What is BGP, What Are The Attacks Like Hijacks And How To Mitigate Them?
(Image from: mk.wikipedia.org)
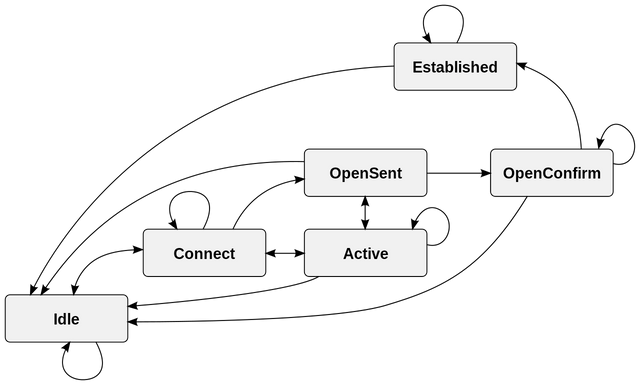
BGP (Broadway Gateway Protocol) is a protocol which will be managing how the data packets are routed across the internet by exchange of the routing and reachability of information across the routers. BGP give directions to the data packets between the autonomous system (AS) the networks managed by a single service provider or an enterprise. Traffic which is routed within the single network is known as internal BGP or iBGP. The BGP which is used to connect the one AS to the other autonomous systems is referred to as external BGP or eBGP.
Why Is BGP Important?
BGP is important since it grows internet on the large scale. The Internet is the basically large group of multi large interconnected networks. Since it is decentralized, there is no governing body or traffic cop which helps the data packets to travel to their intended IP address destinations using best routes.BGP fulfills the role.
What is BGP Used For?
BGP offers stability to the network which guarantees routers will be able to quickly adapt and later send the data packets through another re-connection if one internet path goes down. BGP makes decisions on the basis of the path, rules or network policies created by the network administrator. BGP router maintains a standard routing table which will be used to direct data packets into the transit. This routing table is used in conjunction with another separate routing table know as Routing Information Base (RIB), which is basically a data table stored in the server of the BGP router. The RIB basically consists route information of both the internal and external peers and also continually updates the routing table as the changes occur. BGP uses the client-server topology that is based on the TCP/IP to communicate the routing information, with the client-server initiating a BGP session by sending a request to the server.
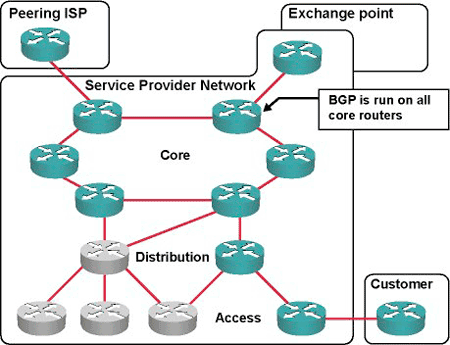
BGP Routing Basics
BGP will be sending the update router table information only when something changes and even later it only sends affected information. BGP also does not have the automatic mechanism, which means the connection between the peers must be set up manually by programming the peer addresses at both ends.
(Image Credit: cdn.ttgtmedia.com)
BGP will be selecting the best path on factors like current reachability, hop counts, and other path characteristics. BGP can also be used to communicate an organization’s own preferences in terms of what the path traffic should be following in and out of its networks. BGP even consists the mechanism for defining the arbitrary tag that are called communities and which can also be used to control the route advertisement behavior by making the mutual agreement between the peers.
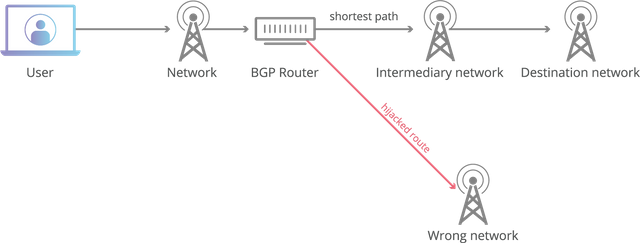
How Can BGP Be Hijacked?
Generally, BGP will be favoring the shortest and more relevant path to the desired IP address. So in order for BGP hijack to take place, the route announcement must be either:
Offering a specific route by announcing a small range of IP addresses other than the ASes which is previously announced.
Offering a shorter route to the certain blocks of the IP addresses. Also, it is not possible for anyone to announce the BGP routes to larger internet. So in order for a BGP hijack to occur, the announcement must be made by the AS operator or the threat actor who will compromise on the AS which is the rare case.
(Image credit: www.noction.com)
It shall be surprising if an operator of large or group of networks will brazenly undertake such activities. But since there are over 80,000 autonomous systems globally it is the case of possibility the some would be untrustworthy. Also detecting BGP hijacking is not easy to detect. Bad actors will try to camouflage their activities behind the other ASes or shall announce the unused block of the IP prefixes which are not noticed in order to stay under the radar.
What Happens When BGP Is Hijacked?
When the BGP Hijack happens the Internet traffic will go wrong way whether it is monitored or intercepted, blackholed or directed to the fake websites like middle-in-the-man-attack. Spammers will be using the legitimate IP addresses for spamming purposes. As per user perspective, page loading time will be increasing because of the requests and responses that don't follow the most efficient network route and may travel all the way across the globe unnecessarily.
So in the best case scenario, the traffic will take long routes unnecessarily, increase the latency. In the worst case scenario, an attacker will be conducting man-in-the-middle-attack or steal credentials directing users to fake websites.
How Can Users And Networks Mitigate Themselves From BGP Hijacking?
Besides constant monitoring how internet traffic is routed, it is very hard for users and networks to prevent BGP hijacks.
IP Prefix Filtering
Most Networks must only accept the IP prefix declarations when necessary and also should declare IP prefixes to only certain networks, not the entire internet. Doing it will help in preventing additional route of hijacking and could keep the AS from accepting all the bogus IP prefix declarations which is practically difficult to implement.
BGP Hijacking Detection
Increase in latency, network performance degradation, misdirected internet traffic are all the possible signs of the BGP hijack. BGP updates will be monitored by many larger networks so that their clients don't face latent issues, and also by few security researchers to do in fact monitor internet traffic and publish their findings.
Making BGP More Secure
BGP was designed to make the internet work and basically, it does that work. However, BGP was not designed with security factors in mind. So more secure routing solutions like BGPsec are being developed for which there is no adoption at yet. So BGP is inherently vulnerable will be so for time being.
Conclusion
BGP is a routing protocol which is designed to solve the certain problems. BGP is also used in managing and exchanging the huge set of the routes within intra and inter-autonomous domains. Recently vendors have implemented new features in BGP and tweaked its performance capability.
Congratulations! Your post has been selected as a daily Steemit truffle! It is listed on rank 10 of all contributions awarded today. You can find the TOP DAILY TRUFFLE PICKS HERE.
I upvoted your contribution because to my mind your post is at least 8 SBD worth and should receive 94 votes. It's now up to the lovely Steemit community to make this come true.
I am
TrufflePig, an Artificial Intelligence Bot that helps minnows and content curators using Machine Learning. If you are curious how I select content, you can find an explanation here!Have a nice day and sincerely yours,

TrufflePigDownvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Your post had been curated by the @buildawhale team and mentioned here:
https://steemit.com/curation/@buildawhale/buildawhale-curation-digest-11-23-18
Keep up the good work and original content, everyone appreciates it!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @fortunex! You received a personal award!
Click here to view your Board of Honor
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @fortunex! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit