
INTRODUCTION
Every day, you make yourself vulnerable.
If you hold multiple wallets and accounts in different exchanges, then your assets could be at risk.
Your phone knows every detail of your communications, your comings and goings, and your restaurant habits.
Your wrist monitor knows your heart rate and other vitals.
Amazon knows what you like to read and what brands of paper towels you buy on a regular basis.
Netflix knows your taste in films, and Google knows your political leanings and whether or not your kid might have the croup.
We live in a world where more than 50 billion ‘things’ are connected, where our refrigerators take photos of their contents and ping them to our phones, where our health records live in the digisphere, and where most of our banking, communicating, planning, driving and working prowess depends on the functionality of these electronics and their services.
The rewards can be great.
But with all of this good, great real-time data shuffling and Big Data collection and analysis comes a price: The more we rely on technology, the more information we reveal about ourselves… rendering us vulnerable to attack.
Vulnerability makes us less free. That’s why the best balance between convenience and security, in my view, always favors the protection of the user.
In this comprehensive guide, I’ll help you craft that balance.
I’ll share the latest developments in data security and data hacking, as well as the biggest risks that users of Macs, iPhones, Windows and Android users must guard against. And, of course, I’ll recommend the best techniques, programs and apps I know of -- strategies I have tried and tested -- that will help you avoid becoming a target of mass surveillance, a hacker, digital wealth such as cryptocurrencies, or even a disgruntled ex-spouse.
Technology changes at a blistering pace, but by following my simple steps, you can make yourself much less attractive to criminals.
You can mitigate the loss of a misplaced or stolen device, and you can make it more challenging for government agencies to invade your privacy without due process.
I can’t promise total invulnerability, of course. If your attacker has the necessary resources, he will find a way to access your data. And if you are the target of government agencies such as the NSA or CIA, the advice I’ll share will indeed make their job harder, but not impossible.
My aim instead is to thwart hackers who end up with your data as part of a breach of a company or service you trust; it’s also to teach you Internet street-smarts that will keep you from becoming a target for criminals.
Think of how you protect your car. An alarm system, anti-theft steering wheel locks and GPS tracking may not stop the most determined thief out there, but the combination may indeed deter someone seeking an easy target.
The same idea applies to protecting your digital self and digital assets.
In this 5-part series, I will be covering the following topics:
1- Techniques for creating strong, yet memorable passwords
2- How to detect and prevent phishing
3- The importance of two-factor authentication and how to set it up
4- How to perform local and cloud backups of your entire digital life
5- Data encryption: How to properly protect your information in this digital world
6- Internet encryption: Why additional encryptions is vital for your privacy and security
7- How to secure your communication via email, text, and calls
8- How to secure your social media habits
9- How to best protect and encrypt your most vulnerable entry point, your smartphone
10- My take on which OS (Mac VS Windows) have the best protection and privacy
1.0 PASSWORDS
Your digital security starts and ends with passwords.
Period.
It doesn’t matter how careful you are – that you encrypt all your data, or only use the most privacy-conscious anti-NSA web services – if your passwords are weak, none of this will help you one bit.
Many people think their passwords are great. After all, when they picked it, the website showed a long green bar and said “Password Strength: Strong” and made them jump through many hoops like adding numbers, lowercase, uppercase and special characters.
But as you will see, this song-and-dance ritual doesn’t necessarily mean your password is actually safe.
Even if you do know how to pick a truly secure password, chances are you don’t actually use one, because it’s impossible for you to remember it.
No longer. By the end of this section, you will know exactly how to create truly secure, random passwords that are unique to every service you use… and you’ll know how to remember them.
1.1 How Hackers Get Your Password
In order to create a secure password, you need to first understand who and what you are up against, how they operate and what their limitations are. Once you understand these things, it’s easy to reduce your risk and minimize the impact a hacker can have on you... even if he manages to get his hands on one of your passwords.
Hackers can obtain passwords in myriad ways, such as:
- They trick you into entering a password on a fake website that looks like a trusted one (such as your bank’s site). This is called phishing.
- They infect computers with malware that records everything typed into the keyboard.
- They hack into websites and nab passwords off of member databases.
- They even use automated programs that try out various combinations of usernames and passwords hundreds or thousands of times per second. This is brute-force cracking.
Unless you are being targeted directly, one of the most common scenarios is that your password is stolen from the database of a hacked website.
Here are some of the largest password leaks that I know about:
- In 2008, MySpace was hacked; eight years later, after messing with people’s data, hackers put up for sale data for over 350 million accounts;
- In 2012, LinkedIn was hacked; a hacker stole 6.5 million encrypted passwords, but that was just the beginning. In 2016, criminals put up for sale the usernames/passwords for 160 million accounts;
- In 2013, Adobe was hacked and over 150 million accounts were leaked; and,
- In 2012, around 68 million Dropbox accounts were hacked (data released in 2016).
As you can see, it can take years for the hacked passwords to be proffered around for sale. In the meantime, the original hackers start using them right away. And don’t scoff at the Myspace example; you might not use it anymore, but criminals bet that the kinds of passwords you used back then still apply. (And they’re often right.)
Some companies are more responsible than others and notify their users and customers as soon as they notice the hacks, that is, if they notice them at all. Others, however, don’t want to attract bad publicity and may chose not to announce a breach.
In other words, you might not have any idea about the breach of your data. The cases noted above are largest, publicly known ones. Think about the number of smaller websites that get hacked. You likely won’t hear about those incidents.
You can visit https://haveibeenpwned.com/ and enter your email address to see if there have been any known account hacks that involve you. Make sure to try older email addresses as well, as some leaks just coming to the surface date from 5-10 years ago.
Once a hacker acquires a password for an account, he will try to log in to web services such as Facebook, iCloud or email to steal more private data. If he gains access to your email, he can then break into your other accounts by resetting passwords and intercepting confirmation emails that other sites send.
Often, however, you may not even be the real target of an attack; instead, hackers might use you to access the prize: They’ll gain access to your email account and send specialized malware to a target who knows and trusts you.
People know not to open links from strangers, but doesn’t everyone open links from friends and family?
This is why, by practicing weak password hygiene, you are not just endangering yourself. You are also endangering your family, friends, employer, business partner, and your own business.
Example of Password Cracking
A good website doesn’t store your password in plain text. Instead they use a one-way hashing algorithm to convert a password like “ImSoSecure” into a hash like "15eb12a1dfbc4723b50f2bb1b7e6f835” and store it in a database.
“One-way hashing algorithm” means that it’s very easy to generate this hash, but almost impossible to revert it back into the original, plain-text password.
When you sign in to your account, the website converts the entered plain-text password into the hash and then compares it to the hash stored in the database. If they match, you are granted access.
Once hackers steal user information from a database, the hashed passwords are useless to them unless they can convert them back to the original plain-text password.
One way to do that is to run a brute-force cracking program that converts thousands of potential passwords into their hashed versions and checks if any of those hashes are in the stolen database.
If they find a match, they know the plain-text version of the password and can use it to log into your account or try it on other websites. These programs use lists containing millions of possible word combinations, ranging from “1234,” or “god” or “love” to complex words with upper and lower-case letters, numbers, and special characters.
Sound familiar?
Over time, a hacker’s word list becomes more efficient, quickly identifying password length, case, or other parameters that dramatically reduce the number of words they need to try.
If your password is a word or a combination of words that can be found in a dictionary like “FreeDog”, your password will be cracked within minutes... or even seconds.
No exaggeration. If your password is a slightly modified version like “Ch1cken!C0w”, which most websites will accept as sufficiently secure, it can still quickly be cracked.
Creating a random password forces hackers to randomly generate combinations of characters to guess your password. If your password is long and complicated enough, this process could take years or decades instead of minutes or hours. This is not only true for website passwords but also for when you want to encrypt data
1.2 What Secure Passwords Look Like
The best way to prevent this kind of attack is to use a long and completely random password.
The job of your password is to force the attacker to generate a huge list of potential random passwords.
The longer your password is, and the more varied the types of characters you include, the more potential combinations are possible, and therefore the longer it will take the attacker to crack it.
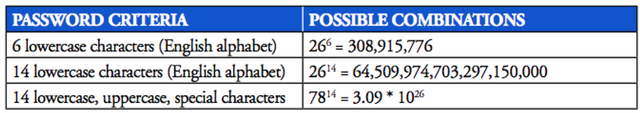
As you can see, the more complicated a password is, the more combinations are possible. Most attackers know nothing about your password habits and have to try passwords ranging from two characters to 14 containing lowercase, uppercase and even special characters.
The time and effort required to convert all of these combinations into a hash and compare it to the hacked database increases significantly.
The 4 Golden Rules for your Passwords:
- Unique for every website or account
- Long (At least 10 characters, preferably 14 or more)
- Random combination of characters (No real words)
- Special characters, uppercase, lowercase and numbers
Examples of bad passwords:
- Sc4rface55
- Aa556245622 (Your phone number, birthday, ... for example)
- My4wesomeSecure
Most of these would pass the standards of most website password checkers, and yet they are insecure.
Here are examples of good passwords:
- Mm10hwttp0tms!
- 14ss,b1jhtmu4gpapFvw
- T47wh5raylitf.
You may think it impossible to memorize these kinds of passwords, but as you will see in the following section, it can be easy to do so.
1.3 Techniques for Creating Strong, Yet Memorable Passwords
Step 1: Come up with a random sentence related to the purpose of the password
All you have to do is come up with a sentence that makes sense to you and is at least 14 words long. Make sure to include some words that start with uppercase letters.
A random sentence would be best, but you could also use parts of a song lyric, a poem, a quote, or a book passage.
My Example: I am glad that I am an Steemit subscriber and know how to protect my Account well!
Step 2: Write down the first character of every word
Now you simply reduce the sentence into a short and completely random password by taking the first character of each word.
My Example:
I am glad that I am an Steemit subscriber and know how to protect my account well!
Step 3: Convert some characters into numbers and special characters
Come up with a system where you can easily convert some characters into numbers and special characters.
You can, for example, turn some characters that look like numbers into numbers. You could come up with creative and unique ways to do this.
Replace the relevant characters of your password.
My Example:
t = 7
i = !
a = 4
!4g7!44Ss4khtpmaw!
Now you have a very long password (18 characters) with uppercase, lowercase and special characters.
Step 4: Memorize the password
To memorize this password, all you have to do is memorize your sentence and which characters you are replacing.
When you want to use the password, simply say the sentence slowly in your mind and type each of the first letters while remembering to replace some of them with numbers and special characters
At first it won’t be easy to remember and type the password correctly. Over time, however, the password will come to mind easily, and soon your fingers will type the password without your having to think about it.
I have used this technique with great success with my passwords, as has the rest of our team. The mnemonic works, and our passwords are all much less vulnerable for it.
1.4 Use a Password Manager

If you recall, one of the golden rules of passwords is that each of them has to be unique. This way, if hackers manage to nab one of your passwords, they won’t be able to penetrate your other web assets and identities.
You might have dozens, if not hundreds, of different accounts at different websites; using the previous password technique for each of them would be onerous or impossible.
This is where a password manager such as 1Password comes in. It allows you to save all of your logins, passwords, credit cards, bank accounts and other sensitive information in a database protected by very strong encryption.
The database can only be opened by someone who knows the master password, which means that even if an attacker gains access to the database file, he would be unable to access your passwords unless he also somehow accesses your master password.
There are several password managers, but I use and recommend 1Password, because it allows you to store your database on your own computer instead of in their cloud.
The app is available for Macs, Windows, iOS and Android.
Recently they have started offering a subscription service, which syncs the database through their cloud.
Don’t use it.
All that will do is make you vulnerable to hackers wanting access to the passwords of thousands of other customers.
Instead we recommend you purchase a standalone license from their website and set it up to sync between your desktop and your smartphone using dropbox.
Although your 1Password database (also called “vault”) will be stored in dropbox, nobody (including dropbox employees or government authorities), will be able to access your passwords, as they are protected by your master password.
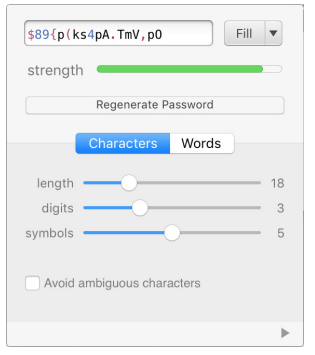
When you set up 1Password, make sure to create a secure yet memorable password with at least 14 characters, numbers, symbols, lowercase and uppercase characters.
Use the technique we described in the previous section. 1Password has a feature that allows you to generate unique, random and very secure passwords for every single website and account you have.
Use that feature to create a random password for every single one of your logins and make sure to set it up to use at least 14 characters, several digits and several symbols
Many websites also require you to set up security questions such as, “What is your mother’s maiden name?” in case you need to reset your password.
Don’t use the real answer. An attacker could easily figure that out. Instead, use a randomly generated password as the answer and save it in 1Password.
Whenever you want to log into a website, 1Password can autofill the password into the login form instead of you having to type it yourself.
If your computer gets hacked, the attacker could install a keylogger, a program that records your physical keystrokes. That could give him access to your master password, and thus the rest of your passwords. Therefore, it is vital to install all the latest security updates and use good antivirus software - or even run a system that is targeted less frequently, such as one on a Mac or Linux-based PC.
1.5 Password Summary
Password security is crucial and the foundation of your overall digital security. If you take nothing else away from this series, at least install 1Password and change all of your passwords to something unique and random.
Then create and memorize at least one secure password that you use only for 1Password’s master password.
To take it a step further, create a separate, secure and memorable password for each of your important websites and computer logins.
To make this task easier, you can make your secure password “variable”.
I used this sentence and password in my example:
I am glad that I am an Steemit subscriber and know how to protect my account well!
!4g7!44Ss4khtpmaw!
You can replace the “S” for Steemit with “G” for “Gmail”, “B” for “Banking” and create multiple unique passwords:
!4g7!44Gs4khtpmaw!
!4g7!44Bs4khtpmGw!
Since each password is technically unique, the attacker would not be able to use it to log into another service.
Here are the unique passwords we recommend you create:
- One master password for your password manager
- One password for your computer login
- One password for each of your critical websites (such as email)
PRO TIP: Stay Vigilant! The more passwords you create, the harder they will be to remember.
Use my system to help, but do nit reuse the same password in more than one place. If you find yourself tempted to do this, reduce the number of passwords you are trying to remember and change them to random passwords stores in your password manager. This will always be a better choice than using the same password in multiple locations.
One more thing to note: The more the attacker knows about you personally, the more he can reduce potential combinations.
Think about the amount - and type - of personal information readily available online or available to purchase: birthdays, family members and their birthdays, addresses where we've lived in the past, the name of our pets, phone numbers, and more. These tidbits are easy for an attacker to try, so never use them in your passwords or security questions.
It’s up to you to decide how much effort you put into this process and how much you modify it.
The more creative you get, and the more random and longer the sentences you use, the higher your security will be.
Part 2 of this series will cover how to detect and prevent phishing, the importance of two-factor authentication & how to set it up, and how to perform local and cloud backups of your entire digital life.
Brilliant!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @concepcionguzman! You have received a personal award!
Click on the badge to view your own Board of Honor on SteemitBoard.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @concepcionguzman! You received a personal award!
Click here to view your Board
Do not miss the last post from @steemitboard:
Vote for @Steemitboard as a witness and get one more award and increased upvotes!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @concepcionguzman! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit