
With every day passing our dependence on internet is increasing. Today the world is way more interconnected and internet dependent as compared to the previous few years. This interconnectivity is increasing exponentially day by day.
We have witnessed so many benefits from interconnectivity of today. We can access nearly anything digital from corner of the world and deliver it to another corner of the world. The interconnectivity the internet has brought makes it possible to attain and deliver the prosperity needed to resolve the world’s key problems. But not everything is rosy.
This increased interconnectivity is increasing the vulnerability of private online data and therefore the need to secure valuable personal data is also becoming increasingly important.
The unrestricted flow of content between numerous online channels has put both the organizations and individual users at a risk of cyber hacking and other fraudulent attacks. Every year, millions of attacks occur on online data storage resulting in the loss of valuable personal records. The cost of this is damages to both the consumers and corporations. Each cyber attack forces companies to cut operations for a period of time, a need to renew security, and to pay off the liabilities incurred by people’s lawsuits. People, on the other hand, face a drastic threat from the potential identity theft and sale of private data that the hackers could cause.
Cyberattacks are not limited to any specific region or industry. Such attacks are expanding the reach to every corner of the world and no industry including cryptocurrency assets and exchanges are immune to the cyber hacking. While blockchain institutions prize themselves as the purveyors of a future reserved for a secure digital environment, the funds and exchanges that are involved in this technology are often breached; the reason is that they are a prime target.
In the last one year alone, several cryptocurrency funds were subject to the criminal online attacks and the assets worth hundreds of millions were at risk. These attacks exposed the vulnerability of cryptocurrency trade and highlighted the need of cybersecurity which is now considered a top priority within the industry.

People have to be very alert in order to combat the cybersecurity threats and therefore must protect their valuable private data flowing across different channels which include emails, websites, cryptocurrency exchanges and mobile devices. However, this whole mechanism of shielding the private data from all kinds of cyber attacks is not so simple. There are countless security solutions available in the market but to implement and manage all these security solutions can be very difficult and complicated. This complexity discourages the users from adopting the full-scale cybersecurity measures.
Major problems in combating Cybersecurity threats
The interconnectivity is growing at an enormous pace and the vulnerability to cyber threats is obviously growing at the same pace but our traditional methods of combating the threats are lagging the required capacity. The cybersecurity market requires a revolutionary innovation with the main focus on efficiency, transparency and the mutual trust. A complete overhaul is required to sort out the issues and problems faced by the individual users and organizations operating within the industry.
 Market Saturation with a flood of Security Solutions
Market Saturation with a flood of Security Solutions
The users across the board are wary of security threats which has created an urgent requirement of security solutions but this urgency has created an oversaturation of market with an unlimited number of security solutions. This oversaturation is confusing and making it much difficult for the users to pick the right solution that meets their requirement.

The information provided by the vendors is misleading and merely focused on profit making. The users have to depend upon their own gut feeling to select a solution that may or may not be proper for their device. Furthermore, using multiple security solutions at a time could be very complicated to maintain because each system requires different software and setting configuration. As a matter of fact, multilayer security solutions concept is outdated and is proven inefficient. It may enhance the threat rather than combating the threats as the users must always be familiar with the multiple software upgrades and maintenance.
 Non-availability of Threat Intelligence data due to Centralization policy
Non-availability of Threat Intelligence data due to Centralization policy
This is another very important issue faced by the users within information security industry. The threat intelligence data lacks transparency and is not available to the individual users.
he cybersecurity sellers while providing the security services to end users are able to collect valuable data concerning the emerging security threats which include all kinds of attack patterns, suspicious IP addresses and other related information but this important data remains within the service providing companies and is not shared with the users.
The security service providers use this information for their commercial benefits and the users who help in generating this data are left with zero compensation rather they keep paying for the services which depend heavily on the data provided by them. It’s now time that this unfair centralization of such a valuable data must end and the compensation should be distributed fairly among the end users.
 Questionable security solutions
Questionable security solutions
This is perhaps the most important concern which creates doubts about the performance of security solutions available in the market. The problem stems from the nature of current market structure which is flooded with unlimited types of security solutions and no one is able to identify the right security system with complete surety.

The only way a user can assess the performance of a security system is by actually testing the product which is a very cumbersome and costly practice. The big corporations can afford to deploy resources and time in this practice but this is not feasible for small users. Therefore, only large-scale corporations can take advantage of full spectrum of multilayer security solutions.
The cybersecurity providers use different means of advertisement to promote their products but as a matter of fact majority of them are not properly familiar with the nature of threats and the industry requirements. It has been observed that some of fraudulent vendors are hiding behind ICOs and the individual users get in their trap.
The ultimate Cybersecurity Solutions by Cloudbric
The cryptocurrency market is losing hundreds of millions of US dollars every year as a result of security breaches and cyber-attacks. Cloubric platform has provided the most innovative cybersecurity solutions in order to protect the internet and blockchain industry on the whole from all kinds of security threats.
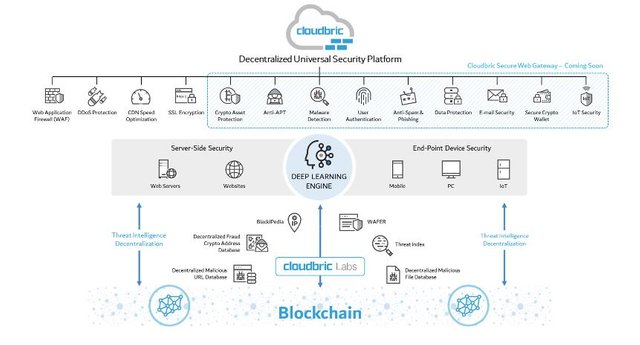
The Cloudbric Universal Security Platform has made the information security much easier by making it accessible to the individual users all over the world hence making the blockchain industry safer than ever before. The Cloudbric security platform is equipped with deep learning mechanism using Artificial Intelligence and comes with ready to use cybersecurity solutions.
Here's a FAQ to quickly get acquainted with the answers of some common queries.
Basic Features of Cloudbric Universal Security Platform
 Cloudbic is equipped with a deep learning mechanism which is known as VISION and provides early threat detection in relation to different end user devices and protocols.
Cloudbic is equipped with a deep learning mechanism which is known as VISION and provides early threat detection in relation to different end user devices and protocols.
 The Cloudbric Security Application is an automatic system that continuously receives real time security data and protects the users from malicious URLs, viruses and other scams on the internet.
The Cloudbric Security Application is an automatic system that continuously receives real time security data and protects the users from malicious URLs, viruses and other scams on the internet.
 Cloudbric offers the largest Decentralized Threat Database which is continuously fed to the VISION collected from thousands of network members and a number of enterprise partners all over the world hence making it the most trustworthy and accurate security solution.
Cloudbric offers the largest Decentralized Threat Database which is continuously fed to the VISION collected from thousands of network members and a number of enterprise partners all over the world hence making it the most trustworthy and accurate security solution.
 Cloudbric also offers crypto asset protection in a number of ways such as protection against false project websites.
Cloudbric also offers crypto asset protection in a number of ways such as protection against false project websites.
Here's a look at more details into the project's functionality.
Security & Compensation
This is the hallmark of Cloudbric Universal Security Platform, the users get rewarded by using any of the solutions provided by the platform. The concept is very simple, by utilizing any of the platform’s security solutions the user will automatically generate an individual threat log which helps VISION, an innovative and revolutionary AI, to detect and learn new attack behaviors. By doing so the user will be contributing fresh data to Cloudbric’s decentralized database and will be adding its participation to ever growing network hence the Cloudbric platform will reward the user with CLB Tokens.
Here's a deeper look at CLB tokens.

The contribution phenomenon is mostly effortless and as simple as normal web browsing. The reward distribution goes on increasing with the number of devices connected and also the number of email addresses secured with Cloudbric.
In short words, Cloudbric Universal Security Platform has changed the landscape of Cybersecurity market by introducing the most innovative and accurate solutions to protect the users from all kinds of cyber threats.
Going beyond the present benefits Cloudbric provides, it’s important to note that this development is future proof as the technology is tailored to service the future of internet and blockchain.
Blockchain, IoT, and AI
Cloudbric exceeds the abilities of centralized security providers because it gets access to a lot of data. This data allows Cloudbric to have the best AI advancement in the security industry. Blockchain is growing and its uses are spouting every day.
Cloudbric is designed to do more than just protect exchanges and wallets, or just funds and investors. Cloudbric is being developed with the goal of protecting everything that comes out of the world’s innovative minds. VISION will advance and have the protection solutions ready. A great example of upcoming innovations are the merger of blockchain and IoT.
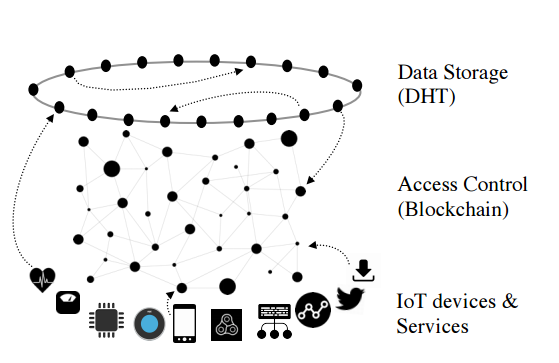
As projects like MIOTA became more prevalent in their reach, digitalized value transfers will become then norm in machines. The internet will be the medium of not just people’s communication, but everything’s communication. That would is our future and Cloudbric is designing the technology to protect our future.
Vision is the result of collaborative efforts from major cyber security experts and the scholars from major educational institutes.

Qualified Team
Of course, claiming to be future ready is meaningless as anyone can do that. But Cloudbric has established products from an existing company and that makes Cloudbric one of the very few projects in cryptocurrency market that has an MVP and is being made by an existing company. This was initially an in-house development of Penta Security Systems, Inc. The company's executives have decades of combined experience in cyber security. They have already provided the initial tools as a testament to deliver, and they certainly have the track record and experience to go the full way and push Cloudbric to reach its full potential.
Get to know Cloudbric's exceptional team.
Cloudbric faces some major benefits as a blockchain project being developed with the support an established company. Cloudbric will be able to access Penta Security's network and will be able to benefit from the established brand recognition of Penta.

As the above awards show, Penta's success is not a baseless assertion but a well-supported claim. The company has faced constant recognition for its developments. Here's a look at details of project road map and achievements.
The direct benefit of this recognition has been Cloudbric's ability to attract a lot of interest in its pre-sale rounds. While several projects have failed to reach even the soft cats of their pre-sales, Cloudbric is on its way to a public sale after both pre-sales sold out. while such a performance is always impressive, doing so in a bear market is a milestone worthy of praise.
Praise certainly has come, and that too from the biggest names in cryptocurrency. Major funds, projects, and exchanges held a yacht party to host a private fund-raising round for Cloudbric. The event was attended by the likes of Node Capital and Tron Foundation. In fact, Cloudbric has a partners list that even established blockchain projects would envy.

It's quite clear that reverse ICO catch attention from major market players. Cloudbric is not experimenting with a whitepaper. It is a revolutionary project from a well-experienced team and it has the network of a leading cyber security company, which is Cloudbric's target market.
While most ICOs are managed by novice market players and early challenges, Cloudbric is on its way to a record start as it already has the market interest needed to kick off with an explosive momentum.
Conclusion
Cloudbric is taking on the existing cybersecurity companies by creating a decentralized cybersecurity network. Centralized institutes simply cannot get threat data as well as the whole world can if it works together. Cloudbric has set a great incentive system and people who join its network won’t just get security, they will also get CLB tokens.

This new model of cybersecurity is sustainable and agile enough to make the web and blockchain interactions safer for everyone. Innovations like this are needed.
Cloudbric’s token sale goes live on 10/22 and the sale has no minimum for participation. This makes it accessible to everyone, just as it should be as CLB tokens are meant to be a community supporting feature of Cloudbric.
KYC is now open and you can learn more about the project through the following links:
The company has provided a quick guide on clearing the KyC process. Begin KYC Registration here.
Website: https://www.cloudbric.io/
Whitepaper: https://ico.cloudbric.io/upload/file/Cloudbric_Whitepaper_EN.pdf
Bitcointalk Thread: https://bitcointalk.org/index.php?topic=4376899.0
Telegram: https://t.me/cloudbric
Twitter: https://twitter.com/cloudbric
Facebook: https://www.facebook.com/cloudbric
Blog: https://medium.com/@cloudbric/
E-mail: [email protected]
Proof of Work for https://bitcointalk.org/index.php?action=profile;u=1887821
With so much at stake it's going to be tough to keep people out. The technical details are over my head but if your right here then the tokens are well worth a look.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
It's addressing very important issues.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Having been hacked myself and had several of my cryptocurrencies stolen I realise the importance of cybersecurity. As we become a more digitally dependent society physical money isn't as practical as it once was and while digital money has its benefits its still easier to steal than physical money.
People are pretty lax with their own digital security and finding solutions you can trust is a research tasks no one really wants to do, until they get hacked. Its nice to see more projects focusing on the secuirty of cryptocurrency as its been plauged for so long with hackers, phishers and thieves
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Sad to hear that.
We really need better cyber security tools.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Sad to hear that. We
Really need better cyber
Security tools.
- stazhao
I'm a bot. I detect haiku.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
This is awesome!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
hi @chekohler,
have you been hacked? damn. how did it happend?
Im so far very lucky and nothing ever happend to me.
Yours, Piotr
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
That is lucky Piotr. Even if we try our best, hackers can be hard to keep at bay.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Yes I did, it was a few months ago and the 2FA didnt work on the website. I wrote two posts about it. You can find it here. I learned the hard way and im better for it and take security seriously
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Still pretty sad to hear this. I try my best to always use the 2FA whenever possible.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks man, yeah it was a very expensive lesson but I'm still here and stronger for it.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
thank you @chekohler . will check that link before bed-time
yours
Piotr
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
It is a very interesting project. However, I think in the current status of cryptocurrency market invest on any ICO it is very risky for short-terrm cashbacks.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
The hardcap is quite low so that ensures the market cap will start at a reasonable amount.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
This is interesting...
I've been reading up on cryptocurrency /Blockchain hacking and I didn't like what I see.
Security is a major issue and like you said, there are so many solutions that one doesn't know what to go for. The reliable ones are usually too expensive to lease and maintain
Cloudbric is a welcome development. I'm eager to see how it all goes although I see great potential in this.
The name VISION reminds me of Marvel's Avenger
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Marvel's Vision protected people in the physical world, Cloudbric's VISION will protect people in the digital world.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
hi @stazhao
My dear friend @hatu recommended me checking out your account. Im glad I did :)
So I just checked your profile just to realize that we seem to share a number of interests :)
In particular that we both share a similar passion towards cryptocurrencies and blockchain technology :)
I know it's hard at the beginning to build solid follower base. But just don't give up. Steemits needs solid content builders.
I will follow you closely.
Cheers
Piotr
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I am a big fan of blockchain tech.
I am sure you will like my future content too!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I love your condifence @stazhao :)
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I defenetly will investigate more about it !!! Thank you!!!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
You are welcome!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
The front lines of information security will not include humans. As defenses continue to succumb to an endless barrage of attacks and an almost immeasurable onslaught of new attack techniques, the notion of humans being able to deploy detection technologies and choreograph responses in real-time will fall away. In essence, human interaction with cyber defense will be deemed for what it currently is –imperfect and unreliable in the face of attacks that are largely automated and mostly reliable, if not perfect. It will be the fall of human cyber defenses and the rise of the cyber botted-defenses.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
AI is the future.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Interesting comment @prince121
I totally agree with @stazhao that AI will be the future
Yours
Piotr
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Yes, it's just a matter of time!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I can't appreciate this enough. Cybersecurity has to be the concern of every individual that is on the digital cyberspace and not just for some government official or likewise body.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
So happy to see that others see the importance of cyber security.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Very interesting project !
Cybersecurtiy will be a huge market in the future.
And it's connected to an existing company so thats's big advantage to other ICO's.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Early partnerships will be easy to achieve.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I learned little bit about the white hacking but as I learned something about it I saw that alot of misuse were going on even inside the white hacking also ....cyber security is an interesting topic and once you indulge in it u can easily came outside of it
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Defended (19.99%)
Summoned by @stazhao
Sneaky Ninja supports @youarehope and @tarc with a percentage of all bids.
Everything You Need To Know About Sneaky Ninja
woosh
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thank you!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
@stazhao has set 3.000 STEEM bounty on this post!

Bounties are a new way you can earn rewards irrespective of you Steem Power. Go here to learn how bounties work.
Earn the bounty by commenting what you think the bounty creator wants to know from you.
Find more bounties here and become a bounty hunter.
Happy Rewards Hunting!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations to the following winner(s) of the bounty!
Find more bounties here and become a bounty hunter.
Find more bounties here and become a bounty hunter.
Find more bounties here and become a bounty hunter.
Find more bounties here and become a bounty hunter.
Find more bounties here and become a bounty hunter.
Find more bounties here and become a bounty hunter.
Find more bounties here and become a bounty hunter.
Find more bounties here and become a bounty hunter.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @stazhao! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
Click on the badge to view your Board of Honor.
If you no longer want to receive notifications, reply to this comment with the word
STOPDo not miss the last post from @steemitboard:
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I gave you a vote!
If you follow me, I will also follow you in return!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit