

1 – Introduction
2 – Problem Statement
2.1 – Anonymity
2.2 – Scalability
2.3 – Pros and Cons of Major Privacy Coins
2.3.1 – Bitcoin
2.3.2 – Monero
2.3.3 – Zcash
2.3.4 – Dash
3 – BEAM
3.1 – What is BEAM?
3.2 – Features of Beam
3.3 – MimbleWimble technology and Zero-knowledge proof
3.3.1 – What is MimbleWimble?
3.3.2 – How does MimbleWimble work?
3.3.3 – Zero-Knowledge proof
3.4 – Beam blockchain operation
4 – Solutions to challenges
4.1 – Privacy solution
4.1.1 – Why privacy for a store-of-value coin?
4.1.2 – Customizable privacy
4.2 – Scalability solution
4.3 – Beam and other major privacy coins
5 – Applications and Use Cases
5.1 – Application and Use case for individual cryptocurrency investors
5.2 –Application and Use case for companies that accept online cryptocurrency payments.
5.3 – Application and use case for Government parastatals
6 – My video on Beam
7 – Conclusion

1 - INTRODUCTION
The invention of the blockchain technology gave room for the actualization of so many other possibilities, of which cryptocurrencies are the most popular. Bitcoin, the pioneer and most popular cryptocurrency, has remained relevant for over a decade because of its unique qualities of which “anonymity” is one of the most important.
However, recent researches have shown that this method has not been totally efficient at concealing the identities of participating parties. Research showed that if a user made a purchase on a shopping website by sending cryptocurrencies through his/her public address, this provides third party trackers with enough information to identify the transaction on the blockchain, link it to the user’s computer’s cookie, and further to the user’s real identity.Source
As a solution to this, there is need for a truly anonymous transaction mechanism that is also highly customizable and scalable, such that participating parties will not only have absolute privacy, but also have the power to decide whom they want to reveal whatever information to.

2.0 - PROBLEM STATEMENT
Despite all the strides that have been achieved by the cryptocurrency industry, it is still considered to be at its infancy stage, primarily because cryptocurrencies have been used mainly as a store of value and less as a medium of exchange.
It would be deception to assume that present day cryptocurrencies like Bitcoin, Monero, Zcash, Dash, and so on, have not done a pretty good job at serving as store of value. But despite their various achievements, there are still some shortcomings and challenges that currently exist in the cryptocurrency space, with respect to them serving as a store of value.
These challenges are categorized into two:
Anonymity
Scalability
2.1 – Anonymity
Right from the birth of the blockchain and crypto industry, the aim has always been for the system to function without the supervision of a centralized body. To further strengthen this goal of decentralization, the anonymity of the participating parties has been highly encouraged and sought after. Just the same way Satoshi Nakamoto(Founder of Bitcoin) has remained anonymous, anonymity has been one of the strongest selling points of the cryptocurrency industry.
However, from researches conducted, it has been confirmed that cryptocurrencies have not been as anonymous as we have been made to believe. Bitcoin for instance uses public keys for its transactions, with the reasoning that they can always be changed, and hence can’t be traced back to the user.
But from researches, which can be found here, it has been shown that public addresses, together with computer cookies, can be used to link back to identify the user of that public address.
Because of this loop hole, some investors have been discouraged from investing in these cryptocurrencies, since anonymity is one of the major qualities of cryptocurrencies that appeals to the public. This has in turn reduced the amount of investments that these cryptocurrencies would have received.
As a solution to this problem, there is a need for a cryptocurrency that makes available maximum anonymity, or better still, maximum customizable anonymity, where the user can give permission for people to have access to his data.
2.2 – Scalability
Scalability has to do with how efficient a blockchain can be when there is an increased amount of users of that blockchain per time.
For example, imagine you are a miner working with a blockchain that can accept 20 transactions per block per time. As time goes on, that blockchain becomes more and more popular, hence attracting more users. After some months, the amount of transactions sent to blocks increase to 1000. This will lead to transactions experiencing “waiting”.
A blockchain that can effectively handle the situation above is a highly scalable one, but the one that doesn’t, hence leading to long wait time is not scalable.
This poor scalability is found in majority of the major cryptocurrencies e.g. Bitcoin. Transactions experience long waiting time because of the high demand for block spaces. This has also led to high fees, since transactions with higher fees get attended to first, hence defeating one of the original goals of cryptocurrencies, which is to reduce the cost of financial transactions.
2.3 – Pros and cons of major privacy coins
In other to get a more in depth understanding of the privacy and scalability challenges facing the cryptocurrency industry, let us take a more in depth look at some of the major coins popularly regarded as privacy coins, exploring their strengths and weaknesses, hence seeing how these challenges individually affect them.
2.3.1 – Bitcoin
Bitcoin, the pioneer cryptocurrency, is the first ever introduced digital currency into the crypto space. Despite the fact that there are numerous cryptocurrencies in the market, Bitcoin is still the most widely used.
Pros
- Bitcoin provides anonymity to its users, through its use of public addresses to carryout financial transactions. These public addresses make it difficult for the identity of the user to be tracked.
Cons
Imperfect anonymity: Research which can be seen here, has shown that the identities of bitcoin users can be traced using their public addresses and computer cookies.
Delayed transactions: Because of Bitcoin’s poor scalability and high popularity, its transactions experience ‘waiting’, which is a situation where incoming transactions have to wait for transactions currently in the block to be processed. This leads to transaction delay.
2.3.2 – Monero
Monero is considered the strongest of the privacy coins Source, especially with the way it ensures privacy. Unlike bitcoin that uses public addresses that can be used over and over again, Monero uses stealth addresses, which are single use addresses that make it more difficult for addresses to be linked back.
Pros
- Monero has one of the most cryptographically secure networks. Through its use of stealth addresses, it provides one of the highest privacy levels in the cryptocurrency industry.
Cons
Imperfect anonymity: Research, which can be found here, has shown that there is a 45% chance that the identity of real Monero coins spent via stealth addresses can be uncovered.
Scalability issues: The Monero network experiences delays as more transactions get sent into the block. This is because each transaction requires six or more transactions to attain completion.
2.3.3 – Zcash
Zcash is founded on the zk-SNARKs (zero knowledge succinct non-interactive argument of knowledge) Source. As the name goes, zk-SNARKs is a technology that lets a process to be true, without verifying the process required to make that process true. It requires ‘zero-knowledge’ about the process, it just concerns itself with the final result.
Also, zk-SNARK transactions are memory-intensive. This means that they consume a relatively high amount of memory when processing transactions.
Pros
- Zcash has one of the most robust and cryptographically secure networks. Through its zk-SNARK technology, Zcash is able to provide high level of privacy during transactions.
Cons
- Imperfect anonymity: Despite the fact that zk-SNARK is a high security and privacy feature of Zcash, it is an optional feature on the network. This means that users have to consciously enable the feature for it to function. And from research, it has been shown that less than 10% of transaction have zk-SNARK enabled.
This means that the average privacy level during Zcash transactions are low, despite the availability of a privacy feature.
- Scalability issues: The memory-intensive nature of zk-SNARK makes it less scalable. As more transactions come into the blockchain, there is need for an increasing amount of memory to handle those transactions. This causes a scalability problem for the network.
2.3.4 – Dash
Dash is the weakest of the three privacy cryptocurrencies. This is because it is founded on a technology called CoinJoin. The CoinJoin technology is cryptographically weak when providing privacy for participants of a Dash transaction.
Pros
- Dash also has one of the most robust and cryptographically secure network in the cryptocurrency industry.
Cons
Imperfect anonymity: Dash is built on the CoinJoin technology, which is weak at providing privacy to Dash transaction participants. The CoinJoin technology is prone to both traceability and linkability.
Scalability Issues: Dash’s CoinJoin system has scalability issues, as it can take from hours to days for the CoinJoin system to handle waiting transactions.
From the analysis of Bitcoin and the three major privacy cryptocurrencies (Monero, Zcash, Dash), we can see that despite the tremendous job done by their various blockchain, they are still not perfect at providing privacy to the participating parties of their transactions.
Also, scalability remains a major challenge faced by these cryptocurrencies in their quest to effectively handle growth in volume of transaction.
There is therefore need for a new system that will provide solutions to these challenges, by providing perfect privacy/anonymity and also maximum scalability.

3.0 – BEAM
3.1 – What is Beam?

In the Cryptocurrency space, rather than going hand-in-hand, privacy and scalability are usually considered a tradeoff. This is because making a transaction private requires a lot of cryptography, and hence making it more heavy to store in a blockchain. In return, the transactions become more difficult to scale as the level of privacy increases.
Beam is a brand new revolutionary project that is redefining the way cryptocurrency transactions are being carried out. Beam is a fully decentralized scalable privacy currency. Beam achieves this by effectively providing absolute privacy and scalability to the cryptocurrency transaction process. Beam achieves this by means of a technology called Mimblewimble.
3.2 – Features of Beam
The Beam system consist of the following features:
Confidentiality: The Beam blockchain operates in such a way that no transaction information is stored on the blockchain.
Versatility: In addition to transmission of value, The Beam blockchain has the ability to process other transactions like escrow, time-locked transactions, and so on. It achieves this by means of its Scriptless-Script technology
Scalability: The Beam blockchain is highly scalable, by virtue of its implementation of the MimbleWimble technology. The blockchain does not experience delay in the processing of transactions.
Sustainability: BEAM is a highly sustainable project, by virtue of the fact that it is open-sourced, community-based, and backed by the Beam Growth Pool (20% of block mining rewards goes to this pool to incentivize development and promotion of BEAM) Source
Usability: The Beam blockchain boasts of a wallet that has support for both desktop and mobile. This wallet will facilitate the usage of the blockchain for conducting efficient transaction.
Compatibility: With the high level of diversification in the cryptocurrency industry, compatibility is of utmost importance. The Beam blockchain, through
3.3 – MimbleWimble Technology and Zero-knowledge proof
3.3.1 – What is MimbleWimble technology?
The name MimbleWimble is a reference to a tongue tying spell in the movie series Harry Potter, that prevented people from telling secrets.
But the technology MimbleWimble is a cryptocurrency technology that was created to provide scalability and also absolute privacy to the bitcoin blockchain.
3.3.2 – How does MimbleWimble work?
To understand how MimbleWimble works, we have to understand bitcoin’s UTXO (unspent transaction output model). When you send an amount of bitcoin from one wallet to another, you are not just deducting the bitcoin from one balance and adding it to another.
When you make a bitcoin transaction from your wallet to another, your wallet software is actually bundling up a group of inputs you received from other bitcoin transactions, summing them up into the bitcoin that you send.
Now, these inputs that your wallet bundles up are usually in their hundreds, and each of them have their own unique ID. To ensure cryptographic security, your wallet has to go through all these inputs one at a time, and individually sign them.
This is where the tradeoff of privacy and scalability begins. Individually signing these inputs provides high security and privacy, but also makes the blockchain heavy hence reducing scalability. This is reason why bitcoin has a scalability problem.
MimbleWimble solves this problem by taking a different approach. Rather than individually signing those inputs and outputs, MimbleWimble creates one multi signature from all of those inputs and outputs. The moment this multi signature can be produced, it then means that it was signed by all the parties involved.
One of the greatest strengths of MimbleWimble is that there are no public or private addresses in the system. The two parties that want to send money from one to another share something called a binding factor (shared secret). With the absence of addresses, the privacy of the system is highly maintained, as only the two parties involved in the transaction know what is going on.
Instead of downloading all transaction history and analyzing them individually like bitcoin does, MimbleWimble identifies transactions by means of binding factor, and analyzes these binding factor instead of indepth history analysis. This saves storage space, hence making the system highly scalable. Also, because of the use of binding factors that only the participating parties are aware of, the system has a high privacy.
3.3.3 - Zero-knowledge proof
The zero-knowledge proof of work is a technology that tremendously improves the scalability of a blockchain, by taking away the need to give in-depth analysis of why a verdict is true, by providing a reasonable proof why that verdict is true.
For example, lets imagine that you want to prove to a blind man that colors exist. So you give two golf ball of different colors to the blind man. He puts them behind his back and swaps them. Then he shows them to you to identify them. As long as you keep correctly identifying that he has swapped them, he will believe that they are of different colors. You don’t have to go into details to explain how the colors are different, but by your proof that he has swapped them, he believes that colors exist. This is a zero-knowledge proof.
In the same way, you can scale up a transaction by doing away with the un-necessary historical information that consume memory space, and stick with proof based verdict.
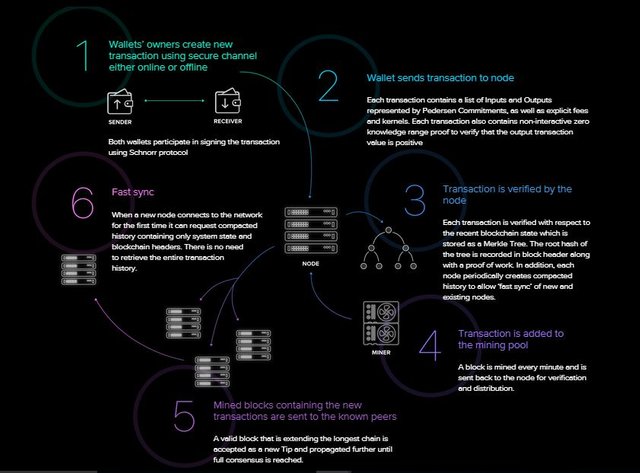
3.4 – Beam blockchain operation
The Beam blockchain implements the MimbleWimble technology from scratch using the c++ programming language, to provide privacy and scalability to its transactions. Just like Bitcoin that implements the proof-of-work concept, Beam implementing the memory-hard Equicash Proof-of-work algorithmSource
The operation of the Beam blockchain can be seen in the image below.

4.0 – SOLUTIONS TO CHALLENGES
4.1 – Privacy solutions
Beam blockchain provides absolute security and privacy to its transaction processes by its implementation of the MimbleWimble technology. The MimbleWimble technology makes use of binding factors, rather than public or private addresses. This binding factor is a shared secret strictly between the parties involved in a transaction, hence making the transaction un-linkable and un-traceable.
The binding factor acts as a ‘header’ for that particular transaction. This header is only available to the participating parties alone, keeping the transaction absolutely private.
4.1.1 – Why privacy for a store-of-value coin?
When a currency is used primarily as a store of value, privacy is of utmost importance. ‘Store of value’ is a phenomenon where a currency is used to hold or retain the value for services rendered.
For example, If I work for 2 hours on a job, and I get paid, the currency given to me should be able to retain the reward value for the job I performed. The currency should be able to retain that value, pending when I want to exchange that value for another form of value, which could be a product or a service.
4.1.2 – Customizable privacy
The Beam protocol is designed in such a way that the privacy level is highly customizable. Beam doesn’t only provide privacy, but also gives users the option to decide who has access to what information, and who doesn’t. This gives users more control over how they use their funds.
For example, imagine that you own a business where you have sponsors. You don’t want your transactions to be hidden from your sponsors, but you want them concealed from every other person. Through the Beam protocol, this can be made possible. Privacy of transactions can be customized to users taste, all on the same layer of blockchain.
4.2 – Scalability solution
While explaining MimbleWimble, we talked about binding factors being headers. These light headers are used in validating the Beam blockchain, as opposed to bitcoins strategy of downloading large volumes of transaction history to validate the entire blockchain.
With this, the validating nodes can validate all of history just by validating these light headers, rather than tracking every input and output involved in all transactions.
This saves a lot of memory space that would have otherwise been used for processing large volumes of blockchain history, instead allocating these memory spaces to process more transactions, and hence avoiding delay in transaction verification.
With this strategy, the Beam blockchain will be highly scalable, with little or no delays in transaction execution
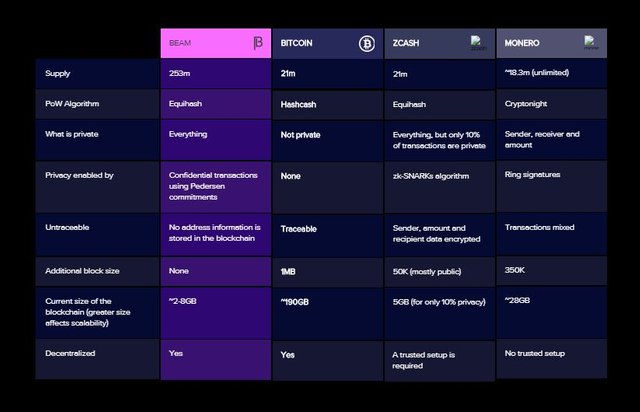
4.3 – Beam and other major privacy coins
Beam is not the first privacy coin concept in the cryptocurrency space. There are other privacy coins like Monero, Zcash, and Dash. But from what we have discussed above, Beam will give more privacy than these protocols, and it will scale better also.
Monero, Zcash, and Dash make use of very heavy cryptography, primarily because of their quest to make the protocol highly secure and private. Also, they store all their history in their blockchain, and hence have to be validated.
Beam on the other hand is private by default, and has high scalability.

5.0 – APPLICATIONS AND USE CASES
5.1 – Application and Use case for individual cryptocurrency investors
Application
One of the major appeals that the cryptocurrency industry had to the public, was its privacy feature. People wanted their financial transactions to be as secure and private as possible. Prior to Beam, researches have shown that the major privacy coins (Monero, Zcash, and Dash), were not absolutely private, bitcoin included.
With the help of Beam, individual cryptocurrency investors can now be rest assured that their investments will have absolute privacy. No other person will be able to trace transactions back to them.
Use case
Ben is a cryptocurrency investor. He invests in cryptocurrencies and also carries out online payments using cryptocurrencies. But Ben has a worry that his transactions could be used to trace back to him, and hence putting his wealth of cryptocurrencies at risk.
On finding out about Beam, Ben starts to use Beam for his transactions. Beam now avails Ben absolute privacy while performing his transactions online.
5.2 – Application and Use case for companies that accept online cryptocurrency payments
Application
It is becoming a latest trend for companies to accept payments online through cryptocurrency. But prior to Beam, most of these payments used bitcoin as currency of payment. Because of the delay caused by bitcoin’s poor scalability, it made the payment process sluggish and less efficient.
With the help of Beam, these companies can now have crypto payment systems that are efficient and quick. Issues of waiting for transactions to be confirmed will become a thing of the past.
Use case
Leam consulting receive online payments for their services through bitcoin. They have been receiving complaints from their customers that the crypto payment process is slow. Leam consulting have been looking for a faster crypto payment process.
On finding out about Beam, Leam consulting implements the Beam protocol, and begins to receive online payments through the Beam blockchain. Because of its high scalability, payment transactions were processed quickly, irrespective of the amount of current transactions.
5.3 – Application and use case for Government parastatals
Application
Most government parastatals deal with huge amounts of moneys. When conducting online payments, they try to make use of payment systems that provide high security and privacy. They don’t want people tracing back their transactions.
Prior to Beam, these government parastatals had their financial transactions accessible to hackers, who could use those data against them
With the help of Beam, these government parastatals can have maximum security and privacy while making their online transactions.
Use case
The ministry of roads and works of Sweden works with a minimum of 20 contractors a year while building roads. They send use amount of moneys to these contractors to carry out the road constructions. Because these transactions are done electronically, the transacting accounts are prone to being traced and hacked.
The Director of the ministry finds out about Beam, and introduces their contractors to the Beam blockchain. Now these contractors can get paid through Beam, with the ministry rest assured that the transaction has high privacy.

6.0– MY VIDEO ON BEAM
7.0 – CONCLUSION
The cryptocurrency industry has experienced a lot of developments on the qualities that Bitcoin- the pioneer cryptocurrency. These developments have led to the birth of so many coins, having so many advantages over bitcoin. Of all these coins, we have a group called privacy coins. These coins include Monero, Zcash, and Dash.
But despite their category as privacy coins, they still have some privacy shortcoming. They are not absolutely private.
Beam is a blockchain that will bring absolute privacy and scalability to the cryptocurrency industry. Through Beam, the cryptocurrency industry can truly regarded as private and scalable.

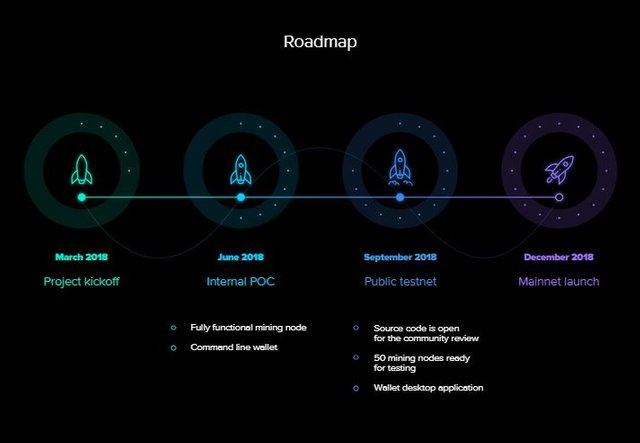
It is only a company that knows where its journey began from, that can know where it is going. Below is a road map of Beam, showing where they have been, where they currently are, and where they are going.
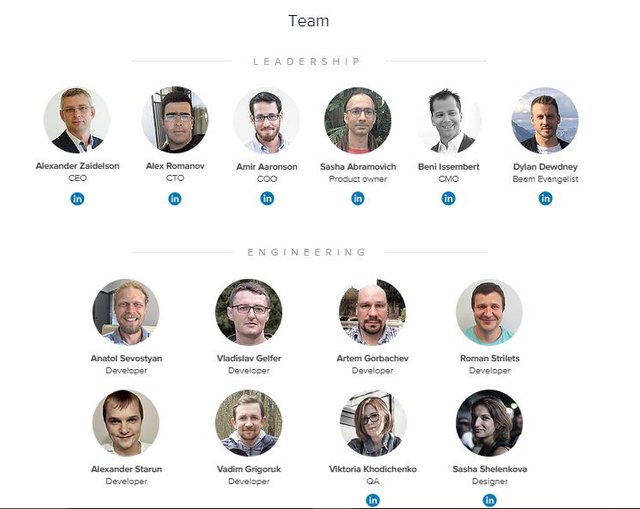
The Beam team is made up of first class engineers and entrepreneurs who are highly experienced in the field of technology. With 7 full time developers, a growing marketing team, and seasoned management, you can’t expect anything lesser than the best.

Beam has a strong advisory board, consisting of cryptocurrency veterans.

Above is a list of those who have invested in the Beam project.
If you need further clarification on any issue with regards to Beam, just do well to drop your questions in the comment section, and I will promptly attend to it.
For more information on Beam, you can visit any of the following channels:
. BEAM WEBSITE
• BEAM POSITION PAPER
• MIMBLEWIMBLE PAPER
• BEAM YOUTUBE
• BEAM TELEGRAM
• BEAM FACEBOOK
• BEAM GITHUB
• BEAM BITCOINTALK
• BEAM MEDIUM
• BEAM TWITTER
To participate in the contest, visit this link
Here is my Twitter link
beam2018
beamtwitter














It's neat not just fresh!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
This is elegant and appealing!!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Tremendously strong shot!!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Just fun :)
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Outstandingly graceful mate
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
That's amazing and engaging m8
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Minimal experience m8
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Magical design dude
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I admire your experience mate
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Coins mentioned in post:
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit