
Bitcoin SV is dealing with a serious problem of double spending, that has been under the radar for some time now. It's zero-confirmation feature, which allows for quick payments, is at the center of this potential disaster. The exploit works around the idea of giving the network nodes the idea that they already processed a transaction.
If a naughty client would send transaction 1 to half of the network and transaction 2 to the other half, the entire network would think it already processed the transaction. This would allow potential harm-doers to double spend their coins. According to documented tests, this can potentially also be executed in real-life scenarios and it's unknown how often double spending is happening already.
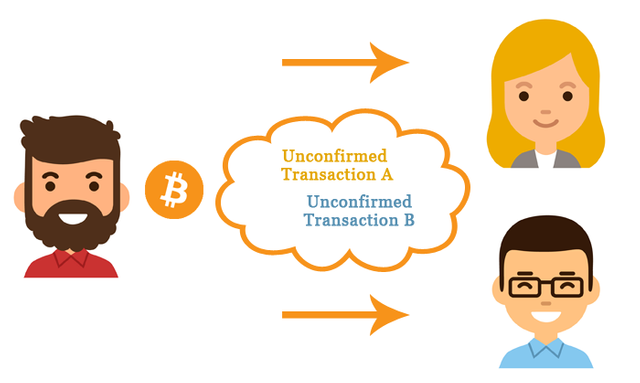
The major problem is that this exploit is not that difficult. The hacker who performed the double spend exploit used his own written software to contact each miner node in the network. This was already possible with 2000 mining nodes for Bitcoin Cash, and is even becoming easier on Bitcoin SV.
Ever since Bitcoin SV forked from Bitcoin Cash late last year, there have been publications addressing the issues of double spending BSV. However, there hasn't been a solution just yet. Yesterday some Twitter users again performed double spending transactions in potentially real-life scenarios.
Bitcoin SV is using the same vulnerability that's in Bitcoin Cash. According to Github user Bordalix he reached a 22% success rate on double spending on the Bitcoin Cash network. The same success rate can be expected on the Bitcoin SV network.
Zero-confirmations is considered one of the main benefits of Bitcoin Cash and Bitcoin SV. Spokesperson and Bitcoin evangelist Craig Steven Wright, often dubbed CSW or Fake Satoshi, always stated that his 0-conf technique in Bitcoin SV is very safe.
Posted from my blog: https://www.nederob.nl/2019/01/07/bitcoin-sv-still-vulnerable-to-double-spending/
Thanks for the info as I didn't know this was possible.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit