
Android users now face another threat from a newly discovered malware campaign. Termed ‘Bouncing Golf’ by the researchers, the new campaign actively targets Android devices, particularly in the Middle East. The campaign infects Android devices with ‘GolfSpy’ malware that executes cyberespionage activities.
Bouncing Golf Malware Campaign Targets Android
Researchers from TrendMicro have unveiled an ongoing malware campaign targeting Android users. The Bouncing Golf campaign is presently targeting ME countries for cyberespionage purposes. The campaign involves infecting the devices with ‘GolfSpy’ malware that pilfers data from the target device and spy on users’ activities.
As elaborated by TrendMicro in their blog post, malware campaign works by maliciously repackaging known apps. These apps are not available on the Google Play Store or any other marketplaces. Rather the campaign markets these apps separately on social media by promoting the website hosting the apps.
Upon reaching the users’ device, the apps deliver malware “AndroidOS_GolfSpy.HRX” that bears cyberespionage capabilities. The malware then collects information from the device and sends it to a C&C server in encrypted form. Moreover, the malware also receives commands from a remote server to execute further actions.
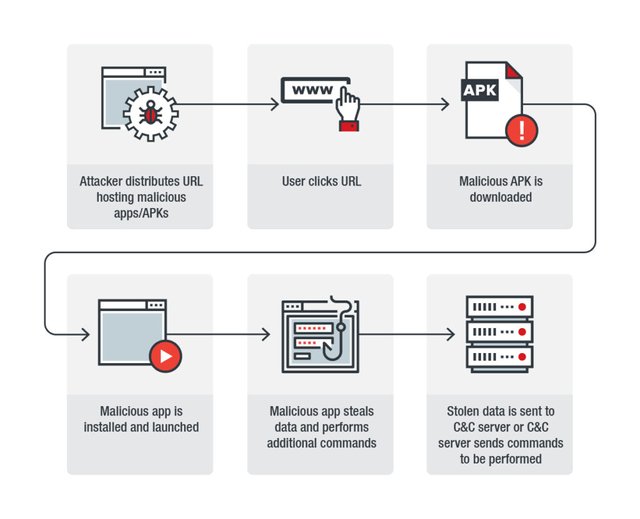
Source: TrendMicro
Describing the working of GolfSpy, the blog stated,
After it is launched, GolfSpy will generate a unique ID for the affected device and then collect its data such as SMS, contact list, location, and accounts in this format: “%,[],time”. The information is written into a file on the device. The attacker can choose the data types to collect, which are written in a certain format.Besides collecting information, the malware also spies on user activities by monitoring and recording phone calls. It also takes users’ photos through the front camera whenever the user wakes the device.
Resemblance With ‘Domestic Kitten’ Campaign
Bouncing Golf malware campaign has repackaged apps various popular apps to infect the devices. TrendMicro found as many as 660 devices infected with GolfSpy. The campaign seemed predominantly active in the Middle East, and it mainly pilfered military-related information from the devices.Tracing back the track of Bouncing Golf was a bit difficult. According to TrendMicro, the attackers have masked their C&C registrant information. Moreover, the C&C server IP addresses also linked to varied locations, including Russia, Holland, Germany, and France.
Nonetheless, the way Bouncing Golf repackages apps, the choice of apps, and the code strings of their decoding algorithm resemble with Domestic Kitten spyware campaign.
As stated in the blog,
The Android malware that both deploy share the same strings of code for their decoding algorithm. The data that Domestic Kitten steals follows a similar format with Bouncing Golf’s, with each type of data having a unique identifying character. It’s also worth noting that both campaigns repackage apps that are commonly used in their target’s countries, such as Telegram, Kik, and Plus messaging apps.While the campaign presently seems focused on ME countries only, the researchers expect it to increase and diversify its distribution.
Let us know your thoughts in the comments.
Posted from my blog with SteemPress : https://latesthackingnews.com/2019/06/23/bouncing-golf-cyberespionage-campaign-hits-android-users-with-golfspy-malware/