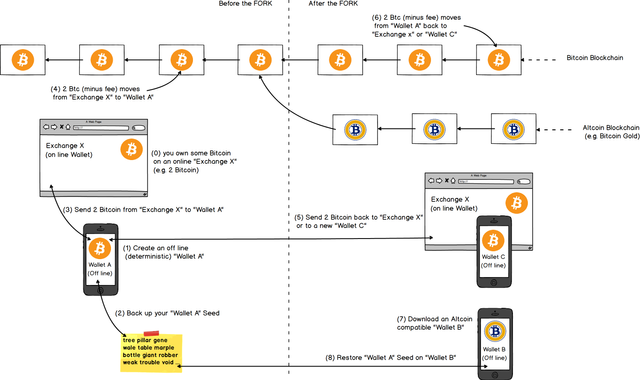
I tried to "ikea"-lize the standard - and very simple - schema of steps you should follow to exploit and Hard Fork on the Bitcoin Blockchain.
This should be valid also for other trustless/public blockchains, as long they will be subject to hard forking.
I tried to put all the explanations directly inside the schema, of course feel free to correct/integrate if needed.
Cheers
QdM