
In a report released by the World Economic Forum in 2016, blockchain technology was recognized as one of the emerging technologies set to disrupt the society.
Having realized the potential of blockchain technologies and cryptocurrencies, several companies have since sprung up to leverage on the technology in order to enhance and incorporate it into their everyday life. However, there seems to be some resentment towards the full utilization of blockchain because it still has some defects such as low performance, poor scalability and technical difficulties. These issues have further limited the massive acceptance of blockchain and cryptocurrencies in several economies. For example, transactions processing in the traditional finance systems is quite cumbersome and payments could take as long as 1–3 days making the whole process slow. However, the typical blockchain networks that are supposed to address this anomaly, unfortunately also exhibit some of these issues, and this can be attributed to the influx of new participants and monopolization of the crypto ecosystem as the likes of BTC and ETH are the major digital currencies being used for payments.
Though, one of the enticing features of blockchain is the anonymity and transparency it provides. However, the issue with the typical blockchains such as Bitcoin and Ethereum is that there is no direct correlation between the on-chain addresses of digital assets and its true off-chain identity. This creates an avenue for fraudsters to use blockchain for illicit activities such as money laundering, terrorist financing etc. Due to this challenge, it becomes very difficult for conventional applications to incorporate cryptocurrencies into their operations because there will be a need for KYC and AML checks. In addition to this, is the issue of high technical difficulties.
Several blockchain companies have tried to address these issues but still haven’t found a headway. Due to this, Usechain is proposing a different model to bridge the current gaps in the blockchain industry. Usechain aims at building the world’s first mirror identity blockchain ecosystem, linking the real-world identity to the accounts of the mirror world on the chain.
This will address KYC issues because traditional companies will be able to incorporate blockchains and cryptocurrencies into their business operations without having to worry about how to conduct KYC and AML checks for their customers.
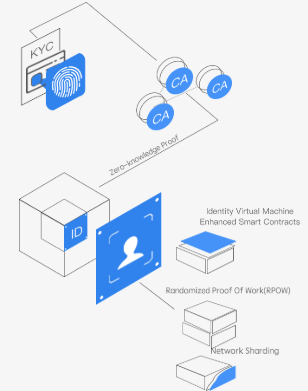
Usechain combines sharding technology, RPOW consensus, light nodes, multi-level authentication mechanism, and other innovative technologies to provide a public based mirror identity blockchain ecosystem. Below briefly outlines their different use.
Multi-level authentication mechanism- The authentication of users is done through cryptography to ensure privacy. This is achieved by initiating a correlation between the on-chain address and identity of the authenticated users. Once established, the mapping correlation is then registered on the chain.
Network Sharding- Typical blockchains require that a full node must be maintained to verify future transactions. This directly translates to a long processing of transactions which in turn affects the performance. However, Usechain aims to utilize the KaZaA P2P protocol, Identity Network Sharding and Identity Transaction Sharding to affirm transactions within the shortest period. i.e., rather than a transaction to be confirmed by all nodes in a network, it will instead be confirmed within the sharding of that particular transaction’s address.
Light Node Client- This was introduced into the system to help carry out verification of transaction and status. Through the use of higher-level Merkle Tree BCMT, the amount of data light-node needed to harmonize and substantiate the accuracy of a transaction will be greatly lessened.
RPOW — Having examined and identified the flaws with existing blockchains, Usechain aims to leverage on current algorithms, coupled with its secure, high-performance and anti-attack Tristed Execution Environment to provide a much better consensus algorithm called the Randomized Proof of Word. This algorithm was adopted because it can help accomplish verification of a high-frequency transaction, lower energy consumption and support mobile mining activities.
It is also able to resist attacks due to the amalgamation of decentralization and distributed ledger.
CONCLUSION
Usechain aims to provide an enabling blockchain ecosystem that can be applied to the mass market for commercial purposes. Usechain utilizes the latest technology in order to improve mass adoption of blockchains, thereby making traditional business operations that intend to utilize blockchain and cryptocurrency, to easily conduct KYC and AML checks.
Kindly visit https://www.usechain.net/ for more information.
Whitepaper: https://www.usechain.net/usechain_en.pdf
ANN: https://bitcointalk.org/index.php?topic=2498919
Twitter: https://twitter.com/usechain
writer: ammier
Hi! I am a robot. I just upvoted you! Readers might be interested in similar content by the same author:
https://steemit.com/blockchain/@ammier/the-first-mirror-identity-blockchain-ecosystem-usechain
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit