The opinions expressed in this blog are my own views and not those of Cisco.
Introduction
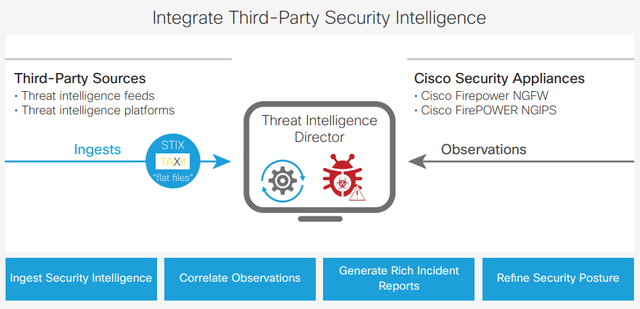
Cisco's Threat Intelligence Director runs on Cisco's Firepower Management Center. It is used to ingest threat intelligence using open standards. Firepower sensors (essentially Cisco's NGFW or NGIPS) provide a rich source of information that includes host and user information, traffic flows from source & destination IP's, port and protocol. Utilising this existing information and leveraging the Threat Intelligence Director you are able to expand your security effectiveness by detecting actionable indicators of compromise from those threat feeds.
What is the Firepower Management Center
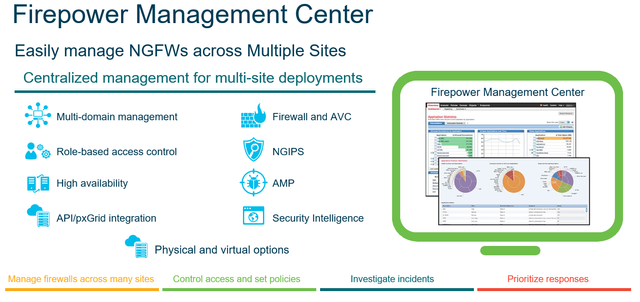
The Firepower Management Center provides unified management of Cisco's NGFW and NGIPS known as Firepower Threat Defence.
Why Use Threat Intelligence Director?
Cyber Security teams are typically ingesting threat intelligence from multiple sources. They then try to operationalise that threat intelligence information in their environment which can present challenges. By using the Threat Intelligence Director on the Firepower Management Center you are able to leverage threat intelligence information leveraging the existing intelligence in Firepower Management Center.
Threat Intelligence Sources
Industry Organisations
There are a number of commercial organisations that provide threat intelligence information for specific industries. Some of these organisations offer threat feeds but may not support STIX/TAXII.
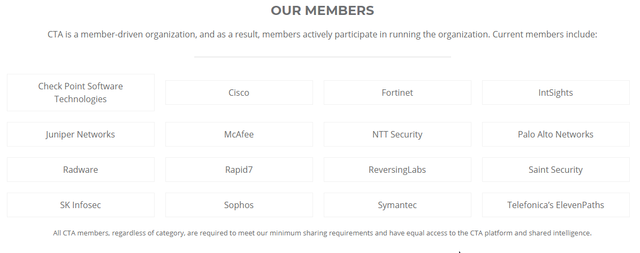
Cyber Threat Alliance - The CTA is a not-for-profit organization that is working to improve the cybersecurity of our global digital ecosystem by enabling near real-time, high-quality cyber threat information sharing among companies and organizations in the cybersecurity field.
Financial Services Information Sharing and Analysis Center - FS-ISAC was established by the financial services sector in response to government directives mandating that the public and private sectors share information about physical and cyber security threats to help protect the U.S. critical infrastructure.
R-CISC - Cyber intelligence sharing for the for the Retail Industry. Membership fees are based on the companies revenue.
Open Source STIX/TAXII Threat Intelligence Feeds
I found a one-stop shop for a list of threat intelligence feeds on GitHub by Herman Slatman aka hslatman titled awesome-threat-intelligence. This begs the ultimate question. Which threat feed will give me the most value. With so many open source threat feeds do I still need to procure a threat intelligence feed from a vendor? Further analysis is required to answer this question.
The below open source feeds look like a great starting point providing STIX/TAXII support.
Open Source Threat Intelligence Feeds
These feeds may not provide native STIX/TAXII support so you have two options. Build your own server that downloads the feeds, normalise/parse that feed then provides the data to FMC via your own TAXII server. Procure a threat intelligence platform that utilises the feeds you require and provides you with a STIX/TAXII feed.
- Abuse.ch Trackers
- Bambenek Source
- Blocklist.de
- BotScout Bot List
- Botvrij
- BruteForceBlocker
- CI Army List
- Cryptam
- Dan.me Tor List
- GreenSnow Blocklist
- ETOpen Compromised IPs
- Hybrid Analysis
- Liste Malware
- Malshare Daily Malware List
- Malware Domain Blocklist
- Malware Domain List
- PDF Examiner
- PhishTank
- Rutgers Attacker IPs
- SARVAM
- ThreatExpert
- ViruSign
- VX Vault Source
- WSTNPHX Malware Email Addresses
Threat Intelligence Vendors & Platforms
A threat intelligence feed may be included in a security product you procure from a vendor an additional paid subscription or an entire threat intelligence platform. Some players in the commercial market are:
- Accenture iDefense
- Anomali
- Booz Allen Hamilton Cyber4Sight
- Cofense Intelligence
- Cisco Talos
- Crowdstrike Faalcon Intelligence
- Department of Homeland Security
- Digital Shadows
- EclesticIQ
- Flashpoint
- FireEye iSIGHT Intelligence Subscription
- Infoblox
- Intel 471
- Kapersky
- Lookingglass
- Recorded Future RiskList
- Symantec DeepSight
- TheatQuotient
- ThreatConnect
Threat Intelligence Director Configuration
Requirements
The Threat Intelligence Director requires Firepower Management Center to have:
- over 15GB of RAM to operate
- FMC and FTD running version 6.2.2 or later
- REST API Access enabled
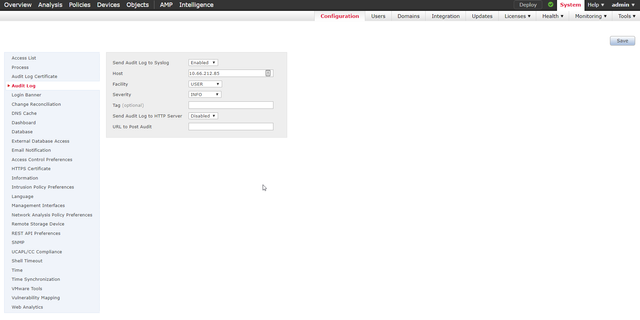
- Enable the REST API. System -> Configuration -> Rest API Preferences
The Firepower Management Center Configuration Guide, Version 6.2.3 states there is no performance impact on managed devices.
If you host TID on the active Firepower Management Center in a high availability configuration, the system does not synchronize TID configurations and TID data to the standby Firepower Management Center. We recommend performing regular backups of TID data on your active Firepower Management Center so that you can restore the data after failover.
Threat Intelligence Director Terminology
Indicators and Observables
Observables is an IOC. The IOC can be a:
SHA-256
Domain
URL
IPv4
IPv6
Email To
Email From
Email Sender
Email Subject
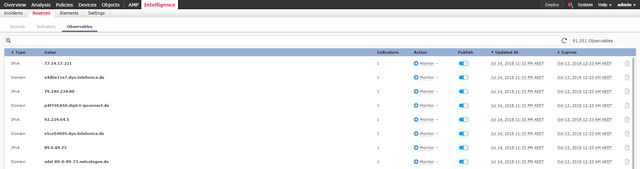
| Observables Bar | Definition |
|---|---|
| Type | The IOC. See the list of supported IOCs above |
| Value | The value or string of the IOC Type |
| Indicators | The number of Indicators using this Observable |
| Action | The action of the observable. This can be Monitor or Block |
| Publish | Pause or enable publishing of observables to elements |
| Updated At | The last time the observable was updated |
| Expires | The timestamp of when the Observable will expire |
| Whitelist | That icon at the very end allows you to add or remove the Observable from a whitelist |
After the Observables are published to the elements, the elements monitor traffic and report observations to the Firepower Management Center when the system identifies Observables in traffic.
Indicators contain one or more Observables. Indicators convey all the IOCs associated with a known threat. An Incident is created by the Threat Intelligence Director and an event is generated in FMC if an observable meets the conditions of an Indicator.
Upon adding the source, you cant change the whole feed to block. This has to be done individually on Indicators and Observables.
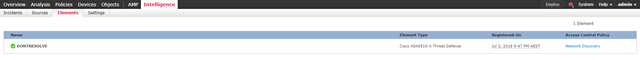
Elements
An Elements is a managed Firepower Threat Defense device.
Licensing
TID requires the Threat Defence License for Security Intelligence Filtering. A Malware license is required to configure file policies for SHA-256 observable publishing.
STIX Requirements
STIX Files must be STIX Version 1.0, 1.1, 1.1.1, or 1.2 and adhere to the guidelines in the STIX documentation: http://stixproject.github.io/documentation/suggested-practices/. STIX files can include complex indicators.
Flat File Upload Requirements
Files must be ASCII text files with one observable value per line. Each file should contain only one type of content:
SHA-256 - SHA-256 hash values.
Domain - Domain names as defined in RFC 1035.
URL - URLs as defined in RFC 1738.
IPv4— IPv4 addresses as defined in RFC 791. (CIDR blocks are unsupported)
IPv6— IPv6 addresses as defined in RFC 4291.
Ingesting Feeds
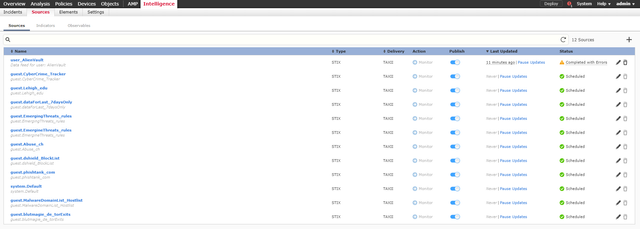
Intelligence -> Sources -> Add Source
Threat Intelligence Director supports the following feeds:
- STIX/TAXII
- URL (STIX or Flat File)
- File Upload (STIX or Flat File)
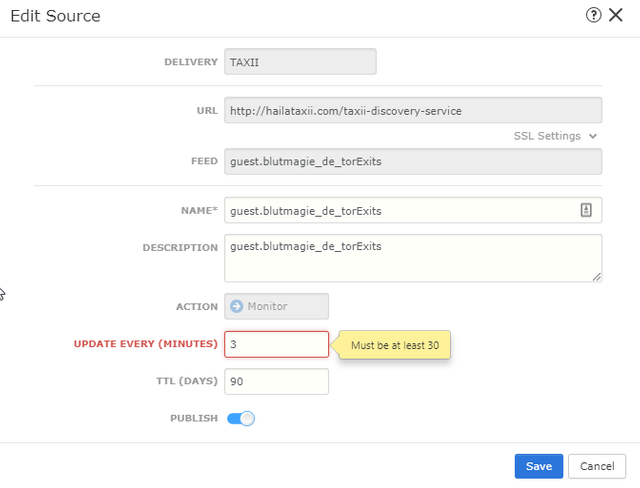
The minimum update time of a feed is 30 minutes imposed by FMC.
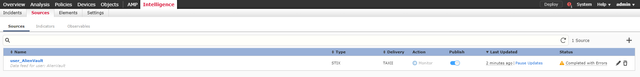
AlienVault Open Threat Exchange (OTX)
- Create an account and login to AlienVault OTX
- Click on API
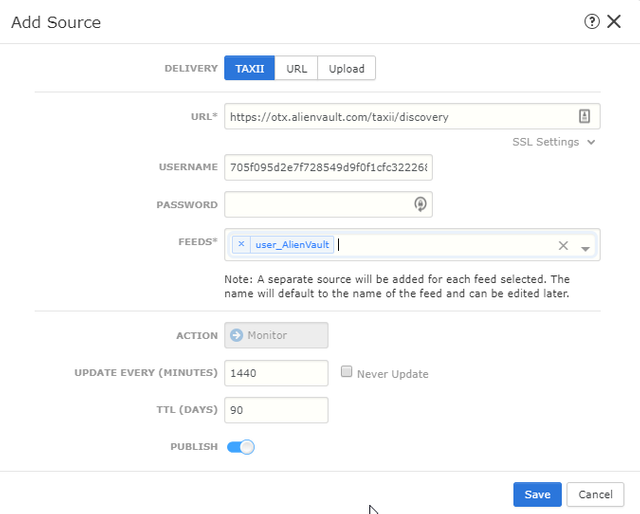
- Click on TAXII. You will be presented with the instructions on how to set up the STIX/TAXII feed.
- The discovery URL is: https://otx.alienvault.com/taxii/discovery
- The username is your API key. This is your OTX Key. There is no password needed.
- Go to Firepower Management Center and click on Intelligence -> Sources -> Add Source (+)
- Enter in the details and you should see the selectable feed populate.
- Click on Save
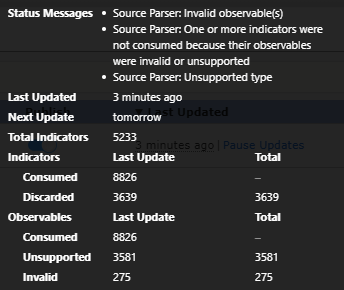
- You now have your feed added. At the time of this post, the feed had 5,233 indicators and 4,937 observables.
- The import did complete although with errors as some information was invalid or unsupported.
Hail A TAXII
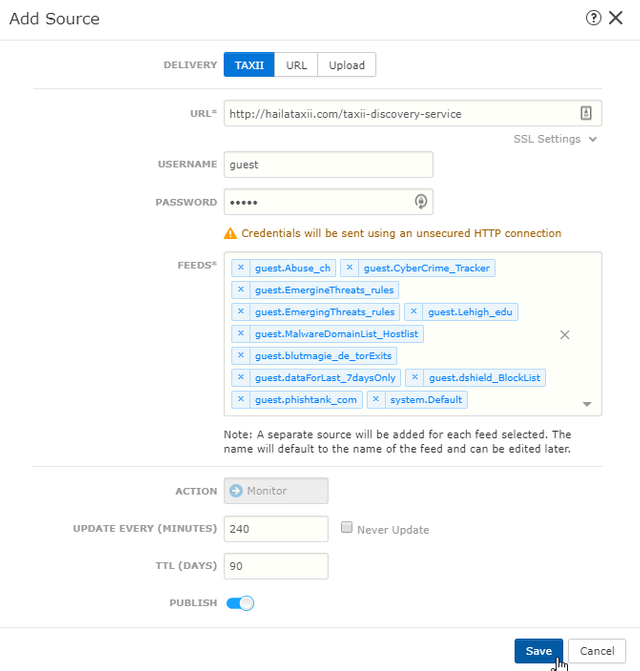
- Go to Firepower Management Center and click on Intelligence -> Sources -> Add Source (+)
- Enter in the Hail A TAXII discovery URL in the URL field. http://hailataxii.com/taxii-discovery-service
- A username and password is required. Use guest/guest
- Select your desired feeds.
- Click on Save.
Threatconnect
I registered an account with Threatconnect at https://www.threatconnect.com/free/. The verification email took a few hours to arrive.
One of my pet hates is for an email to arrive in my inbox with a password, even if it is randomly generated and requires me to change it on my first login.
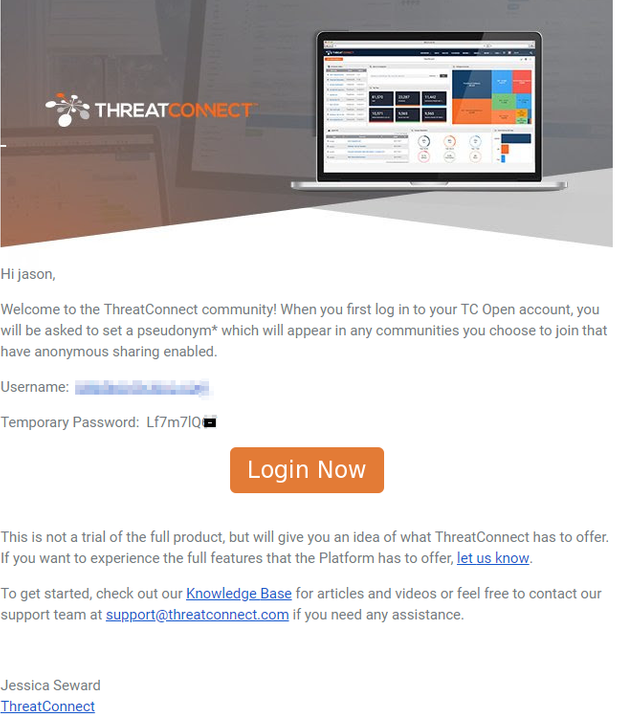
You need to create your STIX/TAXII feed on Threatconnect. I completed these steps following the CREATING AN OUTBOUND TAXII EXCHANGE FEED on their website. I contacted their support team to find it if the guide was out of date.
RiskIQ
I registered an account with RiskIQ to access their Community API. Unfortunately, it was exactly that. There was no STIX/TAXII feed for me to utilise. For those interested, you can create an account at https://community.riskiq.com/registration.
Critical Stack
From hslatman's' awesome-threat-intelligence I discovered Critical Stack's free intelligence feed. Critical Stack is a secure container orchestration platform.
- Sign up at https://intel.criticalstack.com/user/sign_up
- Critical Stack will email you with an activation link. You have three hours to click on the activation link.
Unfortunately, this platform only provided API access. At this stage, I gave up on some other sites that said they provided free feeds as there was no information if they supported STIX/TAXII.
Benefits of Threat Intelligence Director
- Detect and block Indicators and Observables with automated actions
- Accurate detection and incident reporting
- Improve your time to detection and time to respond to threats on your network
- Provides a single integration point for all STIX/TAXII and flat file intelligence sources
Closing Thoughts
After writing this documentation I walked away with a few questions and thoughts:
- Does the threat protection I obtain in Cisco's Firepower devices protected by Cisco's threat intelligence research centre Cisco Talos provide me with adequate protection without the need for Threat Feeds? Another argument could be made that if you are using open source threat feeds wouldn't Talos be using them as well? Let us suppose they do I would imagine there is curation done before disseminating this information down into their products.
- Are organisations benefiting from using commercial threat feeds? If so what security technologies are they using for threat protection that utilize those feeds and how are they correlating intelligence to search for IOC's across their enterprise?
- How often are organisations looking for IOC's specific to their environment and what tools are they using to do so?
- Another how-to post I am considering is utilising threat feed API's to download the data, parse/normalise the data to create my own local STIX/TAXII feed for FMC/Threat Intelligence Director.
- I contemplated doing a bake-off to see which threat intelligence feeds detect threats sooner than the other and the efficacy of their IOC's published. The pitfall of doing this review is that I would only analyse a small sample size based on the time I have and a feed/source that scored poorly this month could score higher in the following month.
Definitions
FMC - Firepower Management Center
FTD - Firepower Threat Defense
STIX - Structured Threat Information eXpression
TAXII - Trusted Automated eXchange of Indicator Information
IOC - Indicator of Compromise
Congratulations @cydera! You received a personal award!
Click here to view your Board
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @cydera! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit