


Just as the proven universality of Blockchain technologies becomes increasingly ubiquitous, it hence successfully perpetuates user friendly platforms that appeals to the mass public and techies, alike.
A decentralized cloud based system also has unexpected security benefits due to the encryption algorithms introduced into the system.
Yes, We all expect the best out of their networking and storage services, and in the past, the most viable method was the use of a centralized cloud. As companies set out seeking to find the fastest, easiest and most secure way of storing their data files, there has been considerable market development.
Blockchain alone, is not a computing cloud service, it does however, have the ability to act as a marketplace application that solves a few of the issues that are seen from platforms lacking the use of Blockchain technology, most importantly, the elimination of intermediaries.

Sharing information without a warrant

Some cloud providers usually share information with third parties if necessary for purposes of law and order even without a warrant. Which its users may not be aware of.
Privacy solutions
Solutions to privacy in cloud computing include policy and legislation as well as end users' choices for how data is stored.
The cloud service provider needs to establish clear and relevant policies that describe how the data of each cloud user will be accessed and used.
Cloud service users can encrypt data that is processed or stored within the cloud to prevent unauthorized access.
Cryptographic encryption /decentralized mechanisms are certainly the best options. In addition, authentication and integrity protection mechanisms ensure that data only goes where the customer wants it to go and it is not modified in transit.

INTRODUCING IAGON

IAGON utilizes enables to store big data files and repositories , as well as smaller scales of files, and to carry out complex computational processes, such as those needed for artificial intelligence and machine learning operations , within a fully secure and encrypted platform that integrates Blockchain, cryptographic and AI technologies in a user-friendly way.
IAGON’s major aim is to revolutionize the cloud and web services market by offering a decentralized grid of storage and processing. By joining the unused storage capacity in servers and personal computers and their processing power, we can create a super-computer and super data center that can compete with any of the current cloud computing moguls.
As more and more companies will recognize the benefits of IAGON’s platforms for storing files and processing them, the demand will increase and so will be the demand for the token – the way customers pay grid participants.

DIFFERENCE BETWEEN BLOCKCHAIN CLOUD COMPUTING AND OTHER TYPES OF CLOUD COMPUTING
| Decentralized | Centralized | - | ||
|---|---|---|---|---|
| secure | less secure | |||
| low cost | high cost |

5 Keys to Securing Your Files
While the valuable information that we all have stored on our hard drives may vary between sensitive company materials, financial records, personal banking and identification information, there is one thing that they all have in common the detriment that misuse of those files could subsequently bring.
1: Back-Up Consistently
It is undeniable that there are other ways to get certain information back if you were to have a completely unexpected disaster, however, there are items that will be lost forever, shall you neglect one of the most important steps in protecting yourself from lost data regular backups.
2: Secure Wireless Transmissions
When sending data files over a wireless network, you are opening up to additional areas of possible file interception, especially when operating over an Ethernet network. Because there is no need for physical access to the devices or network itself, a high gain antenna will be able to seize your private data files and/or gain full access to your entire network.
For these reasons, it is imperative that your access point is securely configured, this technology is provided by IAGON.
3: Password Protected Files
There are several applications that are used primarily for productivity, including Adobe Acrobat, Microsoft Office and things of the like, that will allow you to protect individual or collective files with a personalized passcode. In these cases, you are forced to enter the password provided prior to gaining access.
4: Data Protection Plan
When looking to strategically enhance the security of your data, there has been a high level of success surrounding the development of a data security plan/policy. This plan enhances the level of dedicated security that your corporation holds and sets the standard rules and steps to follow in the event of a data breach and/or hack.
Iagon has implemented a secure lake based on the blockchain’s unbreakable encryption technology. This hones in on file slicing and storage of small, anonymous and strongly encrypted files, ensuring the overall protection of data files, other various files and databases of any size. Additionally, the Iagon secure lake protects your data by ensuring the rapid retrieval and updating of any stored file.
With this technology, even in the event if information systems are breached, the data and files that they are using cannot be accessed, deleted or modified in any way.
5: Know Your Data
One of the most important, and often undervalued aspect of data protection is accurate knowledge of coveted data files. Assuming that a data breach occurs, would you know which files held your most important data? Would you know which files to work on protecting first?
You will be able to limit who has access to these files as well.

AMAZING FEATURES OF IAGON
IAGON Storage Services
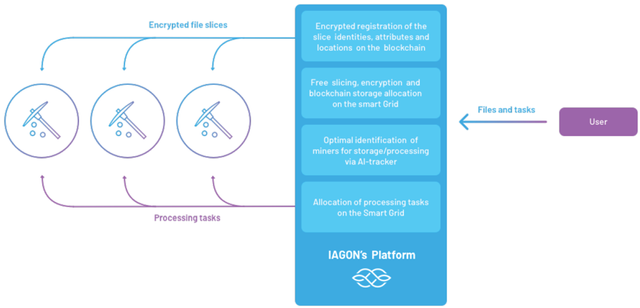
IAGON’s Cloud data storage is based on the delivery of files from local computers and servers into the remote servers and storage facilities that are obscure to the user, but can be accessed and managed at any time.
Thereby, the reliability of cloud storage services and the privacy of users (i.e. protecting the files from being accessed by any party other than their owner) are paramount to subscribing to and implementing any cloud services.

IAGON Computing Services

Artificial Intelligence is often used to generate better user experience. Artificial Intelligence is a set of advanced computational models and processes inspired by research of the human brain. These models and tools operate behind the scenes of many apps, websites and applications in a seamless way that does not interfere with the user’s interaction through the UI. WhitePaper, Page 6

IAGON Smart Computing Grid

The Smart Computing Grid can be compared to a power grid. It is the resource allocation system behind IAGON. The Smart Computing Grid executes the following functions:
Manage a network of CPU and storage providers as well as users who need those resources.
Manage the distribution and allocation of CPU and storage.
Determines underused resources and adds them to allocation pool for users to access.
Allows the CPU and storage providers to earn.
WhitePaper, Page 11

IAGON Ai-Tracker

AI research is a research standing on continuous research. If you can train your machines continuously you will get more data to fuel a more intelligent and accurate AI systems to create better solutions for present day conundrums.

IAGON Data Mining
IAGON is reliable, advocates for user privacy, a secured decentralized storage. It’s users don’t need to worry anymore about their data.
IAGON It benefits the miners providing processing power and storage space to the grid without
requiring efforts when their servers and computers are not used by them.
IAGON has strong authentication, which is a mandatory requirement for any cloud deployment. User authentication is the primary basis for access control,

IAGON Regulation Policies

There is also very poor legal system and laws guiding cloud computing by some companies, there is also very high cost of implementation, migrating an entire organization into cloud environment is extremely complicated, reliability, availability of services and data, complexity, costs, regulation and legal issues, performance, migration, reversion, lack of standards, limited customization, issues of privacy, sharing of information without warrant, consumer end storage.. but with IAGON all these problems are solved.

IAGON Reduced Cost Of Implementation

At present only those with the backing of powers-that-be will become successful in real life. That idea is toxic since you need to have connections in order to propel your vision into the mainstream conciousness. What if you don't have connections? What if your procedure is better than the mainstream powered ones? IAGON is your best choice since it caters to your needs every step of the way.



Hence, how can an individual benefit from sharing your computing power/data and storage?
I can benefit from sharing, by allowing my untapped resources to be used by those who are in dare need of it . Since I am not making use of my computer's full potential why should I prevent other users from tapping the dormant sector of my computer system.
Such noble idea in itself is beneficial specially to those who wanted to make use of supercomputer level processing speeds but is working on a very tight budget. Why should we allow selfishness to run the cyberspace when we can allow intellectuals to tap into resources which is obviously cheap, secure and powerful. This will also allow me to earn more since I am automatically leasing my unused resources for the benefit of those who wanted extra storage, processing speed or both.
A core fundamental quality of IAGON is that IAGON can provide is the affordability and availability of data storage and computing power for ordinary users like me and you whenever the need for the arises.

VIDEOS
a video made by me on IAGON being the Future we anticipated.
Introduction video


ROADMAP

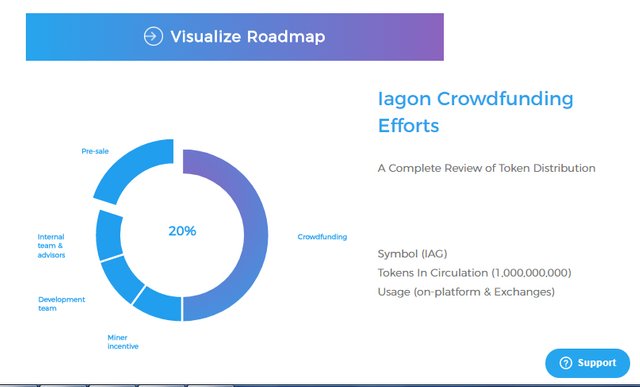
TOKEN DISTRIBUTDISTRIBUTION

GREAT TEAM

STRATEGIC PARTNERS

ADVISORS
.png)

MORE INFORMATION

IAGON Website
IAGON WhitePaper
IAGON BTCTalk
IAGON Steemit
IAGON YouTube
IAGON Twitter

This contest is organized by @originalworks to join click here
iagon2018
@contestbot
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
@cryptobyno, I do not understand anything written
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
My dear you can't understand if you don't know anything about technology, that's why I listed for more information you can check out the website of the company, it's basically all about current technology and blockchain.
To Break it short it's just like uploading a file on drop box etc.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
OK boss
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit