Over the years technological advancement has brought new and novel ways to do several things with ease and people have become so comfortable with living online. Virtually everything can be done online from shopping, meeting with new friends, education, working online, even businesses have moved online.
The average internet user is not aware of how much of their information could be gotten online and this information could be used to manipulate them or their loved ones.
The Cybersecurity Landscape
Cybersecurity is seen as a very complicated field of expertise by many and they envision it as a highly skilled or area that is meant for the special/skilled kind of individual. But in reality, we could be educated on how to secure ourselves online first, before looking at the third-party agencies to secure our data, most often they have the right professional or tools to secure to some extent our information.
The ever-increasing number of internet users have also paved way for the increased vulnerability of private data, which has lead to the ever-increasing need to secure private data and install adequate infrastructures to protect available important data.
What Is Cloudbric?
Cloudbric is a state of the art cryptographic project that leverages Artificial Intelligence to Deep Learning to create a universal security platform that secures both the web and the blockchain ecosystem to help further spread the widespread of cryptocurrency adoption.

Cloudbric Where We Are.
Cloudbric started as an in-house venture of Penta Security System Ic. The number one South Korea's enterprise web and data security vendor, and they currently protects over 10,000 members and organizations and 60+ enterprise partners, with over 25 data centers around the world.
Challenges In The Cybersecurity Landscape.
While there is no direct answer or solution to the cybersecurity landscape. It is increasingly evident that there are processes online users and institution could take to significantly reduce cyber risk, including collaborating with institutions and government agencies to reach an agreement on standards, laws, principles, code of conduct, best practices, and protocols with a recollection that trust has to be earned and continuously be validated.
Cybersecurity which can be an important tool in protecting privacy and preventing unauthorized information sharing, intelligence gathering, and ungranted surveillance. The risk associated with all attacks varies from 3 major factors. which are :
- Threats - This is basically a cybersecurity danger that might exploit a vulnerability to breach security to cause harm to the system. It could be related to who is attacking the system.
- Vulnerabilities: This is the weakness which can be taken advantage of by threat advocator such as hacker, fraudster or individual who is trying to perform unauthorized activities.
- Impacts: A successful cyber attack may cause major infrastructural damage to businesses or even individuals. It can your business trust and your business existence the impact of a successful security breach could be categorized into three parts:
- Reputation
- Legal
- Financial
Oversaturation of security solutions.
The ever-increasing rate for users and institution to stay up to date with the latest security protection has led to an outburst of different similar solution available to them. There are over 1600 cybersecurity solution out there, and this variety of product gives the user many alternatives and complicated issues for them.

Giving An Example:There are more than 10 antiviruses available in the market, users are most often confused as to which of the antivirus they should use. They most often end up not using the best antivirus suitable for them based on the operating system they are using and other logistic reasonings.
How Attackers Thinks.
In the game of cat and mouse: in the ever-growing battle between cybercriminals and cyber professionals. There is a blurred line on how and what strategy an attacker is trying to get to the system.
Cyberattack technique such as malware, phishing, ransomware, and nagware is ever-evolving, especially now that cybercriminals are using an anonymous forum to overcome geographical barriers to collaborate with other cybercriminals to carry out an even more dangerous attack.

Cybersecurity professionals are always on top of their game to be ahead of the attacker and provide defensive measures to vulnerabilities found in the system. And the battle has been on who is more skilled and more sophisticated with the tools to carry out an attack or prevent or block such attack.
Notable Mentions Of Cybersecurity Attacks.
- WannaCry ransomware attack: This is a well known cyber attack that took place in May 2017. It targeted all computers running the Microsoft Windows Operating System by encrypting data and demanded a payment in Bitcoin. This attack was caused due to the vulnerability in the Windows operating systems and was spread to the organization who haven't updated their operating systems after Microsoft released their updated patch.
- Yahoo : The massive hack of yahoo email systems happened in 2013, which caused a severe hack of all 3billion yahoo email addresses. It only became obvious in 2017, and information stolen in the attack include passwords, backup email address. This hack was possible because they were using an outdated encryption technique which are easy to crack.
- Even though it took longer to know the severity of the hack. The hack is one of the big once as Yahoo were the big players in the technology ecosystem.
- Github : On February 28, 2018, The almighty Github was attacked. A version control hosting service. It was hit by a massive denial of service attack, with a 1.35TB per seconds of traffic hitting the popular site. Though, it was knocked offline for a while and managed to come back online after 20 minutes.
- Ethereum : This might have not gained so much media attention in July 2017 the ethereum network was hit and about $7.4 million in Ether was stolen from the ethereum platform in a matter of a minute.
Staying Ahead of Constantly Evolving Attacker Activity
The cybersecurity landscape is a field that is constantly improving and attackers are steadily improving and developing a new strategy to break into a system. To stay ahead in the game cybersecurity professionals need to stay ever ready to learn new strategy and skills in improving their client's data.
Invest In Security
Since the field is ever evolving institutions and organizations need to invest in security tools for professionals to plan their security budget and get adequate tools to safe guide and block attackers. To stay ahead of the cybersecurity curve. The price tag for security systems varies, companies should regularly reinvest and access their stand.
Follow Best Practices.
The world is ever evolving with new technology experts over the years have developed best practices based on their experience and they have constantly improved it to suit both new and expert professionals. Professionals should encrypt just about everything.
Build The Business Around Security
This begins by educating your employee about the possible security breach and how to stay secure, and continuously establish security controls in your business workflow so it becomes easier and safer to take charge of your business security. Organizations should build awareness and constantly adjust methodologies so as to become proactive in the circle of security workflow.
Cloudbric solutions.
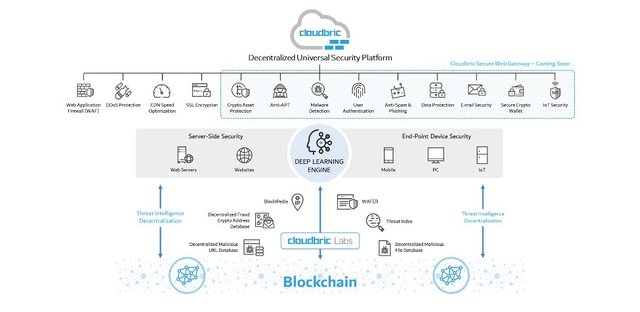
Cloudbric is the next generation of cybersecurity landscape. They are creating a technology that is second to none, making information security open and accessible to all users through the introduction of a new Decentralized Universal Security Platform. The use an Artificial Intelligence which is based on Deep Learning technique know as VISION to provide an all-inclusive pack of cybersecurity solution. They are creating the first decentralized cybersecurity ecosystem that is accessible to all users.
The Next Cybersecurity Technological Landscape.
Cloudbric looks to expands on security possibilities by developing a new user-focused technology solution to enable the security community to usher into the next evolution of the cybersecurity landscape. They have gained global awareness in the past few years of operation and are the No.1 cybersecurity solution in the APAC region and no 5 in global rankings by the top security analyst.
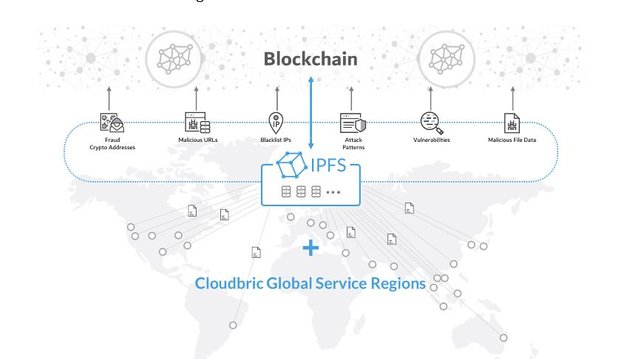
Decentralization Of Threat Intelligence.
The fundamental aspect of Cloudbric reverse ICO is to decentralize all intelligent information on the blockchain. It uses Deep Learning technique to train possibilities of cyber attacks, this will gather a large amount of anonymous user-generated attack logs for collective transparency and open verification.
The sole purpose is to develop the largest cyber threat database across various protocols. This protocol covers both the web, mobile and cryptocurrency threats ( both exchanges and wallets) and making all these information accessible to the general public through the development of new interactive Cloudbric Labs resources tool and custom API.
Partners and investors.
The Cloudbric company have been in existence for a while and have had proven success track record for the past few years of existence and have gained media recognition from top media companies like Forbes, Yahoo, Infeng, Ivan on tech among several others. The list of their media mentions are below.
Team
The Cloudbric team is sophisticated with a list of proven professionals who have had several years in the information security field, which tells the story behind their success story. Teams stand at the pivot of any company and if the team is right it shows the project is on the right side to succeed as a project.
Advisors
The team of advisors I found on their website is quite gigantic as they have surrounded themselves with leaders in high tech companies like Samsung, foundation X amany notable professionals.
Sungjae (Jay) Hwang - CEO, FoundationX
Sungjae Hwang is a serial entrepreneur, investor, and inventor. CEO and Co-Founder of FoundationX, Founding Partner of Futureplay, Chief Product Officer at Fluenty Inc., Chief Strategy Officer at Pium Labs Inc.
Young Ha KimFormer CEO of Samsung Electronics China
Former CEO of Samsung Electronics China, 30+ years of experience in the Chinese electronics and technology development market, a professor at Dankook University
Dr. Jae Woo LeePh.D, CISSP, CCFP, CISA, CISM
30+ years of information security expertise, Advisory Board for Kaspersky Labs, Inc., founder of the Korean Information Security Agency (KISA), recipient of the Harold F. Tipton and Harold Weiss Award
Edward PiaoCEO, Blue chain Asset MGMT Co., Ltd & Interblock Inc.
Lawyer Chengzhe Piao graduated from Peking University, Political Administration Department specializing in the training of senior management. Top investment lawyer in China and has advised Korean/Chinese companies on legal and investment cases. Also operating the Korean Center for “China Blockchain Application Research Center (CBAC)”, which is supported by the Chinese Government and involved in Cryptocurrency business in China.
Trent BarnesPrincipal at ZeroCap
Blockchain and corporate advisor and Board Member of the Blockchain Association of Australia. Entrepreneurial background in the tech, skin-care, and recruitment industries. Co-founded one of Melbourne's premier IT recruitment companies, CircuIT Recruitment, which he sold in 2016.
Steve C.Y. PangExecutive Director of Goldford Venture Capital
Executive Director of Goldford Venture Capital & Goldford Group, 20+ years of experience in financial services and IT sector focusing on China market. An executive at Swire Group, Executive at Zurich Financial Services, Chief Advisor Officer at Aviva Hong Kong
Kyle RileyCo-Founder, iosiro
Director at Zenoic, Research Team Lead at MWR InfoSecurity, Cybersecurity Expert with Solidity Experience
William H. NguyenPh.D Harvard University
Founder and Chairman at EdooPAD, Chief Crypto Architect for GIFTO (GTO), CEO and founder of Kryptono Exchange, Chairman at Krypto Limited, Founder at Universal Technology Group, Alfred P. Sloan Postdoctoral Fellow at Harvard University
Kazunari MiyazakiHead of NEC Venture Fund
CPA, Head of NEC Venture Fund, 10+ years of M&A and venture investment experience, Director of BIGLOBE
Jin Woo ShinPh.D Massachusetts Institute of Technology
Associate Professor at Korea Advanced Institute of Science and Technology & Ph.D. Massachusetts Institute of Technology
Caspar WongCEO of Goldford Fintech
VP of Goldford Group, Chairman of Hong Kong Young Professional Alliance Blockchain Committee, Head of Marketing at Quantum Gold, Founder at WhenAsk, PolyU Council Member at The Hong Kong Polytechnic University
Conclusion
The Cloudbric project is a new heaven in the cryptocurrency landscape as it proposes to mitigate currency security threats we find within the cryptocurrency ecosystem. The Cloudbric solution would proffer new way to protect users data and the ecosystem would enable all users to be able to access cybersecurity threats by introducing a decentralized Universal Security Platform, which is based on Deep Learning.
Finally, the more critical I look into the project the more exciting I get. The proposed mechanism is quite logical and reasonable following the recent trend of cyber threats. The cloudbric solution is here to make both the web and cryptocurrency landscape a safe zone for all.
Visit the www.cloudbric.io official website, join the social media communities and consult the official documents for more information about the project.
Official Contacts
Website : https://www.cloudbric.io/
Telegram : https://t.me/cloudbric
ANN Thread : https://bitcointalk.org/index.php?topic=4376899.0
Twitter : https://twitter.com/cloudbric
Facebook : https://www.facebook.com/cloudbric
Github : https://github.com/Cloudbric-Project/Cloudbric-Contracts
Reddit : https://www.reddit.com/r/cloudbric/
Medium : https://medium.com/@cloudbric
Connect with me on Bitcointalk - https://bitcointalk.org/index.php?action=profile;u=1442709;sa=summary
Join My Telegram Channel For Updates On The Latest ICOs : https://t.me/cryptoviews_en
If you like my article kindly Upvote, drop your comment or question in the section below.

Good Luck, Happy Investing.
This article is not a financial advice. Investing in ICO may be extremely risky, always remember to do your own research and consult financial and legal advisors before investing in ICOs.



You got a 5.70% upvote from @joeparys! Thank you for your support of our services. To continue your support, please follow and delegate Steem power to @joeparys for daily steem and steem dollar payouts!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
With the high trend of cryptocurrency lately. Cyber attackers are becoming more aware of vulnerabilities of users and institutions and the it is expected to increase in high number as many crypto users are not aware of security measures to secure their crypto assets ?
What mechanism are you putting in place to educate the vast majority of crypto users who are not informed on safety practices for their crypto assets.
No doubt, the content is very informative and educative. Having an existing product and now doing a reversed ICO to generate 10000ETH from what I saw on the website is a steal on market valuation.
I wish the project luck but what partnership do they have with any cryptocurrency exchange or crypto wallet as that is their area of focus ?
Thanks for the insight.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
This post has received a 9.39% upvote from @msp-bidbot thanks to: @minnowpond. Delegate SP to this public bot and get paid daily: 50SP, 100SP, 250SP, 500SP, 1000SP, 5000SP Don't delegate so much that you have less than 50SP left on your account.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
You got a 3.56% upvote from @oceanwhale courtesy of @minnowpond! Earn 100% earning payout by delegating SP to @oceanwhale. Visit www.OceanWhaleBot.com for details!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
This post has received a 6.25% upvote from @lovejuice thanks to @minnowpond. They love you, so does Aggroed. Please be sure to vote for Witnesses at https://steemit.com/~witnesses.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Nice post ! You got 4.92% upvote from @flymehigh. Earn free sbd/steem daily by delegating(renting) your SP. We share high return, click here to delegate your sp to flymehigh if you don't know, how to earn passive income by delegating your SP click here for more info Join our discord You can promote your posts. Thanks.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thank you @devblock for this informative review. I have been a victim of cyber attack that cost me a lot. Not in block chain space though.
The blockchain space is heavily flooded with different strategic attack on a daily basis on exchange, wallets and website "Phising".
I really wish the project good luck on their innovative technology to create an atmosphere that is both secured and safe for all crypto users.
And as technology continue its massive growth more and more strategy would be put in place to secure our crypto asset and experience.
Success to the team.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
You got a 6.98% upvote from @sleeplesswhale courtesy of @minnowpond!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
You got a 10.74% upvote from @steembloggers courtesy of @minnowpond!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
You got a 2.84% upvote from @minnowvotes courtesy of @minnowpond!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
You got a 10.70% upvote from @dailyupvotes courtesy of @minnowpond!
To support this service please vote for @chitty as a witness.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Excellent write up. I have learnt a new thing and I do think the idea is innovative to provide one of the best use case of blockchain technology.
With the implementation of this technology our bitcoin and all altcoin would be safer. I would try to invest in this project. I see great future for it.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
You got a 100.00% Upvote and Resteem from @ebargains, as well as upvotes from our curation trail followers!
If you are looking to earn a passive no hassle return on your Steem Power, delegate your SP to @ebargains by clicking on one of the ready to delegate links:
50SP | 100SP | 250SP | 500SP | 1000SP | 5000SP | Custom Amount
You will earn 90% of the voting service's earnings based on your delegated SP's prorated share of the service's SP pool daily! That is up to 38.5% APR! You can also undelegate at anytime.
We are also a very profitable curation trail leader on https://steemauto.com/. Follow @ebargains today and earn more on curation rewards!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit