The use of APIs, or Application Programming Interfaces, is crucial to the success of digital transformation efforts. Integration and interdependence are gaining significance, making them more crucial than ever. It is therefore of paramount importance to safeguard such APIs. Developers and administrators of applications sometimes overlook the fact that APIs present a growing target for attackers.
What is API Security?
An API is a protocol that allows two programmes to exchange data with each other. Most modern web programmes can't work without application programming interfaces (APIs), yet APIs expose them to greater danger because they allow for external access. Protection of Application Programming Interfaces from attacks is known as API security. Thus, the protection of APIs is a crucial part of the safety of software used online.
API Security Importance With Some Examples
Today's digital ecosystems would collapse without application programming interfaces. They are deeply ingrained in computer programmes and are a major factor in the efficient running of applications. Common client-server programmes also rely on APIs to communicate with one another.
In addition, API manager is frequently used to incorporate APIs into preexisting systems through the consumption of third-party APIs. In addition to the typical client-server or third-party interactions, APIs play a major role in microservices, the most cutting-edge and commonly used application architectural paradigm of today.
Thus, enterprises have little choice but to take on the responsibility of securing APIs to lessen their susceptibility and contribute to an open API economy.
Examples of API Security
Inventorying APIs
As digital transformation projects create new APIs, you must assess their security. By analysing API traffic statistics, an AI engine will find undiscovered APIs. This level of API discovery minimises blind spots. When new APIs are identified this way, a security checklist must be run.
Identifying API Threats
API security detects real-time threats. Real-time threat detection uses an API gateway, WAF, or agent applying validation criteria. Real-time security can only be done sequentially so many times before latency increases.
Out-of-band API traffic analysis should be handled by a separate AI engine. This AI engine can capture API traffic metadata to construct ML models for each API and track error rates, API sequences, API grouping by token, API key, IP address, cookie, etc.
Guidelines for API Safety
For businesses to feel comfortable releasing their APIs to the public, they must adhere to a number of basic security best practises and employ a number of tried-and-true security safeguards.
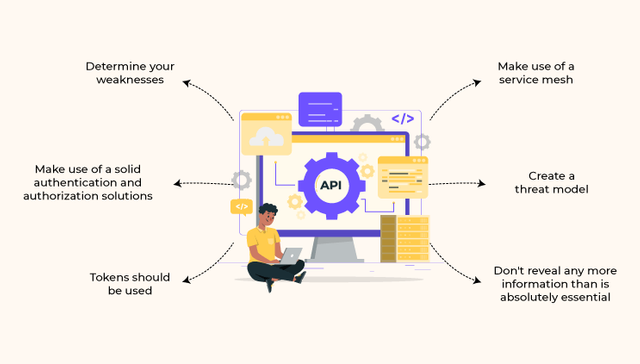
Determine your weaknesses
The only way to properly secure APIs is to be aware of the vulnerable points in the API lifecycle. As the company's reliance on APIs increases, this may become more difficult to implement. All phases of an API's lifecycle, from creation to retirement, must be treated as if they were the product of a software development project in and of themselves. When performing end to end api management, it is crucial to analyse the full API lifetime.
Use strong authentication and authorization
Many public APIs lack authorization and authentication. If you don't enforce authentication or if an authentication factor is easily cracked, hackers can easily attack your APIs. APIs provide access to a company's databases, therefore access must be regulated. Whenever possible, employ proven authentication and authorization systems.
Make use of a service mesh
Service mesh technology transmits requests from one service to another, like API gateways. A service mesh enhances authentication, access control, and other security measures. The service communication layer manages APIs. Service mesh solutions are accessible. If APIs are easier to install, automation and security become more critical.
Summing it up
APIs are the best way to design modern programmes, especially for mobile and IoT devices. While integrating information into a programme from an external source isn't new, some organisations may not yet comprehend the risks of making their APIs public.
Businesses must fight API-targeting assaults including cross-site scripting, injection, and DDoS. Several of these best practises can also assist create and maintain API security standards.
Unified.cc lets you access various apps using a single unified API, saving you time integrating multiple apps and services. Unified.cc makes it easy to connect to various services and data sources, making it ideal for constructing large-scale applications with strong security.