
In Web 2.0 (the traditional Internet), websites acquire the data of their users and send it to centralized Internet companies. From a technical perspective, these companies can treat that data any way they see fit, and it is hard to prevent data leaks, despite the constraints of laws and regulations. For most users, keeping personal data private is a major challenge. Although we regard personal privacy as a major asset, existing infrastructures in cyberspace fail to ensure the safety of such assets. Moreover, when talking about the disruptive applications of Web 3.0 and the transformations it could bring, a major topic is that Web 3.0 can help users fully control their private information.
Although blockchain technology makes data more authentic and transparent, the level of data transparency enabled by blockchain fails to meet Web 3.0 users’ demand in certain scenarios. In the world of Web 3.0, users’ sensitive information, such as transaction/transfer records and on-chain activities, is easily accessible to anyone. Moreover, most Layer 1 public chains now suffer from lack of privacy.
As such, the appearance of privacy-preserving public chains fully meets the demand for privacy protection among Web 3.0 users. These chains provide users with privacy protection solutions, which allow them to selectively hide their sensitive information through technologies such as zero-knowledge proofs (ZKPs) and secure multi-party computation (MPC). Right now, the privacy segment is divided into four categories: privacy coins, privacy-preserving computation networks, privacy-preserving trading networks, and private applications. In particular, privacy coins appeared the earliest, which represents an early attempt to add privacy attributes to crypto. Typical privacy coins include Monero and Zcash. However, right now, a large proportion of privacy-preserving public chains focus on computation networks and trading networks. Speaking of privacy-preserving computation networks, we may think of PlatON and Oasis. As for privacy-preserving trading networks, there are a large number of new public chains, including Aleo, Anoma, and Aztec, among others. As the name implies, a privacy-preserving trading network keeps users’ transactions private and conceals their transaction data, which covers the identity of parties involved, date, amount, etc.
In this article, we will dive into two new public chains that offer privacy-preserving trading networks: Aleo and Aztec.
I. Aleo
- Overview
Positioned as a privacy-preserving Layer 1 public chain, Aleo can now be regarded as a modular zero-knowledge platform for private applications that provides full-stack solutions.
Aleo strives to build a modular, compliant zero-knowledge platform for private applications, creating the ultimate toolkit for private applications. To achieve that, the chain leverages decentralized systems and zero-knowledge cryptography to protect user data on the web. At its core, Aleo offers users and application developers unbounded computation space and absolute privacy. With Aleo, users can access a world of personalized web services without giving up control of their private data. Applications built on Aleo can achieve absolute privacy. More specifically, they help users hide interaction details such as the parties involved, amount, and smart contracts, and will not disclose information unrelated to the present operation.
Team
Members of the Aleo team come from giant companies such as Google, Amazon, and Meta. The team also includes world-class cryptographers, engineers, and designers from celebrated institutions like UC Berkeley, New York University, and Cornell University. Howard Wu, one of the founders of Aleo, graduated from UC Berkeley with bachelor’s degrees in Computer Science and Mathematics. Howard worked as a Software Engineer at Google after graduating with an undergraduate degree, and then returned to UC Berkeley to complete his master’s degree. Since 2014, he has contributed code to crypto wallets, exchanges, ZCash, and Ethereum. In addition, Collin Chin, another member of the team, also graduated from UC Berkeley with a degree in CS and now heads the development of Aleo’s programming language Leo. Besides that, Aleo is backed by a strong lineup of institutional investors, including a16z, SoftBank, Tiger Global, etc.Technology
Aleo uses ZKPs and an optimized version of PoSW, which is a variant of PoW, to avoid massive useless computation under PoW. This not only ensures sound privacy but also solves the problem of performance, which is the biggest challenge facing existing blockchains. According to its test data, the chain’s TPS has reached 10,000, though the actual performance is subject to testing after the mainnet launch. Aleo’s Layer 1 mainly functions as the data layer. Additionally, the network’s execution layer is off-chain, and the validation layer consists of Layer 1 validators on the network, which resembles ETH 2.0.
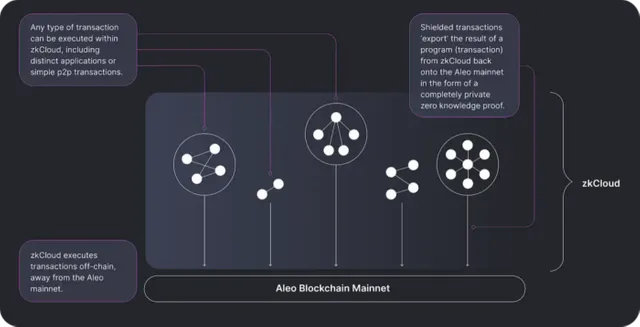
The fundamental technology of Aleo has three components: the ZEXE architecture, the Leo programming language, and zkCloud:
Zero Knowledge Execution (ZEXE): The ZEXE architecture is a specific zero-knowledge proof solution proposed by Aleo. ZEXE conducts offline computations first and then generates online transactions that prove the correctness of the computations without disclosing the details, which means that the transaction can be verified by anyone in a very short period of time. ZEXE also features programmability, allowing users to choose the information to be encrypted and determine the privacy settings.
Leo: Inspired by Rust, Leo is a functional, statically-typed programming language built for writing private applications. It can modularize the zk-snarks settings of the ZEXE consensus protocol, which allows any DApp running on Aleo to use zk-snarks, making app development easier. With Leo, developers can integrate ZKP into various web applications that protect the user’s privacy by making sure that no trace of personal data is left when the app is being used.
zkCloud: Proposed by Aleo, zkCloud is an off-chain, trustless computing environment, where programs are executed privately, securely, and cheaply, and with unlimited runtime. It enables programmatic interactions between shielded identities. Moreover, shielded identities interact directly (as in an asset transfer) or programmatically (through a smart contract). By moving this interaction off-chain, Aleo guarantees privacy and enables greater transaction throughput.
II. Aztec
Overview
Aiming to preserve the privacy of transactions, Aztec Network is a scalable, programmable Layer 2 privacy-preserving protocol based on ZK-Rollup. The network uses a solution called private rollup that’s similar to ZK-Rollup to encrypt and hide users’ confidential transactions. Aztec features two main functions: 1) privacy protection; 2) users can provide programmable contracts through Aztec to build fully private applications.Team
Aztec is headquartered in London, UK. With strong technical capabilities, the core team of Aztec has brought many R&D breakthroughs to Layer 2 on Ethereum. Two of the three co-developers of Plonk, the underlying proof system of the network, are now on the team.
Aztec CEO Zac Williamson has a doctorate in Neutrino Physics from Oxford. He is a former physicist at the European Organization for Nuclear Research (CERN) and T2K Japan. Zac is also the co-creator of Plonk and founder of the Aztec Protocol.
Aztec CPO Joe Andrews graduated from Imperial College London and is the former CTO of Radish, a tech start-up based in Silicon Valley. Joe has rich experience in development.
Chief Scientist Ariel Gabizon has a doctorate in CS from the Weizmann Institute in Israel. He used to be a researcher and engineer at Zcash and is one of the inventors of Plonk.
Institutional investors behind Aztec include Paradigm, IOSG Ventures, Variant Fund, Nascent, Vitalik Buterin, etc.
- Technology
The Aztec team invented Plonk, a general-purpose zk-snark technology, to provide ZKP support for privacy contracts. Users can run programmable privacy protection contracts in Plonk Rollup through Noir, its programming language, and develop applications according to different privacy needs and application scenarios.
Aztec follows an unspent transaction output (UTXO) model similar to that of Bitcoin, and each UTXO is called a Note, which records the changes in the state of each transaction. The note is the basic computation unit in Aztec. The values of a note are all encrypted, and the status of each note is recorded in the note registry. Suppose Alice has a $200 note in her account and transfers $100 to Bob. At this point, the $200 note is split into two $100 notes, one of which is owned by Alice and the other owned by Bob. For an account address, its entire balance is the sum of all UTXOs. Under such a bookkeeping model, whenever a user engages in a transaction, he/she is essentially burning one or multiple notes to generate one or multiple notes with the same value while transferring the ownership of some of the notes.
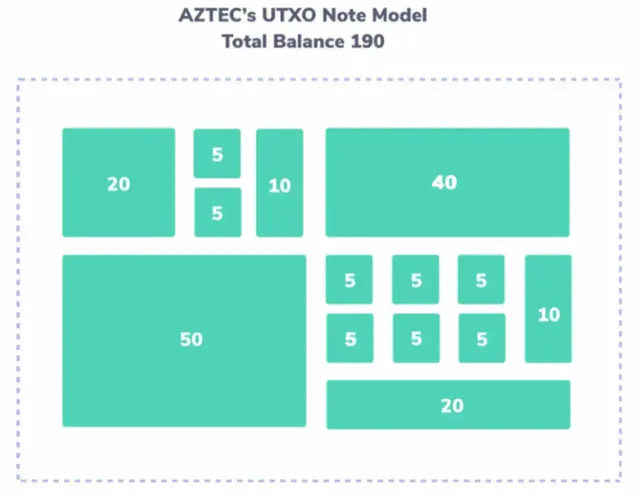
When conducting a transaction, users need to burn notes, generate notes that are of the same value, and then transfer the ownership of the corresponding notes. To conduct such a private transaction, users also have to generate privacy proofs locally. Then, 28 client proofs are aggregated into an “inner” rollup proof, and 32 inner rollup proofs are aggregated into one “outer” rollup proof, which will be eventually verified by nodes and posted onto Layer 1.
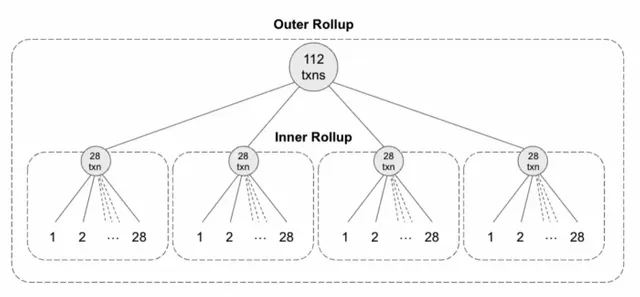
Aztec Protocol has designed a set of development modules to help developers build decentralized applications that ensure confidentiality.
Currently, Aztec offers seven toolkits:
Join Split (Transfer): The Join Split proof allows a set of input notes to be joined or split into a set of output notes and ensures that the sum of the input notes is equal to the sum of the output notes.
Bilateral Swap (Trade): The Bilateral Swap proof allows users to swap notes. This is useful for trading two assets (e.g., trading fiat for bond or collateral). It proves that the makers bid note is equal to the takers ask note and the makers ask note is equal to the takers bid note.
Dividend: This proof allows the prover to prove that the input note is equal to an output note multiplied by a ratio. It is useful for examining whether the interest from an asset is correct.
Mint: The Mint proof allows the supply of Aztec notes to be increased by a trusted party. For instance, a stablecoin mints an Aztec note equal to the value of a bank transfer it receives.
Burn: The Burn proof allows trusted parties to burn Aztec notes. For instance, a stablecoin burns an Aztec note with an equal value of the bank transfer it sends to the note owner.
Private Range: This is used to prove that an Aztec note is greater than another Aztec note, or vice versa.
Public Range: This is used to prove that an Aztec note is greater than a public integer, or vice versa.
Conclusion
The Web 3.0 narrative emphasizes the user’s identity and data ownership. Users must have privacy on the blockchain or network, which turns privacy-preserving computation into an essential requirement of Web 3.0. Blockchains without privacy protection are exposed to many risks. For instance, on such chains, assets are less secure, and operations could be tracked and also face the risk of censorship, making it hard to build and develop commercial applications on blockchains.
If public chains could ensure privacy and achieve programmability, high performance, compatibility, and compliance, then they could be extensively adopted for commercial purposes. As a type of Layer 1 infrastructure, privacy-preserving public chains are competitive players in the category of new public chains and have broad, promising prospects.