Background
I'm IT Engineer with 12 year of experience in the field, working in networking and servers and lately managing IT Services, i started my journey in computers in 1996 and crypto in 2017 and purpose of this is to help newbies (yeah, more newbies than me) to be safe in a proper way. My native languaje is spanish so please take it in consideration when read this xD
When cypto trading or investment hit your daily life, you need to start thinking in how to secure yours activities and investment, getting paranoid could be a positive behavior if we can achieve some goals in order to avoid risk and safeguard our investment. Security is a never ending task that needs to be continuously reviewed, tested and improved. To achieve that we are going to create an onion scheme
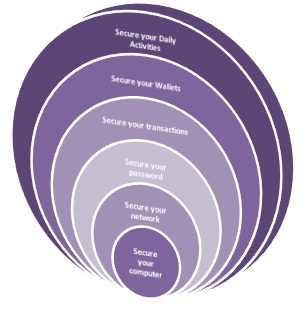
Topics reviewed in this entry include:
- Secure your Daily Activities
- Secure your Wallets
- Secure your transactions
- Secure your password
- Secure your network
- Secure your computer
Let’s start by the core of the onion
1. How to secure your computer.
Usually you should use a dedicated computer for high risk activities (like crypto trading/investment), so if you have a spare computer just format it you should start with a new and fresh operating system, use the one that is more confortable to your daily usage. Please take this as minimum considerations
- Install a new Antivirus: Even if Windows 10 includes Windows Defender, grab a free version of Avast Antivirus is a good recommendation.
- Keep System updated: Setup critical and security updates to download and install automatically. Also check drivers and third programs updates, ALWAYS there will be bugs ready to exploit in any kind of software, mostly in operating systems
- Avoid crack or patch third programs: NEVER crack or patch software in your trading computer (to be fair, try to avoid this in any computer). Try to find a reliable open source alternative or buy the software. For example Office365 subscription is not expensive, google docs is a powerful alternative. 7zip, avast, Google docs are good examples
- Web Browser: Ok, this is important… use at least Google chrome with extensions to avoid ads and hazardous content. uBlock Origin, Metamask and MyEtherWallet extension are good chooises. Tor Web browser also is a smart move.
And… what about not having a spare computer?.
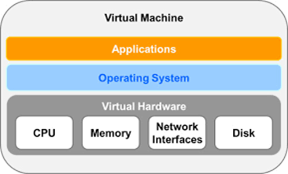
Virtual machines will be your best friend, a virtual machine, or VM, is an application that runs under Windows that creates an environment that simulates a completely separate computer. You need to assign resources like disk space, ram and processors to run a vm, the final setup will be determined by your current available resources. You can run several virtual machines with different operating system if you have the resources need it. Once operating system is installed, all previous advice needs to be followed. Pro tip, use NAT instead Bridge in network adapter setup, you will have an extra security layer.
There is a lot of information about virtual machines; pros, contra, tips, etc. As Always… dyor
https://www.shaileshjha.com/how-to-install-oracle-vm-virtualbox-5-in-windows-10/
Dude, I don’t have enough ram to run a virtual machine.
Jesus… ok, just grabs a Linux live cd/pendrive. Plug in your usb and reboot your computer, you will have a very nice desktop with all your minimal needs.
https://help.ubuntu.com/community/LiveCD
Well, that’s cover the minimum requirements for safeguard your computer. Let's move to the next onion layer.
2. How to secure your network
Wireless networks are inherently less secure — or at least more prone to being hacked — than wired networks. That’s simply the nature of a broadcast-based mode of communication: it’s much harder to hack into a router that requires you to physically plug in.
The minimum requirements for secure your network will include:
Change admin password: Many of you surely will have default password for your router. On top of that, even if you change the password, you are using the default ip rang/segment. Do yourself a favor and change the default password and ip address. Use complex password and change the 192.168.0.x address
Hide your SSID: According to IEEE 802.11 standards, every wireless network must have an identifier that’s used by devices to connect to that network. This is called the Service Set Identifier (SSID), but don’t let the faux-complexity fool you. It basically means “network name”. Every so often, routers broadcast something called a beacon frame. This is nothing more than a transmission that contains information about the network, including the SSID, and is meant to announce that this network exists. This is how your phone, for example, knows about all of the Wi-Fi networks around you. (Beacon frames are broadcasted about once every 100 milliseconds.) Think of it as your router shouting out to the world, “Here I am! My name is Cisco04022! If you can hear me, you can use that name to initiate a connection with me!”
And if you were to stop your router from shouting all of that nonsense, you probably think your router would effectively become invisible. If a network doesn’t broadcast its presence, then devices won’t know about it, and therefore won’t be able to connect. Right?
Not quite. The information is still being broadcasting between your router and everyone in the radio scope
Disable ssid broadcast will depend on your router brand; just search for enable/disable ssid broadcast in your router manual, as always RTFMEncryption: We are at 2018 and there is still people using wep encryption for wifi. You MUST change immediately to WPA2 and AES. Remember, your router is always broadcasting signals in all directions — but you can make these signals uninterceptable by encrypting them. Doing this, any signal meant for your computer will only be readable by your computer.
WPS and UPnP features: These are convenience features that have lots of big security vulnerabilities, mainly the ability to circumvent other security features (like firewalls), so we recommend turning them off ASAP.
NEVER use an untrusted network for trading!! Oh wait, never use an untrusted network for anything!!!
If you are using a public network (untrusted) like starbucks or free hotspot in town, then avoid crypto. If you need to do it anyway then use a vpn to secure your information.
Check ExpressVPN, not the cheapest and not the more expensive around internet, but reliable instead.
https://www.expressvpn.com/what-is-vpn/policy-towards-logs
3. How to secure your password
You know that Wikipedia has an entry with most common password right? Take a look
https://en.wikipedia.org/wiki/List_of_the_most_common_passwords
So, the firsts task for secure passwords is to use a secure password, avoid passwords like “password” or “qwerty” or “123456789” or “admin” for Christ’s sake. Use complex password instead

Recommendations
Don’t type your password in notepad or excel file or in your tissue: use proper software to keep your password safe and available at any time. Safe in Cloud will keep your passwords safe in an encrypted database in your dropbox or google drive. You can use your computer or mobile phone to access the password, the only requirements… you need to setup a password to unlock the software and see your password. Please use a complex one.
Use 2FA: Two Factor Authentication: also known as 2FA, two step verification or TFA (as an acronym), is an extra layer of security that is known as "multi factor authentication" that requires not only a password and username but also something that only, and only, that user has on them, i.e. a piece of information only they should know or have immediately to hand - such as a physical token. Usually 2FA will be enabled by using your phone with a software to get a One Time Password (OTP) but could also be a mail or sms with textcode.
Enable 2FA is a must in mail and Exchanges, use OTP over mail and mail over SMS
Also when you setup 2FA, you will see a paraphrase or a QR Code, safeguard that into Safe in Cloud or any other Password Manager, you will need it to restore if you lost or broke your phone.
4. How to Secure your Transactions
Ok, just follow the previous instructions. Secure your computer, use a good browser with proper extensions, use vpn and secure password.
Always check SSL Certificate: follow this guide https://www.howtogeek.com/292076/how-do-you-view-ssl-certificate-details-in-google-chrome/
Use your bookmark: Are you nuts? Nop… use your bookmark, don't click on links. There are a lot of phishing around crypto sites. Bookmark your sites and use it to access, avoid type or use browser or click links.
5. How to Secure your wallets
You put some bucks in crypto, you are not sure about trading or investing… well, if you trade or invest, you need to secure your investment. Store coins in the Exchange wallet is risky even more if you plan to store for long time a.k.a hodl, so we have a few alternatives, Paper wallet, Online Wallet, Computer Wallet and Hardware Wallet
What is this wallet? In a short answer… software that stores your public and private key. The wallet doesn’t store your coins, stores the keys to take the ownership of the coins recorded in the blockchain. Using your wallet you can send and receive coins.
- Paper wallet: Is a piece of paper printed with the public and the private key. Can be used as gift card or for takeout of the network yours bitcoins/altcoins.
- Computer wallet: This is a software that store your private and public key (obviously) and also an exact copy of the entire blockchain. Can be used to receive and send coins and depending of the coin, can be used to setup masternode, stack, private send, etc.
- Online wallet: Similar to computer wallet but online, you don’t need to download the entire blockchain. Example myetherwallet.com
- Hardware Wallet: usb dongle where private keys are often stored in a protected area of a microcontroller, and cannot be transferred out of the device in plaintext, are immune to computer viruses that steal from software wallets. Example Trezor and Ledger Nano
6. Secure your Daily Activities
- Simple one, avoid publishing sensitive information in social network, all the information that you publish can be used against you
- Don’t share your portfolio or bags
- Don’t use your crypto computer to anything that is not crypto related, and this include watch porn... dude, please don’t use your crypto computer for porn, this is like pee against the wind. You will regret.
- Don’t use google chrome with profile loaded, try to use chrome without putting your mail credentials
- Try to use Proton mail
- Don’t use the same password for everything
- Don’t use the same mail for every site or exchange. Create one mail for every exchange and don't put recovery information between those accounts
Be Careful, out there is full of guys trying to get your money and/or your information, waiting to take any chance to hit you without shame and mercy. Be paranoid and change your mindset to a more secure way, this is just the begining.
Thanks for taking your time reading this.
Hi. I am a bot that looks for newbies who write good content!
Your post passed all of my tests.
You get:
I also write bots and other code for crypto....
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Resteemed by @resteembot! Good Luck!
The resteem was paid by @greetbot
Curious? Read @resteembot's introduction post
Check out the great posts I already resteemed.
ResteemBot's Maker is Looking for Work.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
You were lucky! Your post was selected for an upvote!

Read about that initiative
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Hi. I am a bot that looks for newbies who write good content!
Your post passed all of my tests.
You get:
I also write bots and other code for crypto....
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Resteemed by @resteembot! Good Luck!
The resteem was paid by @greetbot
Curious? Read @resteembot's introduction post
Check out the great posts I already resteemed.
ResteemBot's Maker is Looking for Work.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @davidubilla! You received a personal award!
Click here to view your Board
Do not miss the last post from @steemitboard:
Vote for @Steemitboard as a witness and get one more award and increased upvotes!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit