
Asset – People, property, and information. People may include employees and customers along with other invited persons such as contractors or guests. Property assets consist of both tangible and intangible items that can be assigned a value. Intangible assets include reputation and proprietary information. Information may include databases, software code, critical company records, and many other intangible items.
An asset is what we’re trying to protect. For example furniture in a house.
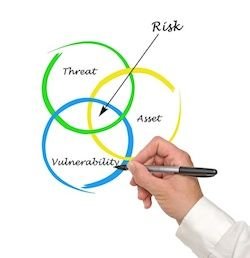
What are the most commonly mixed up security terms? Threat, vulnerability, and risk.
Threat – Anything that can exploit a vulnerability, intentionally or accidentally, and obtain, damage, or destroy an asset.
A threat is what we’re trying to protect against. for example rain
Vulnerability – Weaknesses or gaps in a security program that can be exploited by threats to gain unauthorised access to an asset. For example, a leaky roof on a house
A vulnerability is a weakness or gap in our protection efforts.
Risk – The potential for loss, damage or destruction of an asset as a result of a threat exploiting a vulnerability. for example, water damage to furniture inside the house.
Risk is the intersection of assets, threats, and vulnerabilities.
Why is it important to understand the difference between these terms?
If you don’t understand the difference, you’ll never understand the true risk to assets. You see, when conducting a risk assessment, the formula used to determine risk is….
A + T + V = R
That is, Asset + Threat + Vulnerability = Risk.
Risk is a function of threats exploiting vulnerabilities to obtain, damage or destroy assets. Thus, threats (actual, conceptual, or inherent) may exist, but if there are no vulnerabilities then there is little/no risk. Similarly, you can have a vulnerability, but if you have no threat, then you have little/no risk.
Accurately assessing threats and identifying vulnerabilities is critical to understanding the risk to assets. Understanding the difference between threats, vulnerabilities, and risk is the first step.
So the moral of the story is that prevention is better than cure .

This is where Uncloak comes in.
The growth in Cyber Insurance purchases shows that businesses now see cyber as a risk that needs to be managed rather than merely a problem that needs to be fixed by IT. More and more business owners have considered adding Cyber coverage to their business insurance?
Our aim at Uncloak is to ensure that your network is protected from malicious attacks (hackers/malware/viruses) using our state of the art software running on the blockchain.
Threats are exposed and validated
- Bug bounty: security testers are rewarded for identifying new threats
- AI technology: scans millions of records on the public internet and the hidden internet, searching for new and existing * vulnerabilities and potential new vulnerabilities, identify latest cyber threats
- Uncloak’s database: provides a constant real-time cyber threat inventory
- Businesses can stay ahead of and eliminate cyber threats themselves, rather than relying on expensive 3rd party services such as those provided by the big four consultancy practices.
Please connect on Uncloak Telegram channel for all updates and announcements
https://t.me/uncloakio
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://www.threatanalysis.com/2010/05/03/threat-vulnerability-risk-commonly-mixed-up-terms/
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit