This article mainly explain the third type of fraudulent methods, Theft. There are mainly four types of Theft listed below.
- Trading account theft
Similar to the aforementioned fake Binance exchange website, this fraudulent method induces users to log in to fake exchange websites and steals the users’ accounts and passwords.
- Wallet account theft
Since the beginning of this year, researchers from SecurityScorecard discovered two botnets that are respectively driven by the ZeusPanda and Ramnit malware families, which mainly target the Coinbase.com and Blockchain.info cryptocurrency wallets.
It should be noted that when a user visits a website that is infected with this malware, the malware can detect the user’s access activities and silently inject the obfuscated malicious code in the background, and then modify the content displayed on the target page.
If the target site is Coinbase, the malicious script invalidates the entry fields of email address and password on the original site and creates a new malicious button and then superimposes it on the “Log in” button. In this way, when the user enters the login credential and presses the “Submit” button, the user believes that he or she has completed login when actually his or her credential information will be sent to the server controlled by the attacker. In fact, the malware also pretends that the login is restricted and requires the user to further complete two-factor authentication:
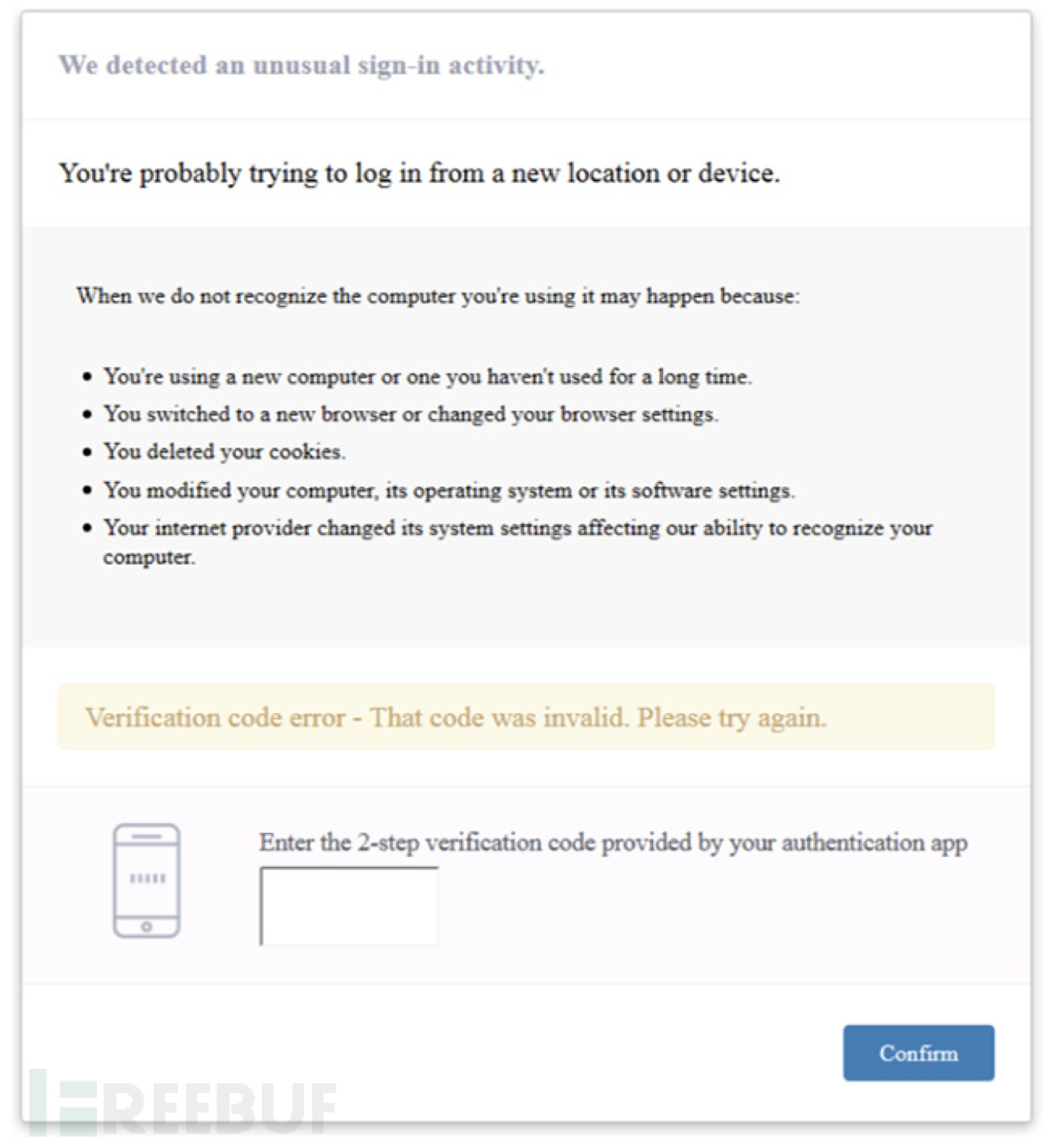
After obtaining the user’s credential data, the attacker can use the data to access the user’s account and modify certain security settings to facilitate subsequent fraudulent transactions.
3.Direct private key theft
The CryptoShuffler virus, with activity peaking in June 2017, can monitor users’ clipboards and match and replace the data stored in the clipboards in real time (the matching algorithm uses regular matching). When an investor makes a donation or transaction, the target wallet address stored in the clipboard will be replaced with the wallet address set by the attacker.
- Wallet address replacement
Claymore Miner is a popular multi-coin mining app, which hosts many devices on the Internet. The Windows version of Claymore Miner provides remote monitoring and management features on port 3333 through the EthMan.exe file under the “Remote management” subdirectory. Botnets can infiltrate other existing Claymore Miner mining devices on the Internet, attack management port 3333, replace the wallet address, and steal the computing power of these victim mining devices and their corresponding ETH tokens.
Above is a summary of Theft, the following suggestions are provided for investors to reduce the probability of being defrauded:
Improve the awareness of fraud prevention by not transferring money to any strangers or unknown addresses to avoid great losses for small gains.
Choose the most secure wallet to manage your digital assets.
SafeWallet, which is a trustworthy wallet with high security.
1)When your wallet is opened, it initiates a security scan to detect viruses in time avoiding asset loss.
2)SafeWallet provides a blacklist address database and checks if the target transfer address is authenticated during funds transfer with a prompt.
3)The wallet provides a complete defense system against potential attacks.
About us
Telegram: https://t.me/safewalletgroup
Official Website:https://www.cmcmbc.com
Twitter:https://twitter.com/safewallethelp
Youtube:https://www.youtube.com/channel/UCGgAmQhnx6ijeqnDaPKL3Rw