We rely extensively on various social media websites for personal as well as professional communication. Facebook even has gone beyond the conventional social media concept to offer features like ‘Facebook at Work’. While using these features we tend to believe that the service providers have made them secure or hack-proof. However in reality securing information systems doesn’t follow a “click’n’go” approach. It is quite possible to have significantly high impact vulnerabilities in these systems even after comprehensive vulnerability assessment stages which they are subjected to prior to moving them to a production environment. It is because of this possibility, a large number of companies offer bug bounty programs. Facebook is one such firm which offers bounties for the bugs users can identify on their platform. The story here is about one such vulnerability, but the sad part is that I couldn’t bag the bounty as another bounty hunter was ahead of me in reporting the same.
Explaining the vulnerability and the exploit would require a recap on SMTP & email communication. SMTP or Simple Mail Transfer Protocol as the name suggests is the standard application layer protocol which defines email transmission. The history of SMTP dates back to 1970's where similar protocols where used in the predecessor of internet - ARPANET. Back in those good old days security wasn’t a concern at all and no security features were embedded in to the protocol. This resulted in SMTP being a protocol which cannot enforce most of the security considerations including Confidentiality, Integrity & Non-repudiation. This inherent vulnerability of the protocol exists even in today’s email communication systems. And as a result, emails can easily be spoofed and sniffed on a network. Further down the line S/MIME was introduced to ensure integrity and confidentiality of emails, however these are not used widely unless in a high priority environment.
Facebook groups are one of the most popular features where people discuss anything under the sun. There have been instances where such discussions have landed people in jail. That being the case, what if I could post something on behalf of you in a Facebook group? Well, the after effect depends on what I post on your behalf, Doesn’t it? Apparently there existed a vulnerability which could let you spoof anyone and post anything to a Facebook group till 18th February, 2016!
Vulnerability Details and Proof
The vulnerability existed in the Facebook Groups’ feature which allowed users to post content to a group via email. For a group with group URL - www.facebook.com/groups/groupname , any member could post to the group by sending an email to [email protected] from the email ID linked to their Facebook account. Without any other validation, facebook accepted the post if the email came from the email address associated with the user’s account.
You could have used any of the numerous fake emailers available in the web which can spoof email addresses to exploit this vulnerability and post to a group on behalf of other users. The Facebook application in this case trusted the input from an inherently vulnerable protocol - SMTP - to authenticate and authorize a user.
The only catch here was that you should be knowing the email address to spoof a user. But there was a way around for this as well. Facebook accepted emails from the facebook email address as well. The Facebook email address of a user with profile URL www.facebook.com/useridentifier is [email protected] and because of this, the entire user base of Facebook was vulnerable to the same attack.
Step 1: Login to Facebook and browse to a group which you want the post to appear. Note down the group identifier from the group URL.
Step 2: Select a member of the group whom you want to spoof. Note down the profile identifier from the profile URL.
Step 3: Open https://emkei.cz/ (or any fake emailer. This can also be done by manipulating the MAIL FROM header of a mail server which allows mail forwarding.)
Step 4: Give the following details and enter the content to be posted in the ‘Text’ field and click ‘Send’
From E-mail: [email protected]
To: [email protected]
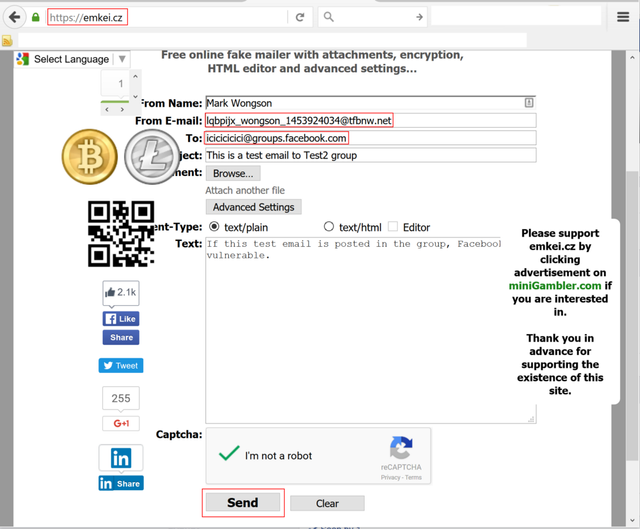
Step 5: It was observed that the text content was successfully posted in the target group by the target user profile!
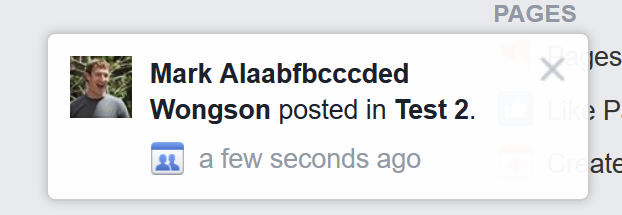
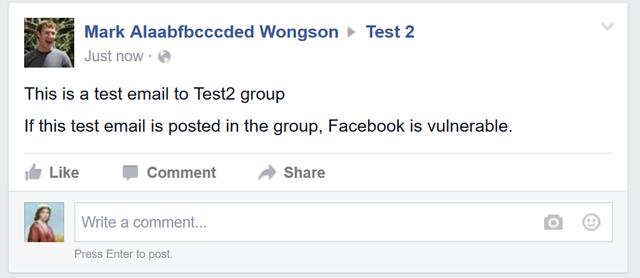
Tadaa, There you go!
The Fix!
After almost two weeks since I reported the vulnerability and they confirmed the same, Facebook mailed me that they have fixed the vulnerability. I initially thought that they would remove the feature altogether, however Facebook’s approach to this issue was different.
After playing around a little with the feature again, I realized that the issue was fixed by validating one of the other e-mail headers, probably the SPF header which gives an idea on whether the mail is being forwarded by a server which is authorized to send mail for the domain. Any spoofing attempt would result in an SPF fail at the spam filter and would be discarded. For Facebook, this is an effective fix as they allow only a handful of emails to be associated with an account based on the reputation and a bunch of other parameters. However this isn’t a fool proof method because an open mail forwarding support on any of the allowed email servers can also result in the same. Looks like at this point facebook considers it as an acceptable risk.
Congratulations @secvibe! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPDownvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @secvibe! You have received a personal award!
Click on the badge to view your Board of Honor.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @secvibe! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit