
Index
Introduction.
- Origin of IONChain.
- Internet of things (IoT).
2.1. Weaknesses of the Internet of things. - IONChain.
3.1. Ionisation algorithm.
3.2. Generation of IONChain value.
3.2.1. Generation of value.
3.2.2. Verification of value.
3.2.3. Value evaluation
3.2.4. Value confirmation
3.3. Transfer of value in IONChain
3.3.1. Application layer
3.3.2. Service layer
3.3.3. Protocol layer.
3.3.4. Smart contract layer.
3.3.5. Blockchain layer.
3.3.6. Data storage layer. - IONChain network created for edge computing ( IONChain Fog Computing)
- A device, a coin, a code.
- Economic model.
6.1. Commercial value of the IONC token. - Cases of IONChain use.
7.1. Data security and privacy protection.
7.2. Exchange and circulation of IoT data.
7.3 Smart contract facilitates sharing the economy.
7.4 Edge computing optimizing the IoT user experience - Team members.
- Conclusion.

Introduction
Since the appearance of cryptocurrencies, blockchain technology has developed rapidly, becoming considered by the State Council of China as a technology that will provide the fundamental infrastructure for the next generation of Internet: Internet of Value, which leads to a inevitable fusion of both technologies.
Considering this, IONChain presents the concept of "A device, a currency, a code" that facilitates the integration of the IoT (Internet of Value) devices with the network of the IONChain block chain, where each device in the IoT network will be used as a mining machine, so each device that uses IONChain is subject to mining rewards.
In addition to this due to the use of blockchain technology, the data source will always be reliable and verifiable in the IONChain network. In addition, the value of the data is quantified and the data transfers are fast and secure.
This facilitates the emergence of IoT standards, unlocks a large number of new IoT application scenarios and drives the entire industry to enter the next level of development..
1. Origin of IONChain.
With the proposal of the ionization of the famous Swedish physicist Arrhenius in which he posits "that similarly to molecules and atoms, ions are also a fundamental particle in the formation of substances". IONChain takes this proposal as its basis and in the same way that the ion will act as the underlying link between all the IoT devices to support decentralized P2P communications between all the devices, which means that the IoT devices can exchange value between them Automatically, with the use of smart contracts, creating innumerable application scenarios for the entire industry, pushing into a new era.
2. Internet of things (IoT).
The IoT network is the key component of a new generation of information technology and is also the indispensable stage of development in the information age., Which means that when we reach this stage of the development of the Internet, the smart devices that we use will be connected to each other.
The IoT network is widely applied in the integration of networks through IntelliSense, identification technology, generalized computing and other telecommunications technologies. In addition, IoT is also referred to as the third wave of global information technology after computers and the Internet. IoT is greatly expanding the range of possible Internet applications.
Therefore, we can say that the innovation of the application is the core, and the user experience is the soul of IoT development.
2.1 Weaknesses of the Internet of Things.
It has been 20 years since the IoT concept was first proposed. Since then, technology has evolved and developed, making great progress.
However, at the stage where we are today, there are still some serious unresolved problems:
1) Business model for the IoT industry not yet established.
In every revolution of the information industry, a well-established business model is inevitably emerging. However, in the case of IoT we still do not have any model clarified. RFID is so far the only example of a large-scale IoT implementation. The main economic benefits of the introduction of IoT are derived mainly from the improved performance of several electronic components, while the huge data resources generated by IoT have not yet been applied in any large-scale business scenario.
2) Lack of data security and privacy protection.
Data security and privacy protection have always been one of the most serious threats posed by emerging Internet technology. IoT devices are collecting data from companies and individuals. It is possible to use this data to track the activity of companies and individuals, which causes concern among many people, especially since most of the IoT data is stored in the hands of only a handful of companies in the upper part of the ecosystem.
A single user can not control the private data he provides to the system. He / she does not know where it is going or how it is used. In recent years there have been cases of successful hacker attacks on those huge centralized storage servers where major companies store data.
3) Lack of interoperability between platforms.
The centralization of IoT data creates barriers for the exchange and circulation of data. The leading companies in almost all industries are rushing to bet their claims on the new frontier of the IoT Big Data market, hoping to take the initiative in this new chapter of the Information Age. However, it is often the case that many other companies that could potentially use this data are competitors with the great leaders of the industry. This creates a situation in which the exchange of real data is just an empty conversation: without it being exchanged and circulated, it is very difficult to extract its real value and realize its potential.
4) The shackles of cloud computing architecture.
In recent years, the increase in network bandwidth has increased exponentially. Cloud computing is now the mainstream in the IoT industry. However, for application scenarios that require real-time interactions, such as VR, industrial IoT and autonomous driving, IoT networks built in the cloud tend to see a delay of up to several hundred milliseconds from perception to execution, which is a response too slow for the purpose of control.
3. IONChain.
A blockchain backbone network for the IoT (Internet of Things), which is represented by the following:
3.1 Ionization algorithm.
The inspiration for the ionization algorithm comes from the formation of ions. Ionization is the process by which an atom or molecule acquires a negative or positive charge by winning or losing electrons to form ions, often along with other chemical changes. Similarly, the ionization algorithm separates two main functions of the block chain: value creation and value transfer. This will produce new business models after combining and separating the value creation layer and the value transfer layer. Under the technical architecture of the current block chain, the creation of value and the transfer of value combine, which has great practical value in certain cases.
The success of Bitcoin and Ethereum is based on this type of algorithm. However, these algorithms are not suitable for the future requirements of the growing IoT industry. The IONChain algorithms are designed to make it possible for each IoT device to become a mining machine, allowing them to create value constantly. However, since IoT devices come in all types and forms, the value created varies depending on the type of device and the function.
The requirements of the future ecosystem of IONChain can not be fulfilled if we follow the existing protocol, which is a combination between the creation of value and the transfer of value. Therefore, the IONIZATION algorithm was developed for IONChain, and the raison d'être of this algorithm is to separate the creation of value and the transfer of value.
Once the separation has been made, the value creation layer is solely responsible for creating the value. Each type of IoT device will have a specifically designed algorithm. Like the ions after ionization, the value created by different IoT devices in the IONChain network can be combined into new types of consensus algorithms that will "translate" the value generated in different scenarios into the unified standard expressed in IONC currencies.
Following this IONChain improve the way in which intelligent devices are used since the value transfer layer allows transferring value within the IONChain system. All participants of the IONChain ecosystem can freely exchange their value through the value transfer layer.
3.2. IONChain value generation.
The IONChain value generation process is divided into four layers:
3.2.1. Generation of value.
All IoT devices have a default value in the IONChain consensus protocol, they also have an IONChain identification code, which includes the manufacturer's information of the device, device identification and other related information. All information is stored in the encrypted device with a zero knowledge test algorithm.
Each of the IoT devices can be used as a mining machine, and the information on it can produce IONC coins after certain algorithm verification. All IoT devices integrated in IONChain communicate through the IMQTT protocol customized by IONChain.
The MQTT protocol was initially developed by IBM for communication between IoT devices. However, it does not include the value transfer layer. IONChain adds the value transfer function over the MQTT protocol, creating the IMQTT protocol. With the use of the IMQTT protocol, IoT devices can not only exchange data, but also perform value transfer.
To support the relatively weak computing capabilities of IoT devices, IONChain will help configure Edge computing centers. These will be the intermediary computing devices configured near the IoT devices. Connected to the network, they would provide much greater computing power than IoT devices alone. The use of this intermediate computing layer makes it more reliable for IoT devices to join the network and transfer their data and value.
The value generation layer is, therefore, a combination of IoT and Edge Computing services.
3.2.2. Verification of value.
This is similar to the consensus algorithm in other block chains. The relevant parties interested in the data provided by an IoT device must complete the value verification in a cooperative manner. Once completed, the value will be transferred to the next layer for evaluation. If the verification fails, the created value is returned as invalid.
3.2.3. Value evaluation.
The value evaluation layer is the second level of value verification. In this step, verification of the authenticity of the value is completed. This process is completed jointly by the relevant parties. This protection layer was configured to ensure that the IONChain system can counteract malicious attacks, such as double spending.
3.2.4. Value confirmation.
This is responsible for packaging the verified value and then passing the packaged information to the value transfer part, so that the value created by the IoT device is officially present in the IONChain system in the form of a digital currency.
3.3. Transfer of value in IONChain.
The transfer of value of the IONC HIN is divided into six layers.
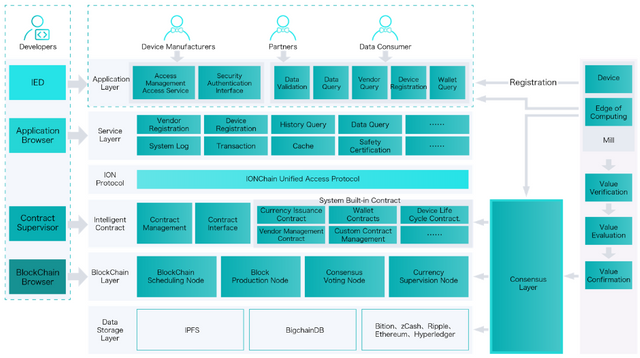
3.3.1. Application layer.
Application Layer is the user interface layer of IONChain. It provides REST API interfaces based on the HTTP protocol. Devices can request access to IONChain through this layer. The IONChain interface provides a verification function against counterfeiting of IoT devices and providers.
3.3.2. Service layer.
The service layer is an abstraction of the internal modules within IONChain. IONChain contains many components, which provide external interfaces through the server. The interface used by the service layer is usually a program instead of the end user.
3.3.3. Protocol layer.
IONChain provides a unified access protocol in the protocol layer, which includes consensus protocol, network protocol, currency exchange protocol, etc. IONChain provides external services through a unified protocol.
3.3.4. Smart contract layer.
Smart contracts are an important part of IONChain. They are the bridges that connect the blockchain layer with the applications. At the same time, smart contracts also play an "adhesive" role, which allows the requirements of the user and the consensus algorithms of the block chain to be combined. They make sure that users can legally and safely use the data stored in the block chain to create added value.
3.3.5. Blockchain layer.
To better adapt to the characteristics of the IoT network, IONChain applies some changes to the classic POS algorithm. By adding our modifications, we have called this new IPOS algorithm.
IONChain reviews the algorithm to better match the IoT requirements, creating the IPOS algorithm. The IPOS algorithm is the update of POW and POS, and is divided into two parts: choose a group of block producers and schedule the production. The election process ensures that stakeholders have final control because stakeholders lose more when the network does not work properly. The way in which people are elected has little impact on the way consensus is achieved minute by minute. Therefore, this document will focus on how to reach a consensus after the block producers have been elected.
3.3.6. Data storage layer.
IONChain provides two ways to store data in the blockchain, which are based on IPFS and BigChainDB.
PFS is an emerging standard for storing addressable file content. Content-addressable storage is a mechanism for storing information that can be retrieved based on its content instead of its location. In other words, all files stored using IPFS receive names derived from the hash of their content.
What this means is that the same file will have the same name on all computers, and the contents of that file can never change without changing the file name as well. It also means that when you download a file from a server, you can verify that it is the exact file you requested by recalculating the name based on the content provided by the server.
IPFS also provides a peer-to-peer network layer (P2P) that allows computers to discover and share files based on their deterministic names. However, this P2P network layer does not provide or guarantee storage, hosting or bandwidth. As it is currently structured, the IPFS network expects users to provide their own servers and related infrastructure.
On the other hand IONChain is also designed for future IoT networks that need to store business data. Therefore, IONChain presents BigChainDB as a business data storage engine to meet data investigation requirements. BigChainDB has some blockchain advantages, such as decentralization, immutability and asset registration and transfer.
4. IONChain network created for edge computing ( IONChain Fog Computing)
The emergence of edge computing technology comes along with the development of smart terminals, which have gradually attracted the attention of professionals in numerous industries. Many people are presenting cutting edge computing instead of cloud computing. However, it is better to see them as complementary. Under the right conditions, Edge can become a crucial optimization layer of the Cloud.
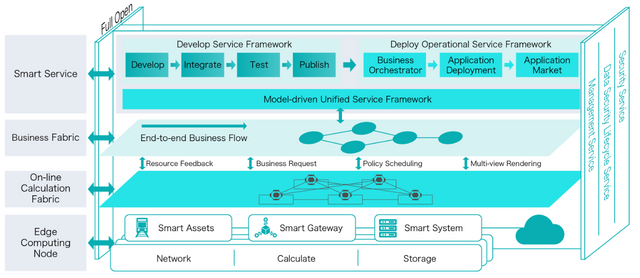
It has been proven at this point that the traditional cloud computing architecture can not provide the real-time response requested in many application scenarios. The use of cutting-edge computing in the industrial Internet of things, smart home technologies, vehicle Internet and other areas of IoT will reduce the latency of network feedback, improve the user experience and significantly expand the amount of scenarios of use cases.
Perimeter computing technology solves the long-standing problems of the IoT industry for privacy protection and adequate data security. Despite promises made by leading cloud service providers, data gaps still occur quite frequently and concern for privacy is omnipresent.
So IONChain, focuses on ensuring data security and helping facilitate the circulation, exchange and exchange of data. The intention is to break the barriers of the regular platform and establish the connection with IOT network nodes of any type or scale through decentralized blockchain technology.
Each of the IoT device manufacturers, IoT builders, data owners and applicants can take what they need within the IONChain network to form a complete IoT business closed loop.
IONChain perfectly meets the architectural requirements of Edge computing technology and can make full use of the computing power of the network nodes. These nodes will comply with the connection requirements nearby for the calculation and storage of IoT devices. This will lead to increases in the time efficiency of the perception process, computing and IoT response. There are a lot of application scenarios that require low feedback latency within the IoT network. The advanced computing solution could be the creative platform for these scenarios. These fields will have a negligible effect on cloud computing.
Depending on the characteristics of the perimeter computing, IONChain introduces the concept that "each device is a mining machine", which means that each of the IoT devices connected to IONChain will be able to extract and receive a remuneration through the "ionization algorithm". " The system will accurately calculate the precise rewards of the functions, the volume of data, the time (for example, the duration of the controlled terminal, the duration of the data collection, etc.) space (areas covered by the terminal or the group of terminals) and many other dimensions. IONC will encourage small or medium-sized companies with their own interests or even people to join IoT projects and boost the development of IoT facilities.
5. A device, a coin, a code.
IONChain has developed an innovative concept that we call "A device, a coin, a code". Our system was developed with the premise of integrating the current IoT hardware and infrastructure.
The "Device" part in our concept means IoT devices, "Currency" means IONC and "Code" is the unique identification code for IoT devices within the IONChain network. The identification code can be embedded in the hardware of the IoT devices to "stamp" the data from the beginning.
This feature, combined with the immutability of the records in the distributed IONChain ledger, makes all the data unique, reliable and, therefore, easily traceable. At the same time, IONChain will provide data conversion tools at the software level, data processing, data packaging and nodes for the Internet system of things already established. With complete data security, we can achieve forward compatibility of our design. This is particularly important considering the current fragmentation of the IoT device software market. We hope this also helps accelerate the formation of industry standards.
6. Economic model
6.1. Commercial value of the IONIC token
IONC is the official IONChain token. It can be used by different participants in the IONChain ecosystem.
IoT devices and access to data are the central parts of the IONChain ecosystem, therefore, the IONC token will be used to reward device and data providers. The annual supply of IONC tokens increases along with the demand for data access. However, the upper limit is preset.
With the fact of having a true IoT economy, the IONC token is an indispensable part of the IONChain system, since it is a unique and crucial part of its economic model.
From the perspective of the ecosystem:
The IONC token is the only authorized cryptocurrency, which unites all the participants of the IONChain ecosystem, which allows them to participate in the value creation process within the system. The overall value of IONChain will increase as more and more transactions and purchases will occur within the network. The IONChain mining rewards mechanism aims to increase the participation rate of all IONChain users, encouraging many smaller IoT devices to participate in the mining process, effectively decentralizing.
From the perspective of an individual:
To build a complete ecosystem, IONChain will distribute rewards to users in exchange for access to their IoT devices and the data generated. The privacy and data protection of the IONChain user is based on encryption and anonymity algorithms. The data load is rewarded with IONC tokens. Users can also spend the tokens to buy various value-added services within the ecosystem.
From the perspective of business entities:
With more and more IoT data gradually uploaded to IONChain, the value of the entire ecosystem for the analysis of large data and the use cases related to AI will continue to increase. Commercial entities will be willing to buy IONC tokens to be able to use them to pay for chain data analysis services. These services can help companies improve their business. They can also provide a basis for completely new types of business models.
Apart from that, the IONC token can also be used in the following situations:
a) Rewards for the IoT devices used as miners.
b) The more time the tokens have, the greater the possibility of being elected as a member of the IONChain council, subject to the Constitution and the requirements established therein.
c) Compensation for the cost of executing data search, statistics and intelligent analysis of contracts. Nodes that execute smart contracts will win prizes accordingly.
d) As the fuel to run DAPP in the ion chain, the node that runs the API called by DAPP will receive the reward corresponding to the running API consumption.
e) As a transaction fee to transfer the IONC currency between accounts, the billing node premium is paid accordingly.
f) Each IONC currency can track its origins and can save and track part of the data through the IONC currency.
g) Nodes responsible for communication between ION (access to IoT devices) in IONChain, and the accounting will obtain the corresponding prizes.
h) R&D spending for developers is a compensation paid by IONC users.
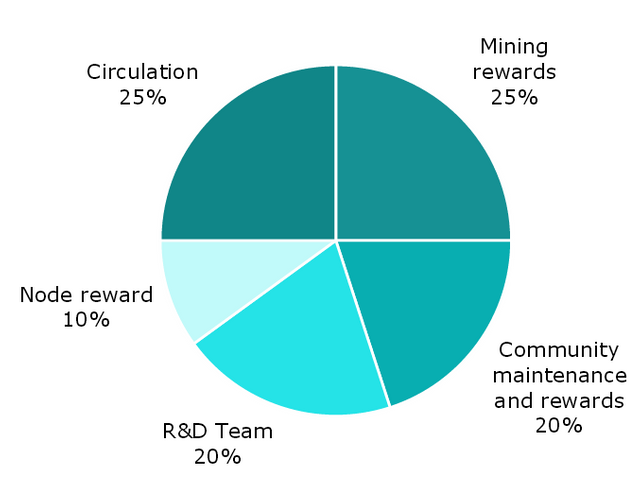
6.2. IONIC token distribution
The IONChain platform issues its own system token: IONC, the total supply is 800 million.
- Circulation 25%.
- Mining Rewards: 25%.
- Community construction and incentives: 20%.
- R&D team: 20%.
- Node incentives: 10%.
7. Cases of IONChain use.
7.1. Data security and privacy protection.
Case 1: In recent years, there has been great concern and condemnation for smart devices that violate the privacy of the person, in smartphones or other smart devices. The activities and regular behavior of the user are loaded privately in the background, and these data make clear user portraits for big data analysis companies to market and exploit. These resources will be used for targeted advertising, or they will be copied, sold in batches and even stolen by criminals. Therefore, those who control the authorization of centralized nodes have a lot of power. IONChain will interrupt this situation, making the IoT data flexible to store in local or distributed nodes with encryption to guarantee security, so that users have complete control over the data.
This private data can be used only by yourself or you have the option to exchange your data with other nodes that value them. Even if a particular node is being attacked or encounters a disaster, data will never be lost.
7.2. Exchange and circulation of IoT data.
Case 2: Company A has built a production line, but is not satisfied with the production efficiency after executing it for some time. The production needs to be optimized.
Through the IONChain data trading platform, company A discovers that company B in Asia has released data from sensors and production line video from a similar assembly line. Company A obtains sensor data and operating videos from Company B through IONChain and significantly improves its productivity. IONChain helps solve an interregional problem and eliminates technical barriers at a much lower cost.
Case 3: A newly created company on the Internet A wants to acquire personal information and the daily routines of car users to analyze data and develop a relevant business. This type of data was previously monopolized by the giants of map and navigation software. So far, it has been impossible for small businesses to collect this data using traditional methods.
The process of attracting traffic and then acquiring user habits would take too much time, so the company could not exist in the meantime, since it would not be profitable. However, thanks to the IONChain incentive model, some of the car users may be willing to exchange their personal data for compensation, which is automatically transferred to them through the use of intelligent contracts. Another company B can publish an application for data for the same type of data that company A has already collected and analyzed. In this case, company A may decide to sell or share the data and / or any relevant material to company B using the IONChain data exchange system.
7.3 Smart contract facilitates sharing the economy.
Case 4: Take, for example, a residential district near the CBD area, where there is often a high demand for car parking. Some of the homes are willing to rent their empty parking lots if they do not use them. By installing smart locks, households and those seeking parking can automatically control who uses the parking space through an intelligent contract and complete the transaction without human intervention. Simultaneously, the property management staff can connect to IONChain as another node. Once the transaction is completed, the benefits will be calculated and distributed accordingly. Transaction agreements within the system will depend solely on IONC. It is not necessary to involve any bank or other third-party institutions. No transaction fee will be required.
7.4 Edge computing optimizing the IoT user experience.
Case 5: A large-scale storage company is using RFID devices and managing data using a private cloud as a data storage center. However, as your business expands and the number of warehouses continues to grow, it is increasingly difficult to centrally manage large amounts of data.
This problem becomes more evident at the end of the month when it is necessary to perform some operations that require intensive use of the data, such as inventory verification or the clearance of incoming and outgoing stock. Response timeout problems can occur frequently, which negatively affects efficiency. The IONChain nodes deployed in different warehouses will perform data intensive operations on the Edge, which will greatly reduce the data request and feedback time. At the same time, the data will be automatically synchronized in a distributed and more efficient way using the IONChain blockchain.
8. Team members

- 16-year experience of consulting and system architecture.
- Technology team management experience with over 300 employees.
- Former CTO of Onechain Fintech, Founder of Vonechain Blockchain and IoT systems.
- Former senior director of Accenture.
- Integrated Technology expert, designed integration solutions for Huawei, China Mobile, SAIC and so on.
- Senior blockchain lecturer for MA courses at Fudan University.
- MBA of East China Normal University

- 15 years experience of programming and systems architecture
- Founder of technical block chain community Block chainBrother .
- Core developer of Hyperledger project in China.
- Participated in the development of Hyperledger Fabric Explorer open source project.
- First author of (Practical application of blockchain) published by China Machine Press.

- More than 10 years experience on IoT device design.
- Industries including agriculture, medical, intelligent scenic spot and intelligent gateway.
- complete top-level design of IoT systems and application scenarios.

- 20 years experience of television media & PR; received both provincial and national awards.
- Former COO & Chief Editor of ChainB (the leading blockchain media in China).
- Co-founder & Former VP of Marketing and Content Production in Uni-Live.
- Graduated from Fudan University.

- Co-founder of Shidian Capital.
- Over 10-years experience on marketing development and business management in telecommunication industry, worked for Huawei US, HTC China and China Unicom (Shanghai), etc. Practical experience on managing enterprises with various attributes and intercultural teams.
- More than 5-years experience in ecosystem build up for startup
companies. In 2011, started the first entrepreneurship NGO in Shanghai and is now a Deputy Chairman of Shanghai Entrepreneurial Alliance. - 2-year experience on cryptocurrency investment and blockchain projects management. Invested in more than a dozen different projects. Master of Information Technology from University of Birmingham, National Senior Entrepreneurship Consultant, traveled over six continents, enjoys long-distance running, exercises and
reading.

- Blockchain Technology & Security Encryption Expert.
- Hyperledger China core developer, participated in Hyperledger Fabric Explorer project development.
- In blockchain programming since 2014.
9. Conclusion.
IONChain aims to solve a wide range of current problems of IoT networks in terms of data security, data circulation, data exchange and data transactions, thus improving the efficiency of the entire IoT ecosystem.
On the other hand IONChain will have a significant impact on the IoT industry and will make the communication parameters of all the devices through the IoT network equal, regardless of the device used. By standardizing the way in which data is interpreted, it will allow them to implement their vision: "A device, a currency, a code".
While IoT technology has gone very far, there is still a lack of compatibility between devices and the overall standardization of their operation. IONChain is the ecosystem that will unify the technology of intelligent devices and allow them to truly become part of our daily life!.
To conclude, remember that IoT devices and access to data are the central parts of the IONChain ecosystem, therefore, the IONC token will be used to reward device and data providers.

More Information & Resources:
IONChain Website
IONChain Bitcointalk Explanation
IONChain WhitePaper
IONChain YouTube
IONChain Twitter
IONChain Medium
IONChain LinkedIn
IONChain GitHub
IONChain Steemit
IONChain Telegram

To participate in this contest please go here.
Twitter Bonus Post:
https://mobile.twitter.com/Kathee_21/status/1059975963293945857
ionchaintwitter
ionchain2018
This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit