Opening Statement//-
Using the Fenix Hash Checker, you can determine whether or not two files are similar in any way by comparing their hashes. This technique must be followed if you want to compare two different versions of the same file. The integrity of a document may also be examined to determine whether or not it has been tampered with or otherwise altered. One piece of software is all that is required for this strategy, which enables the computer to decide in less than a second whether two files are identical to one another or if they are distinct to one another.
How does FenixHash work//-
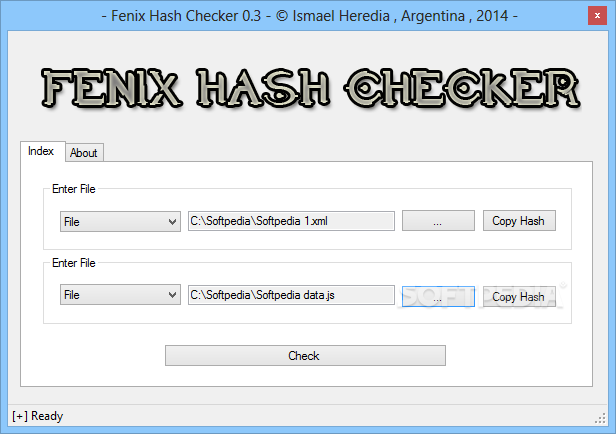
Regarding filing verification, the Fenix Hash Checker has two options: comparing two files together, or comparing two hashes together, respectively. When you run the program, you will be given the option of selecting the input for the base parameter and the comparison parameter, which may either be a file or a hash that has been typed into the software.

Alternatively, you may choose between picking two files, inputting two hashes, or selecting a file and a checksum to compare. In the event that you load a file into the software, it may quickly produce a hash of that file using the MD5 technique and compare it to the second value generated. It makes no difference what form of input you provide as long as the method generates a response as soon as you do so.
With the help of the hash function, you can determine whether or not a file has been tampered with or altered. You can also determine whether or not a file has been tampered with or altered. There has never been a security solution that was so basic, but so effective, and that was also so easy to apply.
It is conceivable that a hash calculator will provide an alphanumeric sequence that is completely different from the one that would be generated normally depending on how little modification is made to the structure of the file. The content of each file in question should be examined if you want to discover whether or not there are duplicates between two files with distinct names that you have in mind.
More about its mechanism of work//-
The hash of the files is instantly generated in the selected box when a file is accurately identified, allowing you to copy the hash to the clipboard without having to restart the program. Rather than manually entering the value into the field, you can save time by selecting 'Hash' as the input value instead. If you want to copy and paste a value from a document or web page into the box rather than manually inputting it, you may do so.
Bringing FenixHash into reality required the arduous efforts of a large number of knowledgeable individuals with considerable experience in their respective professions, all of whom made significant contributions to the project's eventual triumph. The dedication and hard work of a huge number of intellectual persons over a lengthy period of time resulted in the establishment of this platform, which is now in its current form. Several rounds of testing, evaluation, and improvement have been conducted in order to ensure that it meets the demands of future users who have shown an interest in adopting it in the first place.
Final Statement//-
An organization's effort to handle a problem is determined by whether or not the organization is considering potential business partners, which is determined by whether or not the organization is considering potential business partners. FenixHash is an excellent example of this kind of organization, and it meets all of the criteria. Its user interface and functions are clear and simple to understand, ensuring that users have a favorable experience when interacting with the program. Consequently, we would really appreciate it if you would test FenixHash and spread the word about it within your social network as well as in public forums in which you engage, so assisting others while also contributing to the cause of FenixHash. Thanks for taking the time to read this and for taking the time to consider my request.
#bitcoin #fenixhash #fenixtoken
# More Details About Project:
Wеbѕіtе link: https://fenixhash.com/
Twitter: https://twitter.com/fenixhash
Whitepaper link: https://drive.google.com/file/d/1P8tteb_PzlYalyKS6oggW1UQPY3YCS_j/view?usp=sharing
Tеlеgrаm Offісіаl: https://t.me/fenixhash
Author Information:
Forum username: Horraygram
Telegram username: @Horraygram
BCT ACCOUNT LINK: https://bitcointalk.org/index.php?action=profile;u=2306708;sa=summary
Binance Smart Chain Wallet Address: 0x34E5e9749ceB185e29cd239EA631324dD03Bf90A
Proof Of Authentication Link: https://bitcointalk.org/index.php?topic=5381545.msg59314825#msg59314825