

1 – Introduction
2 – Problem definition
2.1 – Business model for the IoT industry still not established.
2.2 – Lack of data security and privacy protection.
2.3 – Lack of interoperability between platforms
2.4 – The shackles of cloud computing architecture
3 – IONChain
3.1 – What is IONChain?
3.2 – One Device, One Coin, One Code
3.3 – IONChain and Edge computing technology
3.4 – IONChain system architecture
3.4.1 – IONChain and Value Creation Process.
3.4.2 – IONChain and Value transfer
3.5 – IONChain token (IONC)
4 – IONChain solutions to defined problems
4.1 – Data security and privacy protection
4.2 – Creating a data trading market
4.3 – Realization of true data sharing economy
4.4 – Edge computing and blockchain technology to improve user experience
5 – Applications and Use Cases
5.1 – Application and Use case in Surveys IoT
5.2 –Application and Use case in Scientific Research IoT
5.3 – Application and use case in Agricultural IoT
6 – My video on IONChain
7 – Conclusion

1 - INTRODUCTION
Clap! Clap! With those sounds from Ana’s palms, the Christmas lights, fluorescent light bulbs, and 32-inch plasma TV in her living room turned on. Ana was showing off her smart home to I and four of our other friends on that beautiful Christmas morning. While we were still with her, having our mouths opened in bewilderment of what had just happened, she uttered the words ‘Car on’, and immediately, we heard a ‘beep, beep’ horn from her car. If it were not for the fact that we were in the 21st century, we would have taught it was magic.
While trying to persuaded her to tell us how she was able to control her home and car, she tilted her head rightwards while also using her hand to adjust her hair, she revealed the Bluetooth earpiece she had on her left ear. She explained that through her phone and earpiece, she was able use the internet to send commands to the devices in her home. This was my first experience of IoT (Internet of Things) technology.
The internet itself is a technology that has revolutionized the way we go about our daily lives. It possesses tremendous potentials and abilities with which advancements, solutions to challenges, and prosperity have been made available to the human race. No wonder it is regarded to as the 2nd wave of global information technology after computers. Through the internet, the world of information processing, transfer and storage have been improved to near perfection.
Speaking of the quest to achieve perfection, the internet is metamorphosing into an indispensable stage called IoT (which stands for ‘internet of things’), where smart devices all around the world are be able to seamlessly communicate and connect with each other through the IoT network, as exemplified in the case of Ana’s smart home above. Well deservedly. the IoT technology is also regarded to as the 3rd wave of global information technology after computers and internetSource.
Statistical data from IDC (an international data company based in the USA) show that in 2015, the overall investment in global IoT market was $736.9 Billion, with the number of IoT software carrying devices reaching a whopping 14.866 billion in that same yearSource . These statistics show the mind boggling potential that IoT technology possesses.
However, it was so unfortunate that Ana’s experience I illustrated above did not have a ‘happy ever’ ending. Her ecstasy at having a smart home was short-lived, as two-weeks after installation, the IoT network of the company in-charge of handling the data from devices in her home was hacked. The hackers were able to penetrate the network, secretly unlocking and trespassing into her apartment as well as those of other customers, and making away with many valuables.
The security challenge Ana faced above is one of the challenges that IoT technology faces despite the huge progress in its evolution and development. History will attest to the fact that IoT has taken information technology to the next level, by providing staggering inputs such as but not limited to pervasive computing and identification technology. However, it has some serious unresolved weaknesses that have hindered it from reaching its maximum potential.
As a breath of fresh air, the blockchain technology comes as one that emphasizes highly secure decentralized point-to-point connection, which has proven through time to be the antidote to hackers and insecurity of data. With the emphasis of IoT being the direct connection between objects and things, inculcating the blockchain technology and edge computing into IoT will surely be a winning combination that will place IoT in its rightful place as a global information technology.

2 - PROBLEM DEFINITION
From the experience Ana had above, we can see that despite the fact that IoT technology provided automated solutions that made life much more comfortable for her, thereby taking internet usage to the next level, it still has loopholes that if not resolved, will cripple any aspirations of IoT achieving the kind of mass adoption that computers and internet had.
These loopholes are as follows:
- Business model for the IoT industry still not established
- Lack of data security and privacy protection.
- Lack of interoperability between platforms
- The shackles of cloud computing architechture.
2.1 – Business model for the IoT industry still not established
From the inception of the personal computer and internet revolutions, numerous business models were made to create businesses from these technologies. These business models included companies like Apple computers (a personal computer hardware and software manufacturing company) and Amazon (an online e-commerce store).
However, it’s unfortunate that the IoT revolution has not been accompanied by any of such business model. It’s difficult to find large-scale deployment of businesses founded upon the IoT technology as was seen in the case of the computer and internet revolutions.
2.2 – Lack of data security and privacy protection.
In the U.S general election of November 2016, current investigations have shown that the data of over 20 million American Facebook users who were eligible to vote, were hacked and used to manipulate the outcome of the election.
Because the data of users in IoT are majorly stored on centralized databases, it places this delicate data at the mercy of the security protocols protecting these databases, which if not strong enough, exposes such data to hack and wrongful usage.
2.3 – Lack of interoperability between platforms
My favorite color is white. The possibility of me buying a white phone is higher than that of buying a red one. This is one of the numerous data regarding my purchase taste that could be of advantage to whoever wields it.
Being aware of the tremendous advantage user data can provide, Big companies in various fields are hastily scrambling for dominance of IoT Big Data.
This however has an Achilles-heel. Monopolizing this field will be a huge setback to the goal of real data sharing, in that big industry leaders in various fields which possess huge financial capacbilities, will monopolize these user data that would probably have been of better and more productive use in the hands of lesser financially capable competitors. This is because it is in the effective trading and circulation of these user data that its true potential can be maximized.
2.4 – The shackles of cloud computing architecture
When VR (virtual reality) develops to a point where surgeons can perform surgeries from a distance away by controlling a robot, lag in action execution will be seen as a costly price.
This is the current situation being faced in the IoT industry because of reliance on cloud computing. IoT networks built on cloud computing experience delays of up to several hundred milliseconds from perception to execution, which is too slow to be considered for effective application in real time operations.
From these listed problems, we can therefore see that there is need for a new IoT infrastructure that will take advantage of the properties possessed by blockchain technology, to provide highly secure and innovative solutions that will take IoT industry to its rightful place as a revolution of this dispensation.

3.0 – IONChain
3.1 – What is IONChain?
Taking a cue from the theory of ionization proposed by Swedish physicist Svante Arrhenius, which postulates that ions are a fundamental constituents of the formation of atoms and link together to form the atoms, IONChain act as a link between all the IoT devices within the IoT network.
IONChain is a non-profit foundation, founded in Singapore in early 2018Source. Through its blockchain-based smart contract protocol, IONChain will effectively provide highly secure and privacy driven decentralized P2P communication link between all the IoT devices connected to the network. Hence, IONChain will enable IoT devices automatically exchange value between each other within a highly secure and private network.
In other words, we can call IONChain the ‘ion of the IoT atom’
3.2 – One Device, One Coin, One Code
Before entering into the IoT market, the IONChain team conducted a thorough research on existing IoT networks, so as to come up with the most efficient way to connect IoT devices. The led to the concept ‘One Device, One Coin, One Code’.
The ‘Device’ stands for IoT Devices connected to the IONChain network. These devices have IONChain consensus protocols and IONChain identification codes stored and encrypted in them through zero knowledge proof algorithm. Through these identification codes, the data from these devices can be identified and traced in a unique and reliable way.
‘Coin’ stands for IONChain coin (IONC), while ‘Code’ stands for the identification code for IoT devices within the IONChain network.
Through this ‘One Device, One Coin, One Code’ concept, a universal standard can be created that will enable all types of devices connected to the IONChain network effectively communicate with each other. This will bring about tremendous increase in the speed and amount of value that can be shared between IoT devices connected to the IONChain, bringing about the quick mass adoption of the IoT technology.
Finally, the universal standard created above will enable the smooth running and universal functionality of dAPPs developed for the IONChain ecosystem, enabling them to be able to be integrated on all IoT devices connected to the IONChain.
3.3 – IONChain and Edge computing technology
Edge computing is a data processing architecture, where user-generated data are processed at the edges of the network, as close as possible to the source of user-generated data. The move towards Edge computing is mainly because of the increasing amount of networked smart devices in the IoT, meaning that these devices can serve as data processing stations (mining stations).
Rather than causing delay by sending time-sensitive data to centralized cloud computing stations, through edge computing time-sensitive data can be processed at the point of generation by an intelligent device.
Also, since through Edge computing user-generated data is processed close to the user, the data remains with the users, hence users having absolute control over their data, and can decide whom to reveal it to. Through this empowerment, users can earn financial rewards in exchange for their highly sought after data.
IONChain implements the features of Edge computing in its ideology that ‘every device is a mining machine’. The concept here is that each IoT device connected in the IONChain network can serve as a mining station and receive rewards through IONChain’s ‘Ionization algorithm’
Through these incentives, individuals and enterprises will be motivated to join IoT projects, hence earning rewards for themselves, and developing the IoT facilities in-turn.
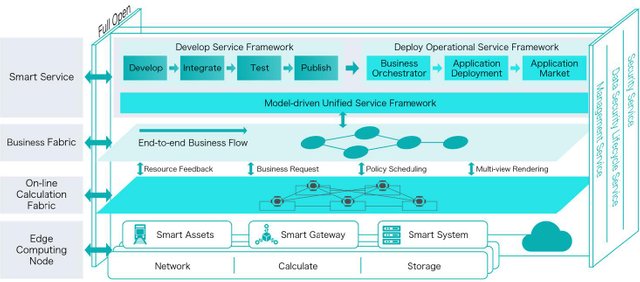
3.4 – IONChain system architecture
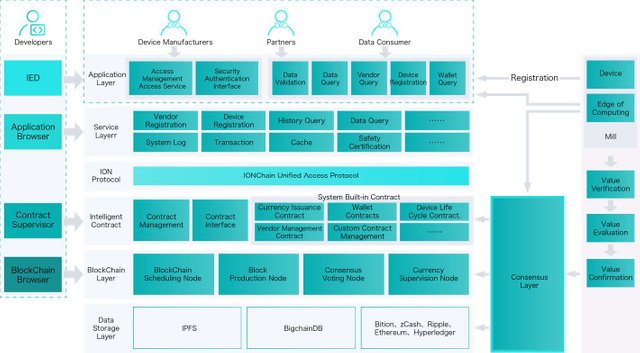
The IONChain system architecture operates a protocol called IONIZATION algorithm – a name derived from the theory of ionization proposed by Swedish physicist Svante Arrhenius.
This Ionization algorithm was formed, because from the research made by the IONChain team, they came to the realization that the existing protocol of combining value creation with value transfer was not effective and had loopholes, hence the need to separate the two processes as discussed below.
- Value creation
- Value transfer
3.4.1 – IONChain and Value Creation Process
The process involved in creating value within the IONChain network is divided into four parts:
- Value generation
Value generation has to do with generation of user data at the IoT device of the user, and the Edge computing centers close to the source of data (i.e. user). We explained earlier that the IoT device are the smart user controlled devices connected to the IONChain network, and serve as mining machines to earn IONC coins.
All IoT devices within the IONChain network communicate by means of a customized protocol called IMQTT, which enables IoT devices not only exchange data, but also carryout value transfer. With communication now in the picture, it then means that some form of computing has to be carried out – the reason why Edge computing centers are part of value generation.
After the data has been processed by Edge computing centers, they are passed on to the next stage.
- Value verification
Value within the IoT setting is the data from the user controlled IoT device. However, this data is going to be transferred to other parties that need them. Hence all parties involved in the transaction have to verify the authenticity of the value before it’s transferred to the next stage.
- Value evaluation
In order to prevent malicious attacks such as double spending, the value undergoes a form of verification confirmation, to ensure that all parties are fully aware of the contents and conditions of the transaction before proceeding to the next stage.
- Value confirmation
After the value has been verified above, it is then packaged and passed to the value transfer section for conversion into IONC coins in the IONChain ecosystem.
3.4.2 – IONChain and Value transfer
The Value transfer part is divided into six parts:
- Application layer
Adopting the REST API interfaces based on the HTTP protocol, the application layer is the user interface of the IONChain ecosystem. It gives users access to the IONChain ecosystem through their devices.
At the initial stage of the system development, the system will include the following built-in services: Data validation, Data Query, Vendor Query, Device Registration, Wallet QuerySource
- Service layer
Just as the application layer is a user interface for end-users, the service layer is an interface for components of the IONChain ecosystem and functions through the binary-based GPRC protocol.
The service layer is currently available only for the internal components. In the future, the IONChain team will consider making the service layer available also for the core nodesSource
- Protocol layer
At this layer, IONChain provides a unified access protocol, which include consensus protocol, network protocol, currency swap protocol, and so on.
- Smart contract layer
The smart contract layer is a very important layer of the IONChain ecosystem. This layer securely and safely connects the blockchain layer with applications. This layer protects parties involved in value trading, by ensuring the safety and legal usage of data stored on the blockchain chain.
If the contract is not satisfied, the value returns back to its source.
- Blockchain layer
This is the core of the IONChain ecosystem. To effectively function well, a customized algorithm called IPOS had to be formed for operation in the blockchain layer. IPOS algorithm is an upgrade of POW and POS algorithms. This upgrade has made it a robust and hard protocol to break.
- Data storage layer
IONChain provides two ways of storing data on the blockchain: IPFS and BigChainDB.
Resolving the concerns that large blocks of data leads to reduction in transaction speed, IPFS (Inter Planetary File System) storage enables IONChain to speedily carryout transactions, without compromising access to blockchain stored data.
It achieves this by storing data on multiple devices, while the storage process and transaction processes of data are made separate.
3.5 – IONChain token (IONC)
IONC is the official token of the IONChain ecosystem. IONC has a maximum supply of 800 million tokens. The IONChain team slated a time frame of 20years for the period of gradually releasing the IONC token. A time frame as this is further proof of the longevity of the project.
IoT devices connected to the IONChain ecosystem and which have participated in mining by trading value, will be rewarded with IONC tokens. The IONC token is the cryptocurrency upon which the economic model of the IONChain ecosystem is built.
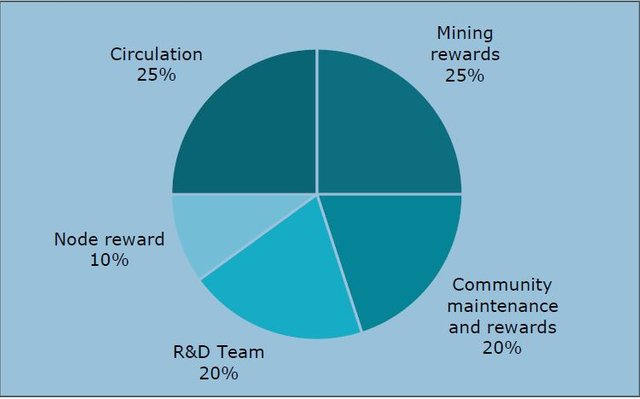
The image above shows the token distribution of the IONC token detailed below:
Circulation:25%
Mining rewards: 25%
Community construction & incentives: 20%
R&D Team: 20%
Node incentives: 10%
4– IONChain solutions to defined problems
4.1 – Data security and privacy protection
By virtue of its blockchain-based protocol, IONChain uses decentralized storage methods for data storage. These decentralized storages provide the data with high level of security and privacy. Within these decentralized storages, the data is encrypted, giving only the user full control of the data, hence further ensuring high privacy and security.
4.2 – Creating a data trading market
Just the same way that business models were created from the computer and internet revolution, business models can be created around the IoT technology, where users and enterprises with IoT devices can earn financial rewards by selling their data.
Since Big companies and enterprises are on the demand side for user-generated data, users can upload their data through IoT devices unto the IONChain, and in-turn get rewarded with IONC.
4.3 – Realization of true data sharing economy
For true data sharing to exist, all prospective clients must be given the same opportunity to have access to user’s data, and to effectively trade them.
Through smart contracts, enterprises can directly acquire user data from users in either device-device or device-user interactions. Smart contracts ensure that these transactions are carried out in a safe and legal manner. Anyone can sell or purchase data, giving everyone a level playing ground, and the opportunity to maximize their initiative in data usage.
4.4 – Edge computing and blockchain technology to improve user experience
To improve response time especially in real-time application, Edge computing technology is preferred over cloud computing, by taking computing from the centralized servers, unto the closer-to-source centers where computing can be carried out faster, hence leading to faster response time.
Combining Edge computing with blockchain technology within the IONChain ecosystem, gives the infrastructure the qualities of speed, security and privacy, tremendously improving user experience on the platform.
Finally, resolving the concerns that large blocks of data leads to reduction in transaction speed, Edge computing, blockchain technology, and IPFS (Inter Planetary File System) storage enables IONChain to speedily carryout transactions, without compromising access to blockchain stored data.
5.0 – APPLICATIONS AND USE CASES
5.1 – Application and Use case in Surveys IoT
Application
Through surveys, various kinds of companies can have ideas on what direction the taste of potential customer base is moving towards. Prior to the creation of IONChain, only the companies benefitted from the conduction of the survey. The users who provided these data had no way of quantifying or earning from this information.
Through the IONChain ecosystem, users can now earn financial rewards in the form of IONC, by granting access to their survey data to companies that have demand for them. By submitting their data to the IONChain platform, users have full control of who has access to their data – a feat that was previously not feasible
Use case
Steve runs a gym, and has about 100 clients who visit his gym weekly. These clients frequently purchase energy drinks while working out. Steve has been looking for a nice but within-budget-range way to appreciate his clients. His previous strategy was to give out discounts to them, which was reducing his profit margin.
He finds out about IONChain, and realizes that he could help his clients earn money from surveys conducted by energy drink manufacturing companies. Rather than conducting free surveys, he was able to negotiate with the companies, and they decided that Steve's clients will provide their data through the IONChain platform, hence enabling them earn some IONC tokens.
With this, Steve is happy because he achieves a win-win situation. He wins, his clients win, the energy drink company wins, and the IONChain platform wins.
5.2 –Application and Use case in Scientific Research IoT
Application
Technology has tremendously enhanced the speed and accuracy involved in scientific research. Majority of the equipment and apparatus used in scientific research and experiment are electronically built with microprocessor chips that process huge amounts of data.
However, these devices don't only process large amounts of data, but also generate large amount of data too. Prior to IONChain, these data only benefitted researchers within the confines of their experiment.
Through IONChain, researchers can gain added benefits outside the four walls of their experiment, by making the data their electronic devices generate available to those who demand them. By sending this data to the IONChain, researchers can have absolute control of their data, giving access to whomever they choose in return for financial rewards.
Use case
Ken is a physisist and specializes in advanced solar cells development. He has been conducting research in this field for over 10 years. Ken's lab consist of different apparatus that process various information , producing refined data that can be applied by solar cell manufacturing companies in building better solar cells.
Being a scientist, Ken has no direct financial benefit from these data produced by these machines, except to aid his further research.
On finding out about IONChain, Ken is elated at the fact that he can make financial benefits from data his apparatus generate. He immediately connects them to the IONChain ecosystem, making these data available to solar cell companies on demand. He is solely in charge of the data and decide who has access to them.
5.3 – Application and use case in Agricultural IoT
Application
Modern day agriculture has gone beyond hoe and cutlass. It now involves the use of technology and electronic devices to monitor plant behavior, predicting better ways of carrying out farming activities.
Prior to IONChain, farmers had no way of directly getting financial benefits from these Agricultural devices. These devices only provided research data, which when applied will lead to increase in farm yields.
Through IONChain, farmers can make financial benefits from the data that these devices generate. Agricultural enterprises who have demand for these data can pay farmers for them through the IONChain platform.
Use case
Evelyn owns a farm north of Chicago. Her farm is a modernized farm where she monitors the growth of her crops using modern technologies. The data from these devices help her make relevant modifications on her agricultural practices. This is all the benefits she gets from these devices.
On finding out about IONChain, she immediately connects her device to the IONChain platform, selling the data her device generates to Agricultural companies on the IONChain ecosystem.
She is happier and she reinvest these funds into making her farm larger.

6.0– MY VIDEO ON BEAM
7.0 – CONCLUSION
Living in the 21st century compels us to use smart devices that generate large volumes of data. This data is a definition of our personality, taste, style and so on. With this data in the hands of big companies, they can make well targeted sales that can increase their profit. The user does not gain from this mix, despite the fact that he generated the data.
What if we can sell these user generated data to these big companies that demand them.
This is where IONChain comes into play. It provides individuals and enterprises with the opportunity of making earnings from their generated data, rather than giving them out for free. The IONChain platform makes this possible.
Through its combination of blockchain technology and Edge Computing, users can securely and legally have their data traded.

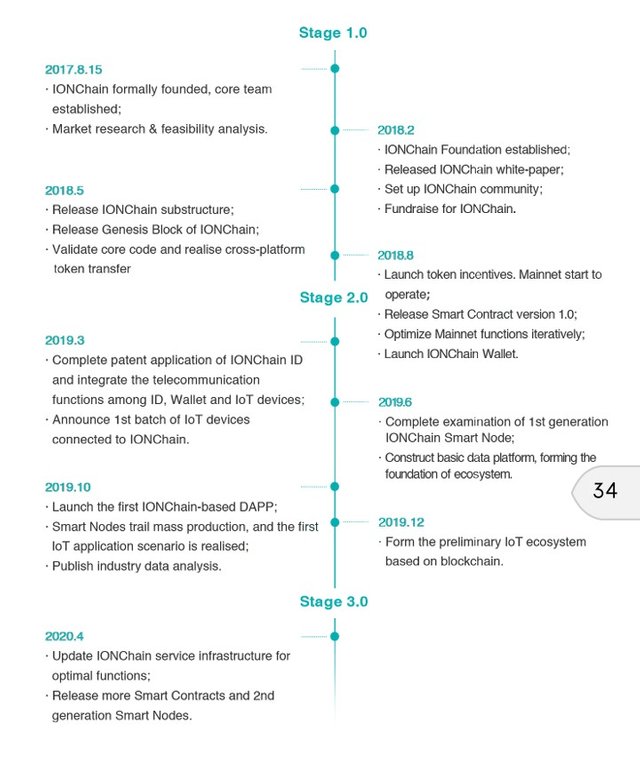
It is only a company that knows where its journey began from, that can know where it is going. Below is a road map of IONChain, showing where they have been, where they currently are, and where they are going.
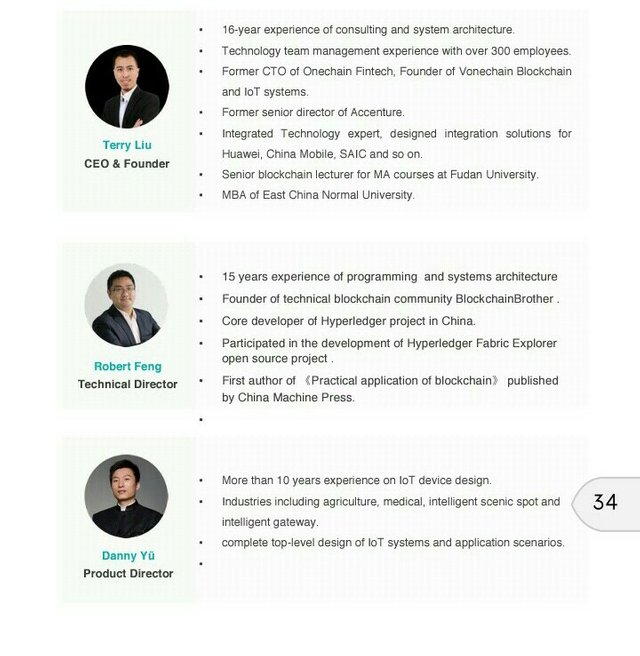
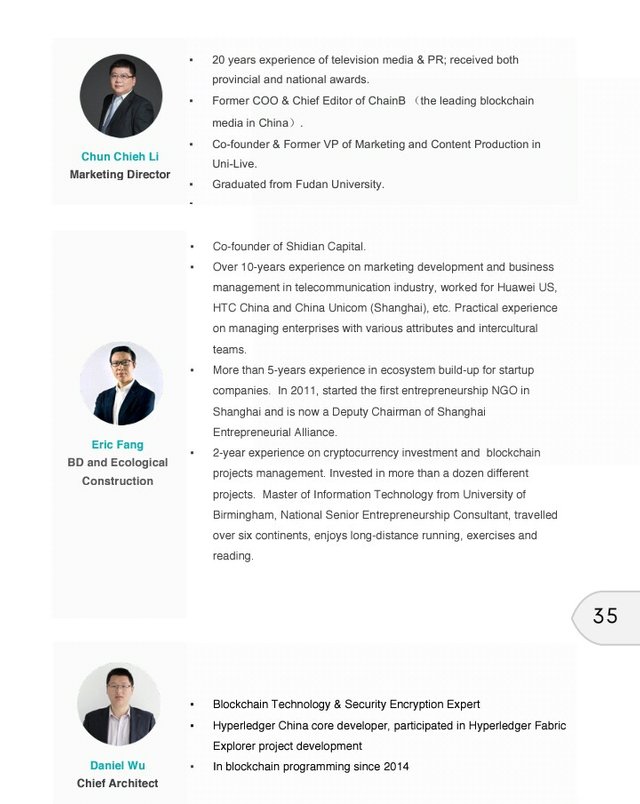
The IONChain team is made up of highly experienced professionals who have proven themselves in the blockchain space. Having gained experience from previous large scale projects like Hyperledger, they are well positioned to carry IONChain to the next level.
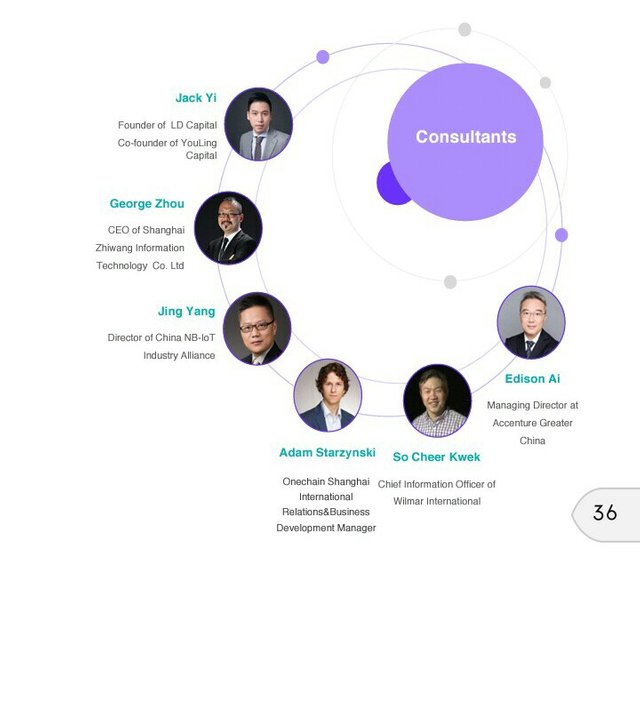
Above is a list of Consultants who provide invaluable expertise contribution to the IONChain ecosystem.
If you need further clarification on any issue with regards to IONChain, just do well to drop your questions in the comment section, and I will promptly attend to it.
For more information on IONChain, you can visit any of the following channels:
. IONChain Website
• IONChain Bitcointalk Explanation
• IONChain WhitePaper
• IONChain YouTube
• IONChain Twitter
• IONChain Medium
• IONChain LinkedIn
• IONChain GitHub
• IONChain Steemit
• IONChain Telegram
To participate in the contest, visit this link
Here is my Twitter link
ionchain2018
ionchaintwitter










This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @lucyc! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
Click here to view your Board of Honor
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!
Do not miss the last post from @steemitboard:
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @lucyc! You have received a personal award!
Click on the badge to view your Board of Honor.
Do not miss the last post from @steemitboard:
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit