Data Utilization vs Consumer Privacy
Walking the tightrope has been challenging for many companies that are using legacy systems. They’re unable to handle consumer privacy issues and control the generated data the right way. They’re also looking towards other companies within the industry to analyze how they are working with data.
Companies should be looking internationally as to how the best practices in consumer privacy are being incorporated. They should work within compliance frameworks and regulations that are designed by government bodies. Additionally, from a complete protection stand-point, the data generated should go back into the research space to create more security-led insights. Historically, these have been the major industries to get hit with data breach attacks.
It's important to communicate the purchase and handling of data in the right way. This is especially true in areas where home security, consumer financial data, and ID information is included. When customers are aware of the risks of hacking, they can better understand what they’re signing up for. They can then choose to trust your corporation based on what you have communicated with them about data handling.
Home security firm ADT faced a similar challenge and addressed it head-on. They developed integrated tools to provide increased clarity to customers who were embedded in their home security system. Using open communication, modeling and best practices in the industry, they're leveraging their data security practice as a strength.
“Every day millions of our customers trust us with what they love and cherish the most, including their privacy. That is why our privacy practices are purposefully designed to ensure we continue earning their well-placed trust. This initiative is part of our ongoing commitment, as the market leader in home security, to implement high standards for our industry, and as we look at the future of technology and access, align our industry around standards and practices that better protect consumers.” - Jim DeVries, President, and CEO, ADT.
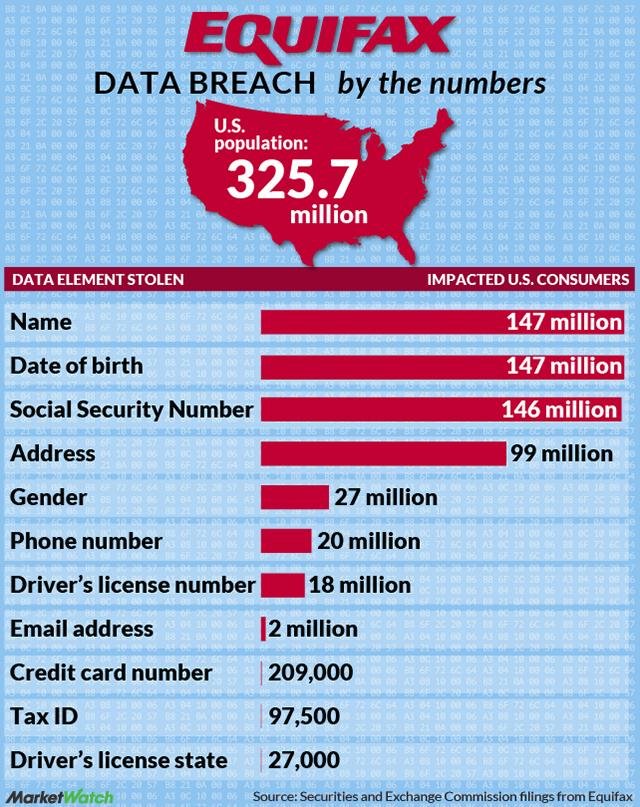
Probably the most excellent example of a data breach has been at Equifax, which was unable to protect the data of a majority of US citizens. It was also unable to effectively communicate the remediation plan that it had set in place. A reference to the data breach is shared below.
From a PR perspective, it is essential that you develop a more comprehensive strategy around communicating the right approach. It’s also important to have a digital and traditional communication strategy that revolves around protecting those that have lost data. It's also about bringing the right factors to provide more information.
From a technical standpoint, it's important to have transparency in lapses and provide a remediation plan for recovering the data. There should also be protection incorporated with stronger firewalls and greater efficiencies in existing security mechanisms.
The responsibilities that come with data ownership
Companies must understand the responsibilities that come with the proper purchase of data. Consumer data is precious and incorporating the right steps is critical. They need to review their technological offerings and create a more evolved cybersecurity strategy.
Here are the following steps that need to be incorporated when understanding data ownership.
Auditing existing security measures
Running an effective red-team should help in streamlining processes better. By running penetration tests, alongside, companies can activate their operations to create more impact. They can design more secure auditing measures that can create an incremental effect. There are also cases where pen-testing is essential to the survival of the brand. An expensive attack can make it more difficult for companies to succeed owing to the public challenges it has to face. That’s why it’s best to do testing early on and ensure that auditing covers much of the scope.Penetration Testing StagesA reference test under the pen-testing best practices is shared above. As we move towards a more connected network, we need to ensure that the data is well protected across the board.
Strengthening security measures
Security measures should also be set in place when it comes to data ownership and security. From technological advancements to policy and control, there are various steps involved in handling data better. There are tools available in the marketplace that are designed to help you remain compliant when it comes to data handling. All compliances including GDPR, PCI, and others are taken care of by the software itself. This makes the process that much more streamlined and all assurances are taken care of.
Empowering employees in the organization
Allowing all employees within the organization is essential. It's necessary to have a clear objective when it comes to employee management, as well as define clear rules as to what employees can work under what domain. This is also consistent with the best practices in handling data that is highly sensitive. It's important to maintain higher quality when dealing with information from across borders as well.
“Recent EU General Data Protection Regulation (GDPR) has led EU organizations as well as those dealing with EU clients to meet compliance requirements. As incompliance lead to data protection regulations can lead to a hefty amount of penalty, organizations are bound to incorporate a range of data protection and regulatory compliance tools.” - Santosh Kumar Research ICT domain.
From a compliance perspective
Employees should be well-trained as to what networks and tools can be used. This is especially true for data-insights driven sectors (finance, marketing, and operations). Additionally, in more sensitive industries, like Healthcare and Medical, employees should be trained to use the right channels to work with data.
Working with third-party vendors is critical as well. However, working with a rightly guarded framework works out best. This is so that there are no leaks that are outside of the organization. Otherwise, an employee may incorrectly share a file or a sensitive piece of information with them. This can then be hacked into by working with the tunnel or the end-point itself.
BYOD and other end-point device strategies should be optimized as well. Compliance measures must be put in place to strengthen the architecture so that the company is more aware of all rules in place. When it comes to bringing your device or using a personal email ID, compliance policies must be put in place the right way.
From a technological perspective
Updating all legacy system is critical. This includes the network, the routers, the information pathways and the channels used for information transfer. Additionally, all areas of network security should be updated as well. From Internet of Things to Artificial Intelligence, all areas of excellence should be used to protect legacy systems.
Encryption should be made standard as well. The core cloud or physical server used to store data should be encrypted and protected from the public networks. This is done to avoid any hackers from gaining access to the system.
Adding a comprehensive dashboard is critical as well. This is done to provide one unified platform wherein all information can be captured. This is also important to note as the compliance department, or the cybersecurity/IT chief can gain access to all insights from one fully-authorized point. A dashboard can also solve multiple problems that we see arising from disconnected systems.
Establishing encouraging business models (Consumer-side)
To encourage customers to share more data with companies, it’s recommended to create a security-first methodology. When customers see companies taking the right measures, they trust the company more. This adds to the overall brand equity built-up. This also aids in hiring the right talent who can then produce better work for the brand. This creates a more security-oriented environment, which brands can then promote to the higher media.
This aura of security is critical to maintaining if customers are to share more information with brands. Otherwise, there is a layer of insecurity supported when data leaks and hacks occur so often. Customers may not want to experiment outside of traditional banks or companies.
This has posed a significant challenge which can be solved with technology and marketing best practices.
Companies can emerge as leaders in the data storage space and create a more compliant environment to walk the tight-rope more effectively. As more companies talk directly with consumers about their security ecosystem, it creates a favorable environment for them to grow.
Conclusion
As technology becomes ubiquitous, there is a greater divide between how companies collect your data and how they manage it. There are also challenges with protecting data against international hackers. This level of exposure is something that is covered under compliance best practices. When companies incorporate compliance measures and technological capabilities, they can walk the tightrope the right way. They can also measure consumer privacy in the right direction and integrate the proper steps necessary.
Utilizing the data is critical as well. This occurs when there is compliance across the board. Data can be used across the corporate processes that relevant in this case, including finance, commercial and customer insights. It makes greater sense to have long-term technological and policy-oriented solutions to help protect customer privacy better.