Edward Snowden spoke at Decrypt's Ethereal Summit, a virtual conference for blockchain investors, technologists, and entrepreneurs.
According to Cheddar News,
Snowden commended so-called "privacy coins" such as Monero and Zcash, which allow for fully anonymous transactions but have struggled to gain legitimacy.
The longer core developers wait to address this, he added, the harder it will be, stressing that leaders in the space need to commit to privacy now, even as they benefit financially from the current system.
"The problem with the cryptocurrency space at the largest scale today is the people who make these decisions have the biggest stake in the system, and the system has benefited from the fact that it has not been regulated out of existence," he said.
In other words, as governments look to regulate cryptocurrencies — a fundamental red line for those who see decentralization as the whole point of alternative digital currencies — there will be an incentive among power brokers in the space, such as crypto-exchanges, to cooperate with new regulatory restrictions, even if they compromise users' privacy.
"The idea of the bitcoin protocol — the peer-to-peer, electronic hash system — is the idea that we can send these payments to anyone permissionlessly," he said. "This is true if it's in your wallet. But how do people fill their wallets? They get it through exchanges, and these guys are imposing permissioning steps that are intermediately to your transaction."
Snowden called for a kind of "purification" that would remove identification information from the cryptocurrency economy.
Edward Snowden Talks Privacy Coins at Ethereal 2021
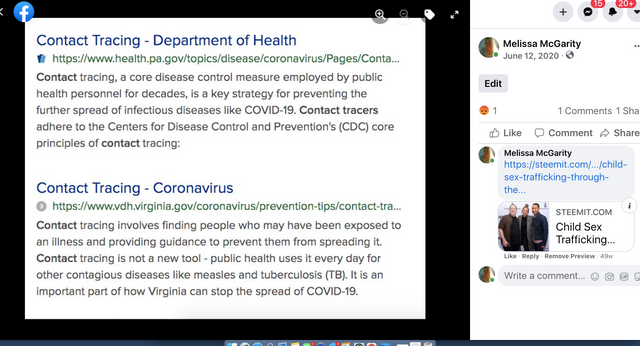
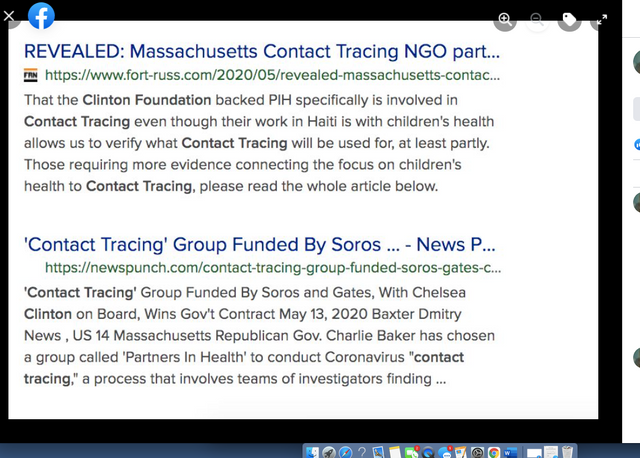
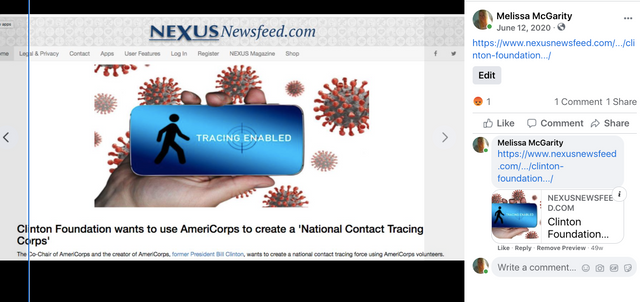
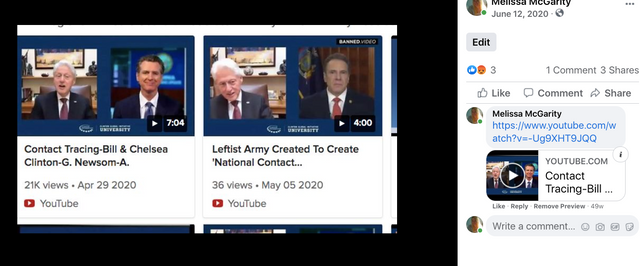
Facebook Frames The Corona Satellites and Contact Tracers
See this inside and far more inside (going to drop just some of the red pills from this facebook frames go to the fb link to see far more),

Coincidence? Are there any coincidences?

What equipment and satellite system was needed in order to track you?
It's Going to be BIBLICAL!
How long before Mathematically Impossible?
Facebook Frames Tunnel just found between Mexico and CA with quite the system and What is the Deal with 3M?
NSA's infrastructure deteriorated in the 1990s as defense budget cuts resulted in maintenance deferrals. On January 24, 2000, NSA headquarters suffered a total network outage for three days caused by an overloaded network. Incoming traffic was successfully stored on agency servers, but it could not be directed and processed.
The agency carried out emergency repairs at a cost of $3 million to get the system running again. (Some incoming traffic was also directed instead to Britain's GCHQ for the time being.) Director Michael Hayden called the outage a "wake-up call" for the need to invest in the agency's infrastructure.
Brian Snow
In 1971 he started working at the NSA. During the 1970s and 1980s he designed cryptographic components and secure systems.
Neal Koblitz and Alfred Menezes have written that Snow was a strong supporter of the transition from RSA to Elliptic Curve Cryptography (ECC) as a public key cryptographic technology:
...ECC started to get strong support from the NSA's Information Assurance Directorate (IAD) during the time when Snow was the technical director and Mike Jacobs was the head of IAD.
It's important to note. . .
IAD (Information Assurance Directorate ) is the defensive arm of the NSA
SIGINT (Signals Intelligence) is the offensive arm
Cybersecurity policy expert Susan Landau attributes the NSA's harmonious collaboration with industry and academia in the selection of the Advanced Encryption Standard (AES) in 2000 — and the Agency's support for the choice of a strong encryption algorithm designed by Europeans rather than by Americans — in part to Snow, who represented the NSA as cochairman of the Technical Working Group for the AES competition.
Why did he allow foreign rather than in country design?
After the terrorist attacks of 11 September 2001, the NSA believed that it had public support for a dramatic expansion of its surveillance activities. According to Koblitz and Menezes, the period when the NSA was a trusted partner with academia and industry in the development of cryptographic standards came to an end when, as part of the change in the NSA in the post-September 11 era, Snow was replaced as Technical Director and could no longer effectively oppose proposed actions by the offensive arm of the NSA:
Who runs "academia" where they charge vast amounts to get their education filled with a Rockefeller Foundation curriculum?
What corporations, foundations, institutes and charities funded by the elite sitting in high places of control like Facebook, Twitter and corporate owned media run and steer Industry?
So Snow was opposing strict standards to keep the United States safe and Not have foreign interference? Interesting how he is touted as a hero by progressives.
In the aftermath of the September 11 attacks, the NSA created new IT systems to deal with the flood of information from new technologies like the Internet and cellphones.
ThinThread, Trailblazer and Turbulence
ThinThread contained advanced data mining capabilities. It also had a "privacy mechanism"; surveillance was stored encrypted; decryption required a warrant. The research done under this program may have contributed to the technology used in later systems.
ThinThread was cancelled when Michael Hayden chose Trailblazer, which did not include ThinThread's privacy system.
ThinThread prototype that protected privacy and Trailblazer awarded contract to develop a program that didn't protect citizen's privacy. Interesting!
Why No Privacy and Whose idea?
The "change in priority" consisted of the decision made by the director of NSA General Michael V. Hayden to go with a concept called Trailblazer, despite the fact that ThinThread was a working prototype that claimed to protect the privacy of U.S. citizens. ThinThread was dismissed and replaced by the Trailblazer Project, which lacked the privacy protections. A consortium led by Science Applications International Corporation was awarded a $280 million contract to develop Trailblazer in 2002.
Trailblazer Project ramped up in 2002 and was worked on by Science Applications International Corporation (SAIC), Boeing, Computer Sciences Corporation, IBM, and Litton Industries.
Some NSA whistleblowers complained internally about major problems surrounding Trailblazer. This led to investigations by Congress and the NSA and DoD Inspectors General. The project was cancelled in early 2004.
A group of former NSA workers—Kirk Wiebe, William Binney, Ed Loomis, and Thomas A. Drake, along with House Intelligence Committee staffer Diane Roark (an expert on the NSA budget)—believed the operational prototype system called ThinThread was a better solution than Trailblazer, which was just a concept on paper at the time.
They reported to the DoD Inspector General office in 2002 about mismanagement and the waste of taxpayer money at the NSA surrounding the Trailblazer program. In 2007 the FBI raided the homes of these people, an evolution of President Bush's crackdown on whistleblowers and "leaks" after the New York Times disclosed a separate program [NSA warrantless surveillance controversy].
Turbulence started in 2005. It was developed in small, inexpensive "test" pieces, rather than one grand plan like Trailblazer. It also included offensive cyber-warfare capabilities, like injecting malware into remote computers.
Turmoil program is NSA’s global passive SIGINT apparatus. TURMOIL is a “high-speed passive collection systems intercept [for] foreign target satellite, microwave, and cable communications as they transit the globe." Presumably all this collection is related to Internet data (DNI), rather than other forms of SIGINT.
NSA collects using TURMOIL through a variety of sources. One of those is the RAMPART-A program, which provides foreign third-party “collection against long-haul international leased communications through special access initiatives with world-wide SIGINT partnerships.
The Internet links that are tapped through RAM-A have “access to over 3 Terabits per second” of data, and “every country code in the world is seen at one or more RAMPART-A collection accesses”.
In other words, friendly communications companies provide access to their backbone links, and those “partners work the fiber projects under the cover of an overt Comsat [communications satellite] effort."
One other specific program that contributes to TURMOIL is the MUSCULAR program, in which the NSA tapped the fiber optic links of Google and Yahoo’s datacenters.
MUSCULAR and another cable-tapping program called INCENSER are part of the WINDSTOP project, rather than RAMPART, access to which occurs through a second party, reported to be GCHQ . There are likely several other cable-tapping programs that contribute to TURMOIL.
A unique aspect of the TURMOIL program is that it operates on the packet level, rather than operating on full sessions. Communications on the Internet, such as an email or webpage, are broken down into tiny pieces called packets when they are transmitted, allowing each small piece of data to take the fastest route possible to its destination.
When all the packets arrive at the destination, they are reassembled and made whole again. This reassembly, and grouping related email messages and webpages, is what the NSA refers to as “sessionized” data, since the data are full sessions rather than broken-down packets.
The massive extent of the NSA's spying, both foreign and domestic, was revealed to the public in a series of detailed disclosures of internal NSA documents beginning in June 2013.
Most of the disclosures were leaked by former NSA contractor Edward Snowden. On 4 September 2020, the NSA's surveillance program was ruled unlawful by the US Court of Appeals.
The court also added that the US intelligence leaders, who publicly defended it, were not telling the truth.
NSA's eavesdropping mission includes radio broadcasting, both from various organizations and individuals, the Internet, telephone calls, and other intercepted forms of communication. Its secure communications mission includes military, diplomatic, and all other sensitive, confidential or secret government communications.
According to a 2010 article in The Washington Post, "[e]very day, collection systems at the National Security Agency intercept and store 1.7 billion e-mails, phone calls and other types of communications. The NSA sorts a fraction of those into 70 separate databases."
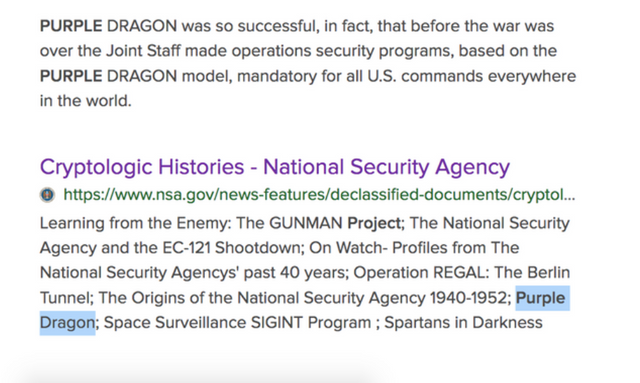
Because of its listening task, NSA/CSS has been heavily involved in cryptanalytic research, continuing the work of predecessor agencies which had broken many World War II codes and ciphers like in Purple, Venona project, and JN-25).
Purple Dragon
Echelon
ECHELON, originally a secret government code name, is a surveillance program (signals intelligence/SIGINT collection and analysis network) operated by the United States with the aid of four other signatory states to the UKUSA Security Agreement: Australia, Canada, New Zealand, and the United Kingdom, also known as the Five Eyes.
By the end of the 20th century, the system referred to as "ECHELON" had evolved beyond its military and diplomatic origins into "a global system for the interception of private and commercial communications" (mass surveillance and industrial espionage).
Former NSA employee Margaret Newsham claims that she worked on the configuration and installation of software that makes up the ECHELON system while employed at Lockheed Martin, from 1974 to 1984 in Sunnyvale, California, in the United States, and in Menwith Hill, England, in the UK.
At that time, according to Newsham, the code name ECHELON was NSA's term for the computer network itself. Lockheed called it P415. The software programs were called SILKWORTH and SIRE.
A satellite named VORTEX intercepted communications. An image available on the internet of a fragment apparently torn from a job description shows Echelon listed along with several other code names.
Britain's The Guardian newspaper summarized the capabilities of the ECHELON system as follows:
A global network of electronic spy stations that can eavesdrop on telephones, faxes and computers. It can even track bank accounts. This information is stored in Echelon computers, which can keep millions of records on individuals. Officially, however, Echelon doesn't exist.
Former NSA analyst Perry Fellwock, under pseudonym Winslow Peck, first blew the whistle on ECHELON to Ramparts in 1972, where he gave commentary revealing a global network of listening posts and his experiences working there. He also included revelations such as the existence of nuclear weapons in Israel in 1972, the widespread involvement of CIA and NSA personnel in drugs and human smuggling, and CIA operatives leading Nationalist Chinese (Taiwan) commandos in burning villages inside PRC borders.
In 1982, James Bamford, investigative journalist and author wrote The Puzzle Palace, an in-depth look inside the workings of the NSA, then a super-secret agency, and the massive eavesdropping operation under the codename "SHAMROCK". The NSA has used many codenames, and SHAMROCK was the codename used for ECHELON prior to 1975.
In 1988, Margaret Newsham, a Lockheed employee under NSA contract, disclosed the ECHELON surveillance system to members of congress. Newsham told a member of the US Congress that the telephone calls of Strom Thurmond, a Republican US senator, were being collected by the NSA. Congressional investigators determined that "targeting of US political figures would not occur by accident, but was designed into the system from the start.
Also in 1988, an article titled "Somebody's Listening", written by investigative journalist Duncan Campbell in the New Statesman, described the signals intelligence gathering activities of a program code-named "ECHELON".
James Bamford describes the system as the software controlling the collection and distribution of civilian telecommunications traffic conveyed using communication satellites, with the collection being undertaken by ground stations located in the footprint of the downlink leg.
A detailed description of ECHELON was provided by the New Zealand journalist Nicky Hager in his 1996 book Secret Power: New Zealand's Role in the International Spy Network.
Two years later, Hager's book was cited by the European Parliament in a report titled "An Appraisal of the Technology of Political Control"
In March 1999, for the first time in history, the Australian government admitted that news reports about the top secret UKUSA Agreement were true. Martin Brady, the director of Australia's Defence Signals Directorate (DSD, now known as Australian Signals Directorate, or ASD) told the Australian broadcasting channel Nine Network that the DSD "does co-operate with counterpart signals intelligence organisations overseas under the UKUSA relationship.
In 2000, James Woolsey, the former Director of the US Central Intelligence Agency, confirmed that US intelligence uses interception systems and keyword searches to monitor European businesses.
Lawmakers in the United States feared that the ECHELON system could be used to monitor US citizens. According to The New York Times, the ECHELON system has been "shrouded in such secrecy that its very existence has been difficult to prove." Critics said the ECHELON system emerged from the Cold War as a "Big Brother without a cause".
They poke you in the eye with shows like Big Brother in their "reality" series.
In July 2000, the Temporary Committee on the ECHELON Interception System was established by the European parliament to investigate the surveillance network. It was chaired by the Portuguese politician Carlos Coelho, who was in charge of supervising investigations throughout 2000 and 2001.
On 5 September 2001, the European parliament voted to accept the report.
The European Parliament stated in its report that the term ECHELON is used in a number of contexts, but that the evidence presented indicates that it was the name for a signals intelligence collection system.
The report concludes that, on the basis of information presented, ECHELON was capable of
interception and content inspection of telephone calls
fax, e-mail and other data traffic globally through the interception of communication bearers including
satellite transmission
public switched telephone networks (which once carried most Internet traffic)
microwave links
Two internal NSA newsletters from January 2011 and July 2012, published as part of the Snowden-revelations by the website The Intercept on 3 August 2015, for the first time confirmed that NSA used the code word ECHELON and provided some details about the scope of the program: ECHELON was part of an umbrella program with the code name FROSTING, which was established by the NSA in 1966 to collect and process data from communications satellites. FROSTING had two sub-programs
TRANSIENT: for intercepting Soviet satellite transmissions
ECHELON: for intercepting Intelsat satellite transmissions
The UKUSA intelligence community was assessed by the European Parliament (EP) in 2000 to include the signals intelligence agencies of each of the member states:
the Government Communications Headquarters of the United Kingdom,
the National Security Agency of the United States,
the Communications Security Establishment of Canada,
the Australian Signals Directorate of Australia, and
the Government Communications Security Bureau of New Zealand.
See more here,
No Such Agency, the good, the bad the ugly! Snowden and reveals. The Echelon of it all! The scope and scale no one thought was even possible!
https://steemit.com/nosuchagency/@artistiquejewels/no-such-agency-the-good-the-bad-the-ugly-snowden-and-reveals-the-echelon-of-it-all-the-scope-and-scale-no-one-thought-was-even
Edward Snowden revealed the surveillance activity of the United States government and those of Fiveyes.
Is it any wonder why the globalists and their corporate owned media have tried to tell the unawake that he is an enemy? He is their enemy for revealing how the globalists and controllers are spying on people.
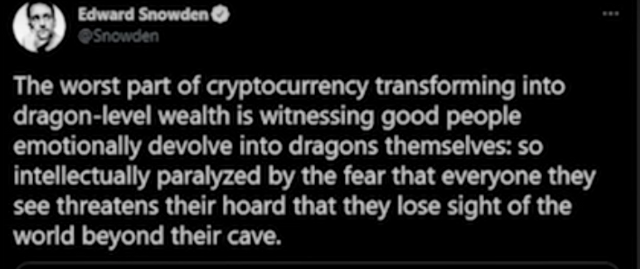
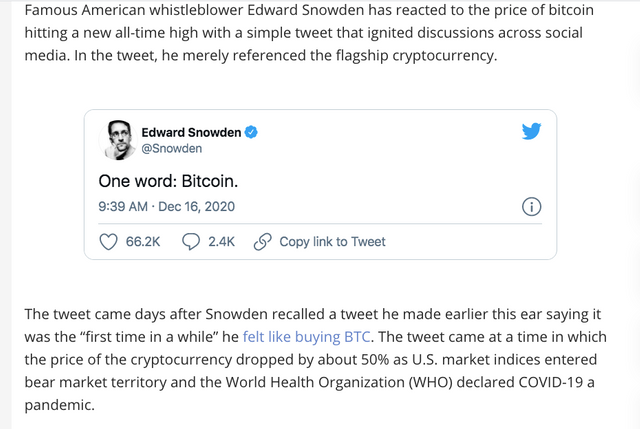
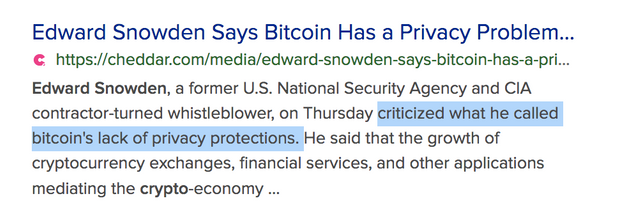
Snowden reveals that bitcoin does not allow for privacy.
From back in December of 2020
Screen Shot 2021-05-23 at 11.03.14 PM.png
https://www.realcryptocurrencyhub.com/edward-snowden-raises-security-concerns-about-bitcoin/
https://cheddar.com/media/edward-snowden-says-bitcoin-has-a-privacy-problem-at-cryptocurrency-summit
Some Key Finds
Found in an article dealing with spying and surveillance Interesting?
Police caught one of the web’s most dangerous paedophiles. Then everything went dark
A trail of clues helped police close in on a dangerous predator. Now, a battle over the future of end-to-end encryption could change the rules of engagement
Police caught one of the webs most dangerous paedophiles. Then everything went dark
GETTY IMAGES / WIRED
TO HIS VICTIMS, David Wilson was a 13-year-old girl. Across a web of fake Facebook, Snapchat and Instagram accounts the 36-year-old used stolen images of young girls to befriend children and gain their trust. Then the abuse started. Wilson would send sexual images of young women and demand his victims, all of them younger than 15, send him photos and videos of themselves in return.
Soon, he turned to blackmail to force children into performing more extreme sexual acts. In some instances he forced his victims to abuse their younger brothers and sisters, some of whom were as young as four. Some of his victims, police were later told, wanted to end their lives.
Between 2016 and 2020, Wilson contacted more than 5,000 children – primarily on Facebook. Around 500 of them are thought to have sent him images or videos. But, with each victim, he left a trail of clues. He was arrested for the first time in April 2015 in relation to two counts of possessing indecent images of children but police could not link him to the crimes and took no action.
Then, in early 2017 Facebook discovered 20 accounts, all belonging to teenage boys, who had been sending indecent images of themselves to an account that appeared to belong to a 13-year-old girl. That August officers from the National Crime Agency (NCA) arrested Wilson again after linking IP address data provided by Facebook to an address in King's Lynn, Norfolk, where he lived with his mother. Police also obtained CCTV footage of Wilson topping up a prepaid phone that they believed was linked to the abuse.
When officers raided the house they found the phone hidden in his bedroom. It contained a small number of illegal images but, crucially, did not contain the network of social media accounts that would have, without doubt, connected Wilson to the widespread sexual abuse of hundreds of children.
It would take another three years – and two more arrests – until investigators were able to gather enough evidence to force Wilson into pleading guilty. On February 10, 2021, a judge at Ipswich Crown Court sentenced him to 25 years. He admitted to 96 sex offences against 52 victims, ranging from four- to fourteen-years-old. The judge called him “extremely dangerous” and a “serial” paedophile, while the officers who had spent hundreds of hours investigating his crimes branded him one of the UK’s most “prolific” child abusers. “He showed very little compassion, even when victims begged him to stop. He just ignored them and carried on,” said Tony Cook, the NCA’s head of child sexual abuse operations.
Wilson’s trail of abuse was relentless. Even as the police closed in on him, and despite the arrests in 2017 and 2018, he kept on offending. And Facebook was his platform of choice. For the police to build their case it was crucial to prove that Wilson had control of the social media accounts linked to the abuse. Officers had tracked him topping up a number of prepaid phones and requested data, through a mutual legal aid treaty, showing the messages in his social media accounts.
In October 2019, police received 250,000 messages showing Wilson’s behaviour. “The content was full of social media accounts, showing the messages and associated friends,” Cook said ahead of Wilson’s sentencing. Investigators painstakingly pieced together Wilson’s activity and even rebuilt a phone that he had flushed down a toilet to gather yet more evidence against him. They eventually linked him to seven false female identities, spread across 14 social media accounts, eight email addresses and five prepaid mobile phone SIM cards. Each revelation came with it a new list of victims who were tracked down and protected.
“The information from Facebook was absolutely crucial to this case,” Cook said. Overall, the company made 90 referrals about Wilson to the US National Center for Missing and Exploited Children (NCMEC), a US non-profit organisation that helps find missing children and collects reports of online exploitation and abuse material. Under US law, technology companies have to report child sexual abuse material they find on their platforms to the NCMEC, although they are not obliged to proactively track down illegal content. The NCMEC then passes tips to law enforcement bodies around the world who investigate and build cases. In the case of Wilson, Facebook provided data about his behaviour, including the IP address of the phone he was using, and the content of his messages.
But the system that allowed Facebook to spot Wilson, and helped police build a case against him, is about to be torn down. Since early 2019 Facebook has been working to add end-to-end encryption to Instagram and Messenger. The move, which is likely to happen in 2022, has reignited the debate around how to balance the importance of individual privacy with protecting the most vulnerable people in society. When the rest of Facebook joins WhatsApp, which turned on end-to-end encryption by default in 2016, the daily communications of billions of people will, law enforcement officials argue, vanish. Investigators in the Wilson case say it’s unlikely he would have been caught if Facebook had already been using end-to-end encryption.
The scale of online child sexual abuse is huge. Year after year, child protection agencies report increases in the amount of abuse found online and say things have got worse as more children have been at home during the pandemic. Last year, the NCMEC received 21.4 million reports of online child sexual abuse material. Across all of the companies that reported content, Facebook accounted for 20.3 million, or almost 95 per cent, of that total.
See more here,
https://www.wired.co.uk/article/whatsapp-encryption-child-abuse

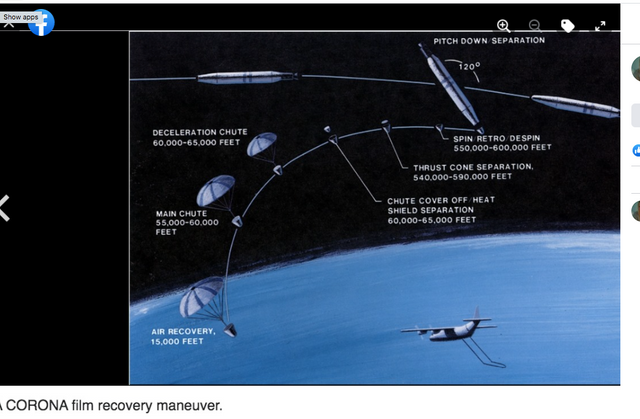
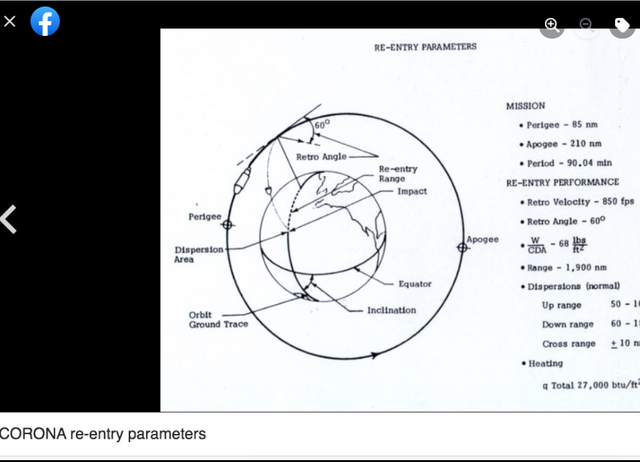
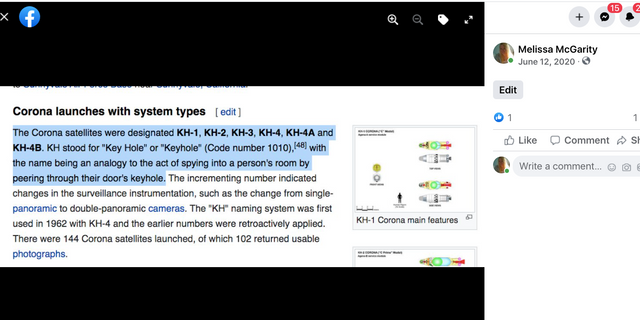
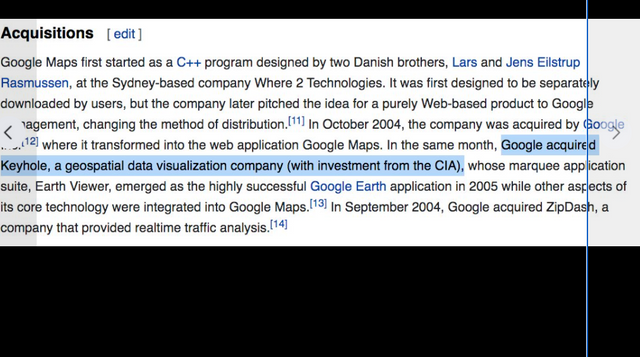
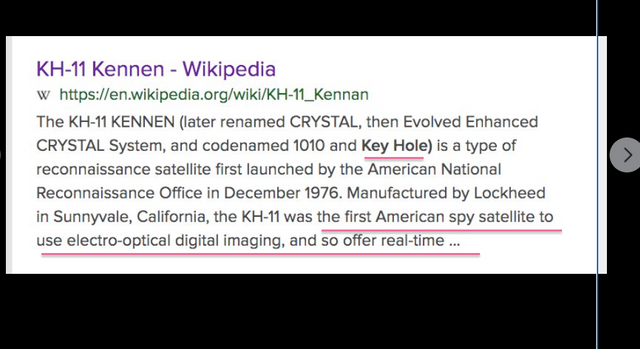
Facebook Frames, Some research on RFID, Satellites and The Corona program. . . a series of American strategic reconnaissance satellites produced and operated by the Central Intelligence Agency Directorate of Science & Technology with substantial assistance from the U.S. Air Force.
Sources and connecting Articles/Reports
https://2009-2017.state.gov/documents/organization/119629.pdf?fbclid=IwAR1fjN-S8IHbwIKHMQL_OhYaHGYFFoEa1lxDJBWmepWLxH4eFnkNAxIfB78
Pentagon Surveilling Americans Without a Warrant, Senator Reveals
From May 13, 2021