
MIDAS Password Management
Introduction
A problem area for many users of todays technologies is that each account requires a secure password. Keeping encrypted data isn't easy in todays world. Many methods that password management systems currently employ are risky. Companies often store password data in a centralized serve. This provides a centralized location to attack, and a large reward for doing so.
Proposal
To solve some of these pains, I propose the inception of a on-chain password manager that provides decentralized password storage.
History
ZeroPass was created in 2014 and seems to be inactive now. They planned a decentralized password management system.
Stop typing passwords & printing security codes.
Use ZeroPass keychain & private key recovery manager.
Essentially it looks like ZeroPass aimed to add 2FA to passwords then store the passwords in a decentralized database.
Although it doesn't look like ZeroPass launched a coin and they are no longer providing updates.
Discussion
Encrypted passwords without context are rather innocuous. By associating password data to an individual block, and writing new encryption data for each password. At that point there could also be a mixing algorithm that would send the data from one node to the next.
If possible, this password software could include a Zero Knowledge aspect similar to ZEC/ZCL/ZEN coins. In a basic sense, Zero Knowledge means that information can flow accurately between two parties without 3rd party observers being able to discern whether the data transmitted was authentic or not. Meaning the transaction is equally possible that the transactor and receiver were faking the whole thing.
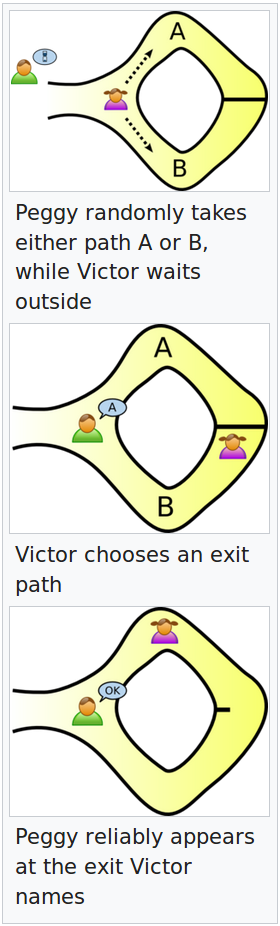
An easy example of this method is Alibaba's Cave. (left) There are two players that are attempting to share a secret without telling each other what that secret is. In this case, the secret is a password that opens a door inside the cave.
By repeating the process you see here, it confirms that the players know the secret because if the test was ever failed, it would call the other players knowledge into question.
If Peggy asks for Victor to appear in path B, and he appears at path A, or not at all, it cannot be said that Victor knows the secret (password).
What calls this transaction into question is external viewers may not know which path Peggy asks for, and no one will know the actual secret, only that there are two individuals utilizing the system.
Lets apply this to password management.
Our players: Password data, Password keeper Password requester, and the Cave. Our cave will be individually secure and algorithmically mixed between nodes. The Password keeper would repeatedly ask for the requester to show that they have the correct secret key. Even 25 replications is enough to show >99% certainty that the secret is correct without ever actually disclosing the true password. Once the keeper is certain that the requester is not an imposter, it would give encrypted data, which the requester would have to unlock using a 6 word passphrase. "ie. yes I do love encrypted passwords"
Your Post Has Been Featured on @Resteemable!
Feature any Steemit post using resteemit.com!
How It Works:
1. Take Any Steemit URL
2. Erase
https://3. Type
reGet Featured Instantly – Featured Posts are voted every 2.4hrs
Join the Curation Team Here
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
That's a good for decentralizing passwords database because it is becoming cyber threats to the whole world , anybody can hack into centralized database get useful passwords. Are you aware of dashlane software ?? Is it trustful thing??
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Your Post Has Been Featured on @Resteemable!
Feature any Steemit post using resteemit.com!
How It Works:
1. Take Any Steemit URL
2. Erase
https://3. Type
reGet Featured Instantly – Featured Posts are voted every 2.4hrs
Join the Curation Team Here
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit