We meet again on homework for the 2nd week of Steemit Crypto Academy. This time I will make a post for the homework of @pelon53. The task this time is to answer several questions that have been given by the professor about Hash and Cryptography.
Explain what does the resistance to collision mean? And what does resistance to preimage mean?
1. Resistance To Collision
Hash has a function where it will make the output generated on a blockchain network system so that there are no similarities and conflicts. As we know that the transaction process that occurs on the blockchain system is very much in time per second, so the output of each transaction must have a different unique code to avoid clashes between transactions that occur.
Each successful transaction will have a unique code that has its own characteristics, and the code for each transaction must be different from each other. This is where the Hash will be used, the hash will make the results of each transaction that occur have different unique codes and have a fairly long code length so that it will make it easier for hashes to create many unique codes at one time.
With this Hash, each transaction will run smoothly without any clashes between transactions because they have different codes.
2. Resistance To Preimage
In addition to reducing the occurrence of collisions between transactions that occur, hashes also have a function to process data so that it is difficult for hackers to learn and hack. Each input that enters will be changed by Hash characteristics so that the output that is already out will be difficult to recognize, even though the content of information between input and output is the same.
This resistance to preimage will minimize crime in the blockchain system. Each output generated is pre-processed by a very complex algorithm so that it will create a code combination that will be very difficult to penetrate and if hackers want to crack the code it will take a very long time.
3. Second preimage resistance
This is the advanced level of security that hashes have, having a second preimage resistance hash ensures that the processed data will have a different code. There is no guarantee that all the code generated by Hash will not experience a collision, so when this collision occurs and the resulting code is the same, then the second preimage resistance will make the output generated cannot be tracked by the input, this will make hash security even more guaranteed even in the event of a collision.
Use tronscan and Etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking.
1. Tronscan
Visit the official page of Tronscan, then scroll down and you will see a column of the latest blocks, then I chose the top block.
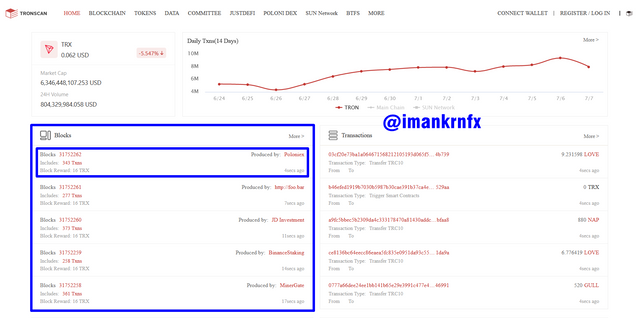
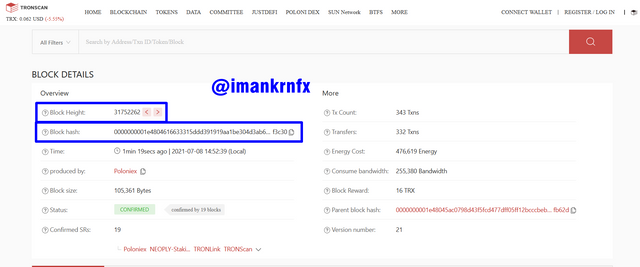
Then we will be taken to the next page that shows the block details. You can see in the blue column below that the Block Height is 31752262 and the Block Hash is 0000000001e4804616633315ddd391919aa1be304d3ab639b4e0638f8bbf3c30.
Then to see the latest transactions, we can look at the start page, then click on the top transaction.
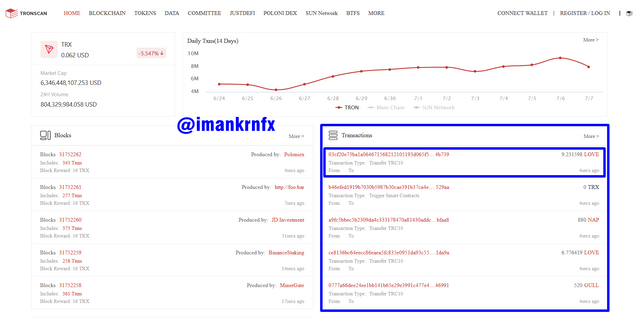
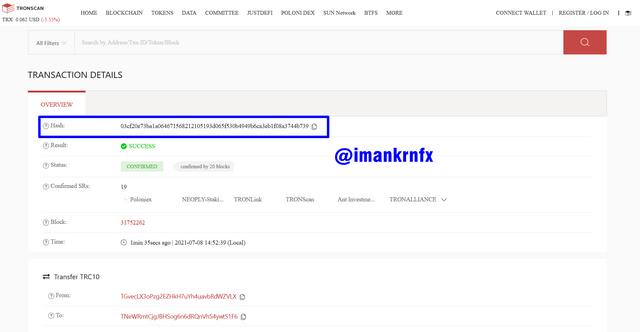
After that we will be taken to another page that shows the transaction details, in the blue column below you can see the Transaction Hash made is 03cf20e73ba1a064671568212105193d065f530b4949b6ca3eb1f08a3744b739.
2. Etherscan
Visit the official page of Etherscan, then scroll down and you will see a column of the latest blocks, then I chose the top block.
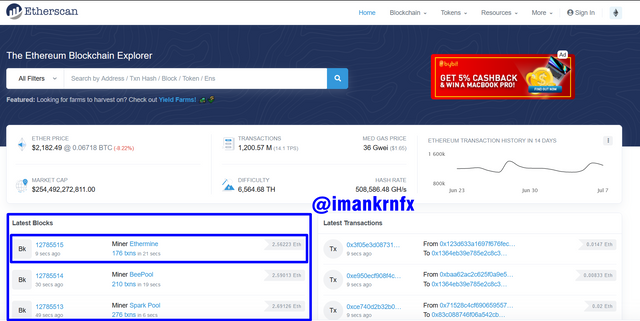
Then we will be taken to the next page that shows the block details. You can see in the blue column below that the Block Height is 12785515.
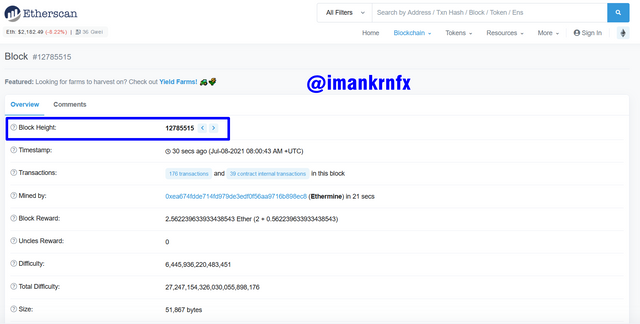
To see the Hash, you just click "Click to see more" then scroll down, then the blue box in the image below shows that the Hash is 0x99875dfc4dbebabc863024d76bc418d1d5d7323b7b1cdc29b1d50f26ad7c17de.
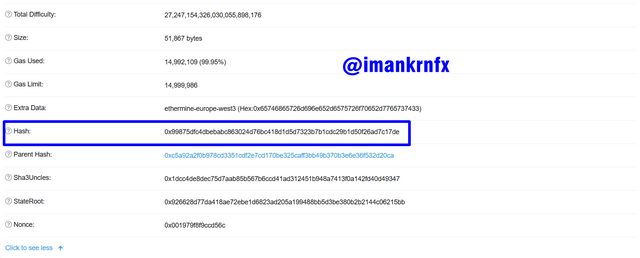
Then to see the latest transactions, we can look at the start page, and select the top transaction.
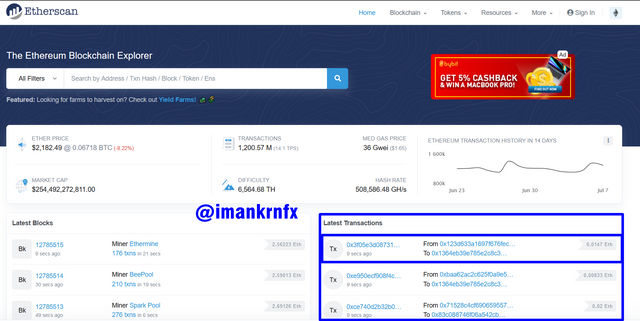
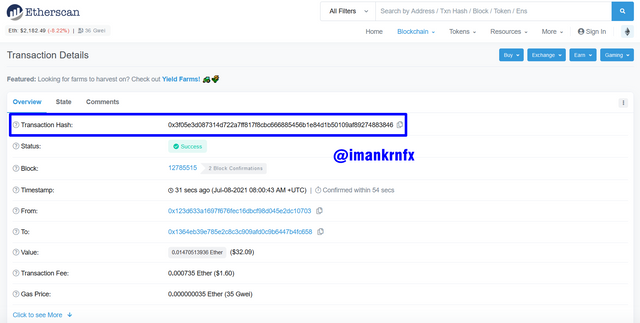
After that we will be taken to another page that shows the transaction details, in the blue column below you can see the Transaction Hash made is 0x3f05e3d087314d722a7ff817f8cbc666885456b1e84d1b50109af89274883846.
Generate the hash using SHA-256, from the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain.
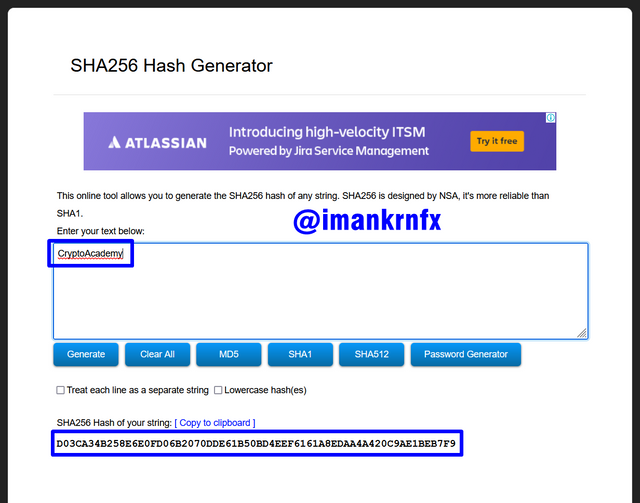
Visit the official page of SHA256 Hash Generator, after that I filled in the column provided with the word "CryptoAcademy" it will be shown at the bottom of the page that the Hash made is D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9.
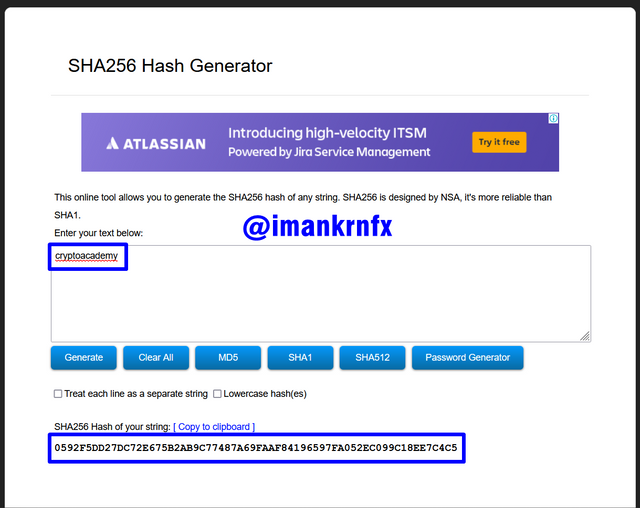
Then I repeated the same but with a different text, this time I entered the words "cryptoacademy" and the Hash result I got was 0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5.
From the example above we can see that hash is an algorithm that has a uniqueness in that it cannot be repeated nor can it be changed. The difference only in the type of capital letters and not capital will change the hash code that will be created.
This also proves to us that the hash will give a different result/output for each input. If we were to do the same thing a second time on the Hash, then we would get a different output code too. All of this aims to improve the security and smoothness of the blockchain system.
In your own words explain the difference between hash and cryptography.
There are several differences between Hash and Cryptography, including:
1. Hash
Works very easily without having to use any additional tools.
The resulting algorithm will be different for each output. So that there will be no conflict between other transactions.
Has a high level of security because it uses a computer algorithm that is very difficult to crack.
Able to make data information invisible and cannot be read easily.
Has a unique and long code which is very difficult for hackers to crack.
2. Cryptography
Requires a tool in the form of software to use it.
Capable of storing a lot of information so that there will be no corruption.
Able to perform encryption and decryption process very easily.
Has a high level of security because the method used is very complex.
Does not require a key for every transaction except decryption.
Conclusion
Hash and cryptography are technologies that were both created to support the Blockchain network system to run smoothly and avoid hacking that often occurs in the cryptocurrency world. With technology, it will create a sense of security for users in transacting on the blockchain network and even more so for people who don't really like all their transactions seen by others, then this hash will be very helpful.
cc: @pelon53
Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
Resistencia a la colisión no fue explicada. Hay resistencia a la colisión cuando hay muy pocas probabilidades que dos entradas choque, es decir, generen un hash idéntico.
No entendí esto 👆. Para cada palabra el hash es el mismo. No hay cambio cada vez que lo hagas.
El hash tiene caracteres fijos, por ejemplo, el SHA-256 tiene 64 caracteres.
Recomendaciones:
Responder cada pregunta de una forma sencilla y que se entienda.
Entender lo que se investiga, para poder hacer tus conceptos correctamente.
Calificación: 8.0
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thank you for the feedback prof.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit