
Recently I’ve made research about different cryptocurrency wallet types. Currently I’m using a popular web wallet but now I’m thinking to move to a hardware wallet.
In this article I’m going to make a synthesis of information I have found. Later I will write a new article comparing best hardware wallets of 2017 — beginning 2018.
Feel free to ask any questions, complete and share your experience with the community in comments.
A cryptocurrency wallet includes:
- Keys set (public and private key) to get access tokens stored on this wallet
- Algorithms managing these keys and allowing you to execute transactions in a cryptocurrency network
Hardware wallets — physical devices created to keep your cryptocurrency safe. Some online wallets also support hardware wallets.
Most of hardware wallets:
- Generate and store on the device a private key
- All the operations and transactions are executed on the device. It can display only the result of it: a hash of each operation.
- Have a screen to display some information
- Have one or more physical buttons
- Display transaction information
- Require a manual confirmation of an operation using a hardware button
- Allow to create a backup of private keys if the device is broken, lost or stolen
- Require to install manufacturer-provided software
- Works on all modern versions of Windows, Linux, MacOS
- Doesn’t work on Android
- Doesn’t allow to install any software on the device
- Require to set up a PIN code (or even multiple PIN codes)
- Support only few top cryptocurrencies
Let’s take a look at how different are hardware wallets from other wallet types.
Web Wallets
In this case your private keys are stored on remove servers. As a result, a user can lose his tokens if:
- His computer has been hacked and he lost the password
- A remote server has been hacked
- The company went bankrupt
- The FBI (or other authorities) seized company servers
- A software bug in the wallet
- An unauthorized person accessed a smartphone or computer when the owner was logged in
Desktop Wallets
A computer that has been hacked or infected by a virus can lead to a hacked wallet. A computer has much more vulnerabilities comparing to a hardware wallet.
Smartphone Wallets
These wallets can be separated into 2 groups:
- UI for web wallets. They have same kind of vulnerabilities as any other web wallet (see above)
- Autonomous wallets. In this case they are more or less like software wallets installed on a computer and can have same vulnerabilities.
A wide spread of mobile devices has lead to a rapid development of viruses for these devices which means that your money can not be in safe.
USB Flash Drive
It should be obvious that storing your private keys on a USB drive can not be safe, but people still use this approach.Here are few related problems:
- Any software can read or copy these private keys
- A malicious software can replace receiver’s address
- A lost or a theft can lead to a lost of all your tokens
However, it’s possible to increase the security using special USB drives requiring to enter a PIN code to access files.
Paper
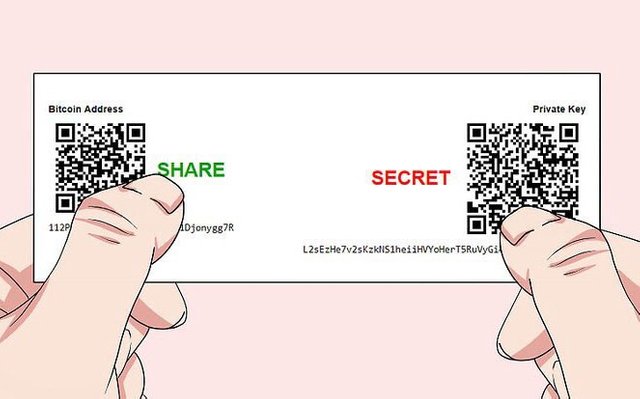
A correct store of a private key on a paper is quite secure but extremely inconvenient in use. Moreover, you will have to enter your private key in one of wallet types described above to make a transaction.
Risks and Possible Vulnerabilities of Hardware Wallets

At present (December 2017) there is no one known tokens stole from a hardware wallet. In spite of the fact that they appeared quite recently, they showed a good security level.
However, t’s important to understand that using a hardware wallet couldn’t be a silver bullet. There are few possible vulnerabilities. It’s important to take it into consideration choosing a hardware wallet and how much tokens you are going to store on it.
Replacing receiver’s address. A hardware wallet can not prevent you from sending your tokens to a wrong address. For example, a virus on your desktop can track your transactions and replace the destination address one it detects a large transaction. To solve this problem, it’s recommended to use a 2 Factor Authentication to confirm a transaction.
A bad random number generator. Hardware wallets depend on their intern random number generators. Unfortunately, to generate a real random number isn’t that easy. A bad random number generator can create such values that could be predicted by a hacker.
Bugs. The security of any system — hardware or software is based on the quality of its realization. Hardware wallets are not an exception. Firmware bugs could give to an attacker the access to internal structure of a wallet.
Compromised manufacturing process. Even an ideal firmware and hardware can’t prevent from an intentional or an unintentional intrusion during the manufacturing.
Compromised delivery process. During the delivery, it’s even easier to remove or replace some hardware or software elements so that it won’t be evident to a customer. According to some sources, many governments intercept and change different hardware products to open a backdoor.
Conclusion
So, using a hardware wallet can’t prevent you from all risks but a choice of a trusted manufacturer with a good reputation can help to protect your wallet from much more vulnerabilities comparing to software wallets.
It seems the ideal solution is to use an open source software together with an open to general use hardware such as Raspberry Pi or Arduino and a trusted source of the entropy such as a dice.
As I mentioned before, in my next article I’m going to present you my list of best hardware wallets of 2017 — beginning 2018. Feel free to comment and complete this article in comments below.
About the author. My name is Dan Podolan. I’m a blockchain developer and investor. Recently I’ve launched LiveMarketCap.com. It provides a live ranking of all the active cryptocurrencies and includes latest cryptocurrency news, market prices, charts and analysis. Feel free to help me make it better!
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://hackernoon.com/what-is-a-bitcoin-hardware-wallet-and-why-you-must-use-it-3fceeae2b21
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Well done @cheetah, it's also my article ;)
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit