The most dangerous extortion virus called WannaCry has been terrorizing computers around the world for the third day, and despite the active opposition from cybersecurity services and antivirus companies, there is still a danger of infection that leads to the encryption of most important files on attacked computers. As has become customary in recent years, extortionists demand for redistribution of user files a ransom in bitcoins.

Why is this virus so widespread? Like all the most famous virus epidemics, he exploited the vulnerability of Windows operating systems: all Microsoft operating systems, up to and including Windows 10, using the old version of the file transfer protocol over the local network (SMB), are affected. This vulnerability, called EternalBlue, was discovered and shut down by Microsoft back in March of this year, but a huge number of users and organizations do not use automatic updates. They were the victims of the attack. In order to prevent infection, it is enough to install the above update. Nevertheless, today there can be another "exacerbation", since many office workers who came to work on Monday turned on their computers and entered the Internet. And not all of these computers are protected.
Chronology of events
Massive infection began on Friday evening - several British clinics reported to him immediately, who were forced to stop work. Later, reports were received from organizations around the world: the automaker Renault, the German railway operator Deutsche Bahn, etc. Information on the number of computers attacked is significantly different, which may be due to different information collection time: according to Kaspersky Lab, more than 45 000 Computers in 74 countries. Avast reports 126,000 victims in 104 countries. According to information from Europol, the victims are even more: more than 200,000 people and organizations in 150 countries have been affected. That is, the epidemic can be considered truly global.
A significant number of attacks occurred in Russia: telecom operators MegaFon and VimpelCom, as well as the Ministry of Internal Affairs and the Ministry of Health, the Investigative Committee and the Ministry of Emergency Situations, RZhD and Sberbank were hit.
Microsoft President Peter Smith blamed the dissemination of information on the vulnerability in Windows to US intelligence services: in his opinion, hackers received it by stealing data from the networks of the NSA and the CIA. Smith even compared the breaking of intelligence servers with the theft of Tomahawk missiles from military arsenals. About the connection WannaCry with the ANB previously stated and the runaway agency employee Edward Snowden.
Attack Results
Despite the scale of the disaster, hackers could not earn much: according to the data for May 14, their address is listed only 6.46 BTC (just over $ 10,000). That is, they were paid only three dozen victims: for unblocking files hackers require $ 300 in bitcoins. Cryptographic viruses are already widely known, and people know that paying, most often, is useless - this does not guarantee obtaining a key for decryption. In addition, many organizations have become more serious about computer security.
An attack of this magnitude demanding ransom in bitcoins can attract undesirable attention of governments and law enforcement agencies to crypto-currencies and lead to another tightening of regulatory measures, although in this case the crypto-currencies acted only as an instrument for obtaining redemption. What is even more strange is that hackers still use bitcoins, although today the increased liquidity of anonymous crypto currency (Monero, Dash, Zcash) allows them to better protect themselves from the attention of special services.
But behind global events, we should not forget that attacks happen and in the world криптовалют.
Poloniex under attack for a week
Against the background of increased market activity in the crypto-currency markets, Poloniex, the largest stock exchange, has undergone a large-scale and prolonged DDOS attack. Although the exchange was able to partly neutralize this problem, many users still report delays related to the execution of transactions and the withdrawal of crypto-currencies. Users complain that their applications for withdrawals hang and even cancel, and Poloniex is slow to admit the problem.
The DDoS attack began on the night of May 9, access to the exchange was limited for several hours. With interruptions it continues to this day, exacerbations were observed on 12 and 13 May. Poloniex notified the issue by posting a post on her Twitter:
"DDoS. We are working on eliminating the problems. "
Although methods aimed at eliminating DDoS were effective, the problems did not end there. Some traders claim that their orders were canceled. In addition, users in the chat complained that the application for input and output does not pass. At the moment, this problem is solved, with the exception of ETC purse and several smaller alcoccons that are on maintenance.
The freezing of accounts, the suspension of withdrawal of funds and the simple extremely negatively affect the reputation of the exchange at such a critical time.
Traders file a class action lawsuit against Poloniex
Claiming about "possible insider trading," one of the traders decided to sue the stock exchange. The visible downward dynamics combined with the numerous constant technical problems at Poloniex led to the fact that many traders lost their marginal positions, especially the large ones were on ETH. One of them claims that he lost about $ 250,000 because of this insanity.
The allegation of insider trading is not so far-fetched, given the additional growth in the cost of bitcoin. The lack of access to the site for several hours on the night of May 9 resulted in the impossibility of canceling orders on the trading platform Poloniex.
The case of traders against Poloniex was taken over by the American law firm Berns Weiss LLP.
At the same time, the Kraken exchange faced similar problems. The Exchange provided a little more information about the situation:
"A large number of orders for the sale of ETH provoked a cascade of liquidations. The sharp decline in liquidity was slowed by the Kraken market price protection system. The mechanism of trade and risk systems functioned as they should. "
According to both exchanges, the lack of full user access was triggered solely by the DDoS attack.
Now is the best time to remind users about the drawbacks of storing large amounts on the exchanges accounts. The best option is to store crypto currency in your wallet on your computer, because in this case no DDoS or downtime will not be able to take your coins from you. If you leave the funds on the stock exchange, they may not be available at the time of panic.
Attack, which was not: little Georgia in the global blockade
And, in conclusion, we will supplement the story with a story with a more prosperous end. However, it is not over yet. Last week we wrote about another spam attack filling the Bitcoin network with a huge number of strange transactions, which actually contained only a commission of miners, as a result of which the mempool of miners continues to grow to record values.
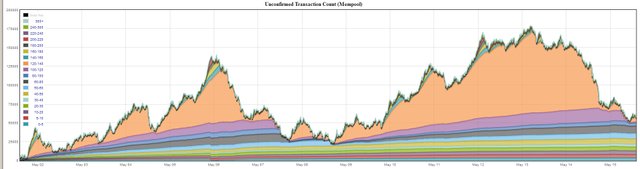
However, users of the forum bits.media found in them and other patterns. Most of these transactions, regardless of the size of the commission, included a Bitfury pool in their units - the largest of the SegWit supporters among Bitcoin miners. In addition, since April 2016, Bitfury has been cooperating with the Georgian government to deploy a state register of real estate on the basis of the blockade. Works on the state register of real estate are supervised by the Minister of Justice of Georgia, Tea Tsulukiani.
The described "spam attacks" on the Bitcoin network began in February 2017 - a month after the active work on the project began. After comparing the hashes of the zero outputs of the "spammer" transactions with the hashes of the documents of the Georgian state register, one of the forum users found that they coincide. After that, the situation cleared up: Bitfury periodically uploads new registry entries into the block (one document - one transaction), and later confirms them in the blockroom. This is the reason for the periodic "roll-out" of several thousand transactions into the blockade from about a dozen addresses.
Thus, small Georgia with its real estate register occupies a very important place in the global blockade of Bitcoin. This proves once again how much the Bitcoin network needs to improve its scaling - after all, nobody can use it as such. A few more similar projects, and the network bandwidth will be guaranteed to be exceeded. Interestingly, solutions like the Lightning Network will not solve the problem in any way, since all transactions of the state register require confirmation through the blocking system separately, and not only "aggregating" the turnover in the transaction channel.
It is not entirely clear why Bitfury chose to select Bitcoin, rather than any Altkokin, for its registry, or did not create its own. Even if it is the most secure and invariable hashes of documents, it is guaranteed better in it, but the placement of transactions in Bitcoin's locker requires costs (since some of the transactions are confirmed by other pools) and much more time for confirmation. In addition, its own blocking or sidechain would allow the company to adjust the rules for placing documents in accordance with the requirements of the customer, and even adjust them if necessary, while Bitcoin's lock-ups will always have to follow a general consensus.
If the Georgian experiment proves successful, this will serve as an additional incentive for the emergence of specially designed blockhouses designed exclusively for the maintenance of state and corporate registries - not only real estate, but also any objects where the main requirement is the reliability of storage and guarantee of unchanged records. For example, a similar solution is already being tested in the UK.
What is a crypto currency and how does it work? How to earn it? Why Onecoin? All answers can be found here. The most profitable investments in MLM More: http://onecoinsign.com
Get a mac, and file vault your shit...
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit