
INTRODUCTION

The evolution of financial systems has a very interesting history. The fact that we are talking about money today actually began in the form of fiat money in the form of a bronze shell called "Chao" in the year 1,000 B.C. in China. But today fiat currencies are now supported by governments and serve the societies in which they are located.
However, since the emergence of bitcoin in 2008, cryptocurrency units have been developed that serve the needs of specific communities that form a specific project around which it is built. Although not perfect yet, the financial system of cryptocurrencies has evolved into a structure that is beginning to take more control over financial segregations with a high degree of functionality, which can surpass even the functions offered by traditional fiat systems, individual and smaller ecosystems.
Crypto money, therefore, allows the storage of wealth in a small ecosystem or local currency specific to a particular community (usually an online community dedicated to a particular purpose) and therefore provides the recognition of such a community within a global valuation network.
However, the cryptography science that we started hearing with Blockchain technology is a system developed to solve security issues that are the basis of many security vulnerabilities. The correct use of this science can give us a new perspective on security. But this is never enough alone. Even if we use decentralized stock exchanges and secret keys, we still can't get rid of being a toy in the hands of hackers and fraudsters. One of the biggest reasons for this is the security vulnerabilities in the devices and smart devices we use. Although our secret keys create an encrypted algorithm, still providing access to our device with old-fashioned systems causes these vulnerabilities to arise.
In the same way, software installed on our smart devices cannot provide us with fully secure internet experience. The software we use may be Linux, Windows, or OS. But this software is the software that puts the functionality into the forefront, they can not provide our security in full sense. What we need is new Blockchain software, which comes to the fore with the science of Cryptography from the beginning.
We need three things exactly to ensure our security under these conditions: Blockchain technology, a much safer software, a device designed using the cryptography science.
Before you mention the importance of the three elements above, I would like to introduce you to the Securypto project. Securypto is a masternode-based Zero coin project. Before introducing this platform that is different from most projects you know, I would like to briefly mention zero coin and masternode systems.
What is Zero Coin Protocol?


Zero coin is actually a project to cover the shortcomings and weaknesses of Bitcoin. Because when you use bitcoin, it can be seen by anyone, where, how much, what you buy or who you send money to. You can see this not only in the state, but also in your friend or foe, and a serious security breach will occur. If you are taking extra care of your safety, this situation may bother you a little.
The Bitcoin payment network offers an extremely redistributed mechanism for making and transferring electronic money around the world. sadly, Bitcoin suffers from a serious limitation: since transactions are kept during a public ledger (called the “blockchain”) it should be doable to trace the history of any given payment — even years when the actual fact. Worse, since the Bitcoin ledger is public, any party will recover this data and information mine to spot users and patterns within the transactions. In alternative words: Bitcoin transactions are conducted publicly.
The Zero coin protocol uses demonstrably secure scientific discipline techniques to confirm that Bitcoins cannot be traced. These techniques permit users to conduct transactions on the Bitcoin network whereas receiving sturdy mathematical guarantees that the transactions cannot be traced. These guarantees stay in place whether or not a little of the Bitcoin network is compromised by associate degree attacker.
Imagine yourself and your other 2 friends in a room. This put one dollar in the wallet in front of 3 friends. It's known who put the dollar at the moment. But the wallet a 4.the guy doesn't know who the dollar belongs to. The zero coin protocol is simple, and the security measures it provides are at maximum level.
What is Master node?

The master node system was first discovered by coin, known as Dash. In this system, the owners of the Dash coin, for example, keep 1,000 DASH coins locked in their wallets. The number can never be less than this number. Through these locked coils, Dash's operations in the blockchain network are approved. This system serves 24/7. This system, similar to bitcoin mining, is technically slightly different from it. Users whose credits are locked up are rewarded for a certain period of time as a result of their benefits to the Dash platform. The master node system is installed on devices that require electricity, such as the same mining, and they operate continuously.
These two systems offer a very important service to the end user: anonymously file, money, information exchange, and this information are protected by the science of cryptography. Can not be traced, cannot be stolen.
Now let's talk about the three components that comprise the Securypto platform.
1 - Software:
The software that Securypto uses has a system that can be used on Windows, Linux, Android and other platforms. User-friendly interface and easy-to-use are some of the most important reasons that make this software special. This software is open-source code. So anyone who wants to contribute to this software. You can easily use this software on your computer and on your phone. With this software, any information or money transfer you make is encrypted with cryptography and it will become almost impossible to access and track.
2 - Blockchain
Blockchain technology was needed because the money flow could not be adapted to the requirements of the global world. In a world that is now almost limitless, the flow of money must also be fully liberated. Neither the government nor third-party companies should interfere with this. The fact that people want to make money transactions more confidential and fewer commissions has finally introduced us to this technology.
3- Dedicated Hardware

This device, known as DigiSafeGuard, was created with the combination of the software and Blockchain technology that Securypto specifically designed. It's almost the size of a phone, and it's pretty simple to use. You can exchange money, coins, files, messages on this device with your own touch-screen keyboard. When using this device, you can assign a password to the device and use the 2-factor authentication service. Now let's talk about some of the features of the device:
Application Areas Of The Device:

Hardware Data VaultStandalone Data Encryption DeviceHardware WalletAnonymous Encrypted File TransferAnonymous Encrypted Messaging
Why is Anonymous encrypted messaging so important an why we should use Securypto for this?

Messaging and instant communication with other people is an activity that we do every day and almost every second. These messages are monitored by the government and other third-party companies. Because most messaging applications sell our personal data to third party companies to generate advertising revenue. Although new-generation messaging applications such as Telegram, which are encrypted from one end to the other, are somewhat hindered by this, the measures are still not enough.
That's exactly where DigiSafeGuard comes in. The encryption used by DSG is also an end-to-end encryption system, but Securypto takes these security measures one step further. Simply put, the algorithm used by DGS is as follows:
DSG lets users create their own RSA key and export it on demand
DSG lets the users import their own RSA key
The RSA keys created in end-to-end encrypted programs such as Telegram is known by the service provider and is open to access by those who developed it. But when using DGS, you go a step further and the generated keys are not known by the system or by the developers. This means that the encryption keys you have created are only used by you and only available to you.
The Way The DSG Works:

Step 1: When you use the DSG, you will be set up a special RSA phrase enabled key pair.
Step 2: The public key created is sent to the party who wants to reach you via the message. And in this way, you can send a message or file to the receiver using the public key that was sent to it.
Step 3: When the user wants to send a message to a third party using the DSG hardware, this message is encrypted by the DSG encrypted system. And it loses all traces of the user. It can never be traced, and no one from the outside world can understand who this message belongs to. Even a third device connected to the DSG cannot break this key.
Step 4: DSG generates a QR code for the message it generates with this secret key and can be transmitted to messaging applications such as Telegraph, Whatsapp. Not just these applications, this Code can also be transmitted to any application that functions like messaging, such as Gmail, Facebook, Twitter.
Final Step: Finally, when this message reaches the recipient. The receiver reads the QR code and can read the message without knowing what connection it is coming from. This message can only be read by the person who has read the QR code and cannot be reached by a third person in any way.
Creating a fully equipped privacy network


Services such as Telegram, Whatsapp, Gmail are relatively safe applications. But because all the resources are stored in a non-decentralized warehouse, it contains security holes in itself. As a result, our private information is purchased by third parties and companies. And they have the right to lead us as they wish.
If we use these messaging applications with DigiSafeGuard, these companies against us cannot violate our security. When we use this device, as the Zero Coin Protocol says, we will use a security service that cannot be traced, followed or tampered with.
Why is Anonymous encrypted file transfer is so important and how firms like Netflix, Amazon Prime, Security Agencies can use this technology to save their data information?

File Encryption

DigiSafeGuard users can also implement the system they set up for the same messaging applications. With RSA encryption, users can encrypt files, folders and even information on an entire hard disk from one end to the other. And they can send this information to any user they want. Other than that, users can sell their material value information into the Securypto network, but we will talk about it later. But before we do this, let's talk about how users can encrypt files and folders on their hard drives or USB devices via DigiSafeGuard.
Step 1: The user plugs the USB device or hard disk into the DGS hardware.
Step 2: DSG encrypts this information so that only the recipient can read it.
Step 3: The user gives this encrypted hard disk or USB device to the recipient. However, the information contained in these devices is not required to be transmitted through a device. All these files and folders can be transmitted to the recipient via the internet.
Final Step: The receiver receives encrypted devices and puts them to its DigiSafeGuard hardware. DGS opens this encrypted information with its own private key and becomes available.
Today we live in a world where television has lost its importance. The television is replaced by user-oriented and internet-enabled platforms such as Netflix and Amazon Prime. People are now using such new platforms more than ever. One of the biggest reasons for this is that users have the opportunity to watch the program they want at any time. When we watch television, what we are going to watch determines the broadcast flow of that channel. And sometimes we may have to watch the programs we don't like watching. But the emergence of new platforms in the emancipated world has developed the area of freedom for people. Therefore, platforms such as Netflix and Amazon Prime are constantly spreading and increasing the number of users.
In light of all this information, we face an important problem. The new platforms mentioned above require monthly or annual membership fees for the services they provide. However, users who pay for this service will have the right to benefit from these services.
But not all people want to pay for these services. Some people prefer to use these services on the Internet and find it illegally. One of the biggest reasons for this is the security vulnerabilities of these platforms. Platforms cannot prevent the services they provide with users to be copied and stolen.
That's exactly where Securypto comes in. We mentioned above how DigiSafeGuard protects files and folders. This information can only be accessed by the sender and the receiving party. And it is impossible to steal this by third parties.


Netflix and Amazon Prime, such as platforms using the Securypto platform to encrypt data by stealing a healthy way to prevent theft of these stolen and prevented the opportunity to increase the company profits.
Why platforms such as Netflix and Amazon Prime should use the Securypto platform is important here. It is also possible to increase corporate profits because it prevents theft by encrypting data in a healthy way and preventing it from being stolen. The Securypto and Digisafeguard hardware maximizes the confidentiality between individuals and companies and aims to make both sides profitable. Because these platforms are costing millions of dollars because of stolen and copied data. This causes users to pay relatively more monthly fees.
If online platforms such as Netflix and Amazon Prime cooperate with a robust platform such as Securypto, both companies and users will be profitable.
All the protection activities mentioned above also apply to Security Agents. As a result of ensuring full security, legal sanctions can be applied in full. The problems such as theft of data, copying of data, which are legally prohibited, will be easily overcome. In this way, both companies and security agencies will be able to use their data safely without the risk of stealing it.
Well, is that all? No, it's just starting.

Monetizing content distribution and paid content management feature:

On the agenda, especially blockchain technology gained speed and the possibility of making new money emerged. Examples of ecosystems such as Steemit, Mithril. On such platforms, you can generate income with articles, shared pictures. Unlike older applications, especially Facebook, Instagram uses non-blockchain technology, new platforms set up new platforms, user-oriented, thanks to the content they share allows them to be rewarded.
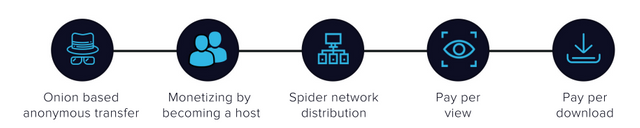
Here is a system that will allow Securypto to make money for its use. Users can earn money by using hostnode systems, by checking the correctness of their operations on the network, or by simply submitting content to the platform. If the user wants to sell the content they have he/she can send it to the network to gain money. As a result, revenue can be generated in a correct proportion to the number of downloads or the number of displays for the user. The advantages of this system are as follows::
Onion-based anonymous data transfer
Spider Network distribution
Monetizing by becoming a host
Monetizing by pay per view/download
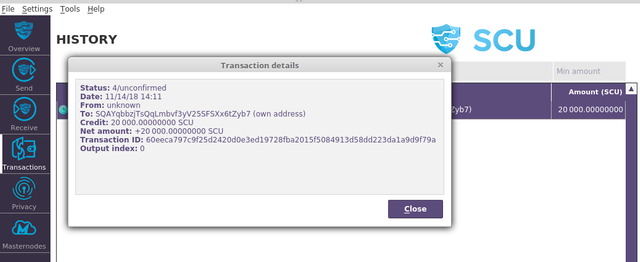
To obtain passive income with masternode system

I told you a little about how the masternode system works upstairs. Mastermode is a system based on computers and other devices and should remain open 24/7. This system provides you with a profit by confirming the operation of the coin. It is just not enough. You can use the masternode to lock a part of that coin you have to the system. This number can be a different number for each coin. In addition, each coin has no masternode system. By doing more detailed research on the internet, you can find out which coins you can install a Masternode system for.
After setting up your computer this system, the system automatically begins to work for you. And even when you sleep, the system makes money for you. Thanks to the platform coins you keep locked in hand, you contribute to the system. And as a result, you will be rewarded monthly by the platform.
Other Features of DigiSafeGuard

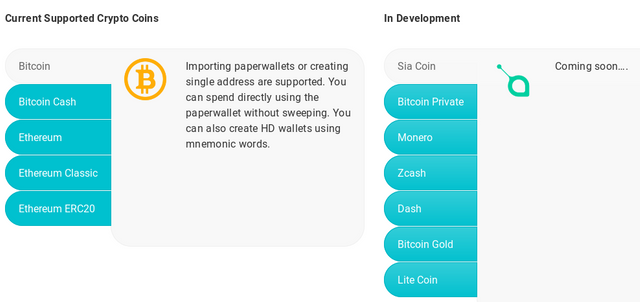
By using this hardware wallet you can collect a lot of coins. These coins are now limited and if you can see the picture below you can see which coins are available on this platform for now. And you can see which coins going to join this wallet soon.
By using this hardware wallet you can send, receive and store stated coins on DigiSafeGuard
You can store your all files, passwords, top secret information on this wallet. This means you can use this wallet standalone encrypted file store
- You can access a lot of online services like Banks, Hotmail, Facebook, Whatsapp etc.
- This hardware-software designed to be user-friendly. If you have not been met the Blockchain technology, this is not a matter. This hardware is as easy to use as a cell phone.
CONCLUSION

Since blockchain technology emerged, it still faces security issues. As a result, we see thousands of people or stock exchanges hacked and robbed. But we don't have to live in the shadow of all these problems. Because it's not just about the money. Our personal data, files, folders, pictures, passwords. These are all in constant danger where the internet is located, and this has to stop now.
Securypto wants to solve all these problems thanks to the features it provides. The special keys provided by the platform can be seen by neither platforms nor those who developed this platform, and this gives us 100% security.
If you are a person who cares too much about the security of your personal data, you should definitely meet this platform. In addition, if you own a company and want to store the company's data on a special platform, Securypto is a place for you.
MEET THE TEAM

For Further Information:

Securypto Panel ID: 18878
Telegram username: @Nuxxorcoin
This project has a great vision and i hope they will get the success. Im looking forward to buy this hardware.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @kadjar! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
Click here to view your Board
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
The Zero coin protocol uses demonstrably secure scientific discipline techniques to confirm that Bitcoins cannot be traced. This is next level technologhy about blockchain.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Securypto is a great platform where you can make money from encrypted data transfer and storage. I expect to be successful in ICO
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I really like the Securypto project. Especially I love DigiSafeGuard device which is a game changer apparently. Thanks.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Securypto provides to its users top privacy. If we are living in internet era, authority couldn't watch us easily. It is not about being illegal, it is about being free.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thinking all about the privacy concerns, Securypto comes to help the internet world.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Securypto is very important project for Blockchain technology. Thanks to the features they have reaching privacy is supereasy now.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thank you for information about Securypto project.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations! This post has been upvoted from the communal account, @minnowsupport, by kadjaar from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, someguy123, neoxian, followbtcnews, and netuoso. The goal is to help Steemit grow by supporting Minnows. Please find us at the Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.
If you would like to delegate to the Minnow Support Project you can do so by clicking on the following links: 50SP, 100SP, 250SP, 500SP, 1000SP, 5000SP.
Be sure to leave at least 50SP undelegated on your account.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
A great article regarding one of the best security projects of all time. Securypto seems amazing with its team and advisors.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Privacy and security are the big issues of crypto market, Securypto has reliable and funcktional solutions to fix those problems.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
The project team is on the path of honesty. Informing the investors about each topic will ensure their success in a short time
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
A good project to make data transfer the safest way, I hope they will succeed.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
It is one of the important projects for the use and dissemination of digital money.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
If you own a company and want to store company data on a private platform, Securypto will provide the ideal storage service for you. The right project for investment.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Zero coin is actually a project to cover the shortcomings and weaknesses of Bitcoin. Because when you use bitcoin, it can be seen by anyone, where, how much, what you buy or who you send money to.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Securypto is a Zerocoin, masternode-based blockchain project focused on anonymous storage & transferring of encrypted data.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit