Introduction:
Fenix Hash Checker is not only a reliable piece of software, but it also has the capability of comparing two files and determining whether or not they are similar in any way. You may use this approach, for example, to compare two different versions of the same file or to determine whether or not a certain document has been tampered with or altered. In less than a second, the program can determine whether or not two files are identical to one another or if they are separate.

How does it work:
When utilizing the Fenix Hash Checker to verify a file, there are two ways that may be used: either comparing two files next to one other or comparing two hashes adjacent to one another. Following the first activation of the program, you will be given the option of selecting the input for both the base parameter and the comparison parameter, which may either be a file or a hash that was manually entered into the software when it was initially started. The following alternatives are available: picking two files to compare, inputting two hashes, or selecting both a file and a checksum to compare While loading a file into the software, it is conceivable that it will generate a hash of that file using the MD5 technique and compare it to the second value that was generated. It makes no matter what form of input you send to the method as long as it responds soon after receiving your input, which is the case in most cases.
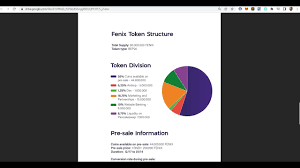
More features of FenixHash:
With the hash function, you can tell whether or not the file has been tampered with and whether or not it has been changed. This is a straightforward, but very effective security solution that is easy to implement. Any change to the file's structure, no matter how minor, can cause a hash calculator to generate an entirely different alphanumeric sequence than it would normally generate. Instead, you may establish whether or not duplicates exist between two files that have distinct names by looking at what is included inside each of the two files in question.
Upon successful file identification, the hash of the files is immediately created in the selected box, enabling you to copy it straight into the clipboard without having to restart the software. To avoid having to type the value in manually, you may copy and paste it from a document or web page into the field if you choose 'Hash' as the input value instead of typing it in.
In the event that a file is correctly identified, a hash of the files is immediately generated and displayed in the selected box, allowing you to copy and paste the hash into another application without having to restart the app. It is possible to save time by choosing 'Hash' as the input value rather than manually entering the value into the field, rather than manually entering the value. If you want to avoid manually entering a value into the box, you may copy and paste the value from a document or web page into the box rather than typing it in manually.
Conclusion:
An incredible number of intelligent people with remarkable experience in their various professions have come together to establish FenixHash, a platform that has arisen as a result of the persistent work of a big number of clever individuals. It has been tested, examined, and tweaked to ensure that it meets the demands of prospective users who have shown an interest in using it. To be successful, any business must first assess whether or not the firm is making an effort to solve a problem, and FenixHash is precisely that kind of organization. The software's user interface and functions are concise and easy to grasp, ensuring that users have a favorable experience when working with it. So we want you to try out FenixHash and spread the word about it to your network of friends and to public forums in which you engage in order to help others while also helping the cause of FenixHash.
#bitcoin #fenixhash
#fenixtoken
••.•´•.•••.•´•.•••.•´•.•••.•´•.••••.•´•.•••.•´•.•••.•´•.•••.•´•.••
About:
Web Link: https://fenixhash.com/
Telegram Link: https://t.me/fenixhash
Twitter Link: https://twitter.com/fenixhash
Whitepaper Link: https://drive.google.com/file/d/1P8tteb_PzlYalyKS6oggW1UQPY3YCS_j/view?usp=sharing
••.•´•.•••.•´•.•••.•´•.•••.•´•.••••.•´•.•••.•´•.•••.•´•.•••.•´•.••
Authors Information:
Bitcointalk Member Profile Name: BitCoinGuy10
Bitcointalk Member Profile: https://bitcointalk.org/index.php?action=profile;u=2248378;sa=summary
Forum POA Link: https://bitcointalk.org/index.php?topic=5381545.msg59120738#msg59120738
Telegram Member Profile Name: @BitCoinGuy10
BSC Wallete Address: 0x3784Ec44d4bf51b9A727e3dC12488cc598Eeb43c