
FireEye has dubbed and exposed Iranian cyber espionage group APT39, as actors of a series of attacks on the Middle East. After 5 years of observing its patterns and behaviours, it found links between APT39, Iran and Advanced Persistent Threat (APT) attacks on the telecommunications industry of Saudia Arabia, Iraq, Egypt, Turkey and the UAE. The Middle East suffered attacks on websites of organisations and Domain Name System (DNS) takeovers.
APT
An APT attack is a cyberattack that requires unauthorised access into devices before staying undetected for a prolonged period of time. The hacker monitors and tracks information contained within the device or network and steals information. The main intent is to stay in the network for as long as is needed to take what it requires.
APT 39 and its links to Iran
During observations of APT 39's patterns and behaviours, Kaspersky noticed the group mainly stole personal information. Doing so further develops Iran’s strategies when carrying out cyber attacks. The APT attacks are all deemed part of the country’s information gathering stage. This was different from other Iranian espionage groups. Rather, the groups tend to target government, commercial or intellectual property information. The links between the Group and Iran became more evident as Iran reported more on its intent and need to address its 'enemies' focal tools used. These tools include the media and cyberspace. It appears this is happening as the country expands its presence in cyberspace.
Targeting telecommunications further aligns with this motive as a common place to find the most personal information is within this industry. In addition, it is an access point to the critical infrastructure of communications.
FireEye further linked AP39 trends with APT 34 who are also an Iranian espionage group. Its associated malware includes Powbat and Bonupdater. APT39 too leverages the Powbat backdoor malware.
Carrying out APT attacks
APT Attacks carried out include the use of malware and tools throughout the whole process. It gains entry into devices through phishing mail campaigns, with an attachment containing the Powbat. By exploiting web servers it installs web shells such as Antak and Aspxspy. Once in, APT39 establishes a foothold with Powbat and other backdoors. Through the use of tools such as Mimikatz it escalates privileges on the device gaining control and maintaining its presence. Several tools are used at this stage including xCmdSvc and Remote Desktop Protocol. APT39 then archives stolen personal information with archiving files such as 7-Zip. Kaspersky found 73% of attacks were on vulnerable web-based applications.
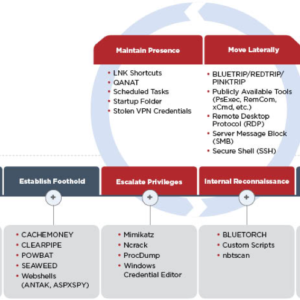
Kaspersky's report illustrates the tools used at various stages of an APT39 attack.
The Group remains active.
Posted from my blog with SteemPress : https://latesthackingnews.com/2019/01/31/iranian-cyber-espionage-group-apt-39-linked-to-middle-east-attacks/