Researchers have spotted another malicious attempt by bad actors to breach iOS users’ privacy. This time, they have discovered an attack scenario involving the iOS URL scheme. They found that exploiting this feature could allow attackers to steal data from other apps and execute other malicious activities.
iOS URL Scheme Vulnerability
According to a recent report from Trend Micro, a new way of targeting iOS users has surfaced online. They have allegedly found the misuse of Apple’s iOS URL scheme. The feature that is supposed to assist apps in communication can let attackers pilfer information from other apps upon an exploit.
As explained in their blog post, Apple employs a dedicated sandbox mechanism for running every application on iOS. This saves the users from massive damages in case of a compromise of an app as it cannot impact other apps.
However, this mechanism creates problems for applications to interact. Thus, Apple addressed this problem by their URL scheme feature, which allows applications to exchange information.
While the feature provides convenience, there lies some problem with it, making it vulnerable to hijacking. When the two apps interact with each other via URL scheme, a malefactor can hijack it to steal data. As highlighted by the researchers,
The URL Schemes function as portals for apps to receive information from other apps… since Apple allows different apps to declare the same URL Scheme, malicious apps can hijack sensitive data of certain apps.To explain the vulnerability, they demonstrated an attack scenario using two Chinese apps: WeChat (messaging app), and Suning (retail application). They explained that signing-in to Suning app via WeChat account generates a URL scheme query from Suning app to WeChat. Upon receiving the query, WeChat requests Login-Token from the server and transmits it to Suning app for verification.
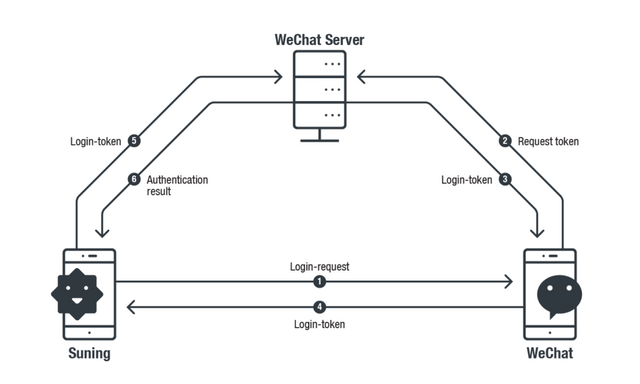
Source: TrendMicro
During this process, WeChat does not validate the login-request source. Whereas, Suning app uses the same Login-Request URL Scheme query every time to request Login-Token from WeChat. Thus, a potential attacker can hijack this URL scheme to request a login-token from WeChat, and then use this data to sign-in Suning app.
Creating Fake Apps For Attack
As explained by the researchers, successful hijacking of a URL scheme requires the attackers to create a fake app. For instance, in the demonstrated example, an attacker could generate a fake WeChat app to which the Suning app would send the login request query. That is also pretty easy.
Capturing it from the Suning app requires creating a whole separate app with WeChat’s URL Scheme (WeChat’s URL Scheme could be found in the field of LSApplicationQueriesSchemesin Info.plist of Suning). With the legitimate WeChat URL Scheme, a fake-WeChat can be crafted and Suning will query the fake one for Login-Token.Here is how the exploit would work.
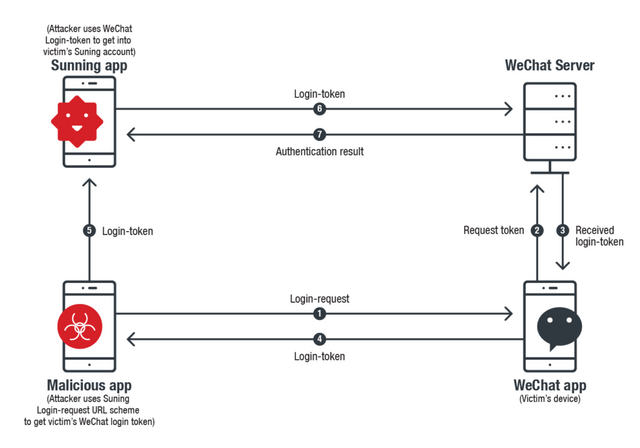
Source: Trend Micro
Whereas, to abuse WeChat, the same fake app would make use of Suning app’s unique URL registered with WeChat to request Login-Token. Owing to the absence of source authentication, WeChat would simply generate the Login-Token in response to the URL.
In this way, both the apps become exposed to the attackers.
The attackers explained that this attack scenario can work with numerous apps. They even gave another example where the victim would pay others’ bills.
This issue is not exclusive to these two apps, the vulnerability exists in many apps that have this particular login feature.Trend Micro found this vulnerability in 2018 and reported the matter to the concerned vendors and Apple. Apple has even notified the developers of this problem and has recommended them using Universal Links for deep linking instead.
Let us know your thoughts in the comments.
Posted from my blog with SteemPress : https://latesthackingnews.com/2019/07/21/misusing-ios-url-scheme-could-allow-attackers-hijack-user-accounts/
Congratulations @twr! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
You can view your badges on your Steem Board and compare to others on the Steem Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!
Vote for @Steemitboard as a witness to get one more award and increased upvotes!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit