If you are new to my Cryptology Series or are having trouble with any of the terminology, I encourage you to go to my blog and check out parts 1,2,3,4,5 and 6. I will link to the other parts of the series at the bottom of this post. Now let's get started!
First a quick review of some terms!
Cryptography Definitions & Concepts
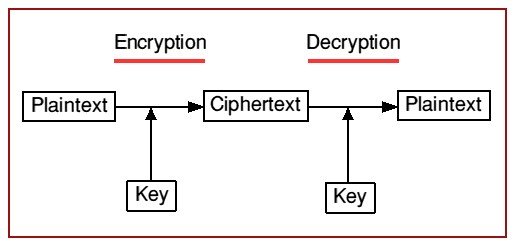
Plaintext- readable text
Ciphertext- unreadable/ encrypted text
Cryptosystem- a system or product that provides encryption and decryption.
Algorithm- the set of rules also known as the cipher, dictates how enciphering and deciphering take place
Key (cryptovariable) - Sequence of bits that are used as instructions that govern the act of cryptographic functions within an algorithm.
Keyspace - a range of values that can be used to construct a possible key.
Kerckhoffs’ Principle
The only secrecy involved with a cryptography system should be the key.
Making an algorithm public allows more people to test the source code and discover weaknesses which is still controversial.
Similar to open source vs compiled software debate.
Rules for Keys and Key Management
Key length should be long enough to provide necessary level of protection
Keys should be stored and transmitted by secure means
Keys should be extremely random, algorithm should use full spectrum of the keyspace
Key’s lifetime should correspond with the sensitivity of the data it is protecting
The more the key is used the shorter it’s lifetime should be
Keys should be backed up or “escrowed” in case of emergencies
Keys should be properly destroyed when their lifetime comes to an end
Key Management Hardware
Trusted Platform Module-an international standard for a secure cryptoprocessor, which is a dedicated microprocessor designed to secure hardware by integrating cryptographic keys into devices.

Key Management in Cryptocurrency Example
Most of the principals above can be applied to crypto currency key usage and can also help you understand why your Private Key is so important.
Let's look at one specific example of how a hardware wallet manages your private keys.
My hardware wallet of choice is the KeepKey, you can purchase your own with a link I will provide at the end.
KeepKey

KeepKey Key Management
Does KeepKey ship with pre-determined private keys?
KeepKey does not ship with any private keys. Before you can use your KeepKey, you must initialize it. During initialization, your privates keys will be generated using entropy provided by the computer client, combined with entropy generated by the KeepKey. This method ensures that KeepKey is generating unique and unpredictable private keys.
Can my private key be removed from the KeepKey by a thief?
Your KeepKey uses a very limited protocol to communicate with the computers it is connected to. Private keys are never exposed in this protocol.
The micro-controller in KeepKey is set to highest level (2) of read protection, which is enabled during manufacturing. This prevents access to its flash memory (where private keys are stored) with externally attached debug tools. For additional security, PIN protection is offered during initialization. This prevents unauthorized users from reviewing balances and transacting on your KeepKey.
An optional passphrase can be used to encrypt your private keys, so even if the read protection feature of the micro-controller is circumvented, your private keys remain safe.
The KeepKey comes with a ARM® Cortex™-M3 and a TRNG (Hardware-Based Random Number Generator).
The TRNG is a device that generates random numbers from a physical process, rather than a computer program.
"The major use for hardware random number generators is in the field of data encryption, for example to create random cryptographic keys to encrypt data. They are a more secure alternative to pseudorandom number generators (PRNGs), software programs commonly used in computers to generate "random" numbers."
I recommend using a hardware wallet like KeepKey for maximum security.
I hope this post gave you a better foundation of understanding why key management is important and the best practices for keeping your keys safe.
If you had any trouble with terminology or the concepts involved check out the other parts of my series
Cryptology Series Part 1: Getting the Basics
Cryptology Series Part 2: History of Cryptography
Cryptology Series Part 3: Strength Of Cryptosystems
Cryptology Series Part 4: Methods of Encryption
Cryptology Series Part 5: Types of Symmetric Systems
Cryptology Series Part 6:Types of Asymmetric Systems
The next and final part of my series Part 8, will focus on Quantum Cryptography!
If you are interested in buying BTC,LTC or ETH check out Coinbase, you will get $10 of free BTC after your first $100 BTC purchase, using the link below.
Coinbase.com
KeepKey Hardware Wallet, the wallet I use.
KeepKey
If you want to stay up to date on crypto news follow my blog @digicrypt.
DASH: XgQ9NBonMoCPKhF37agY4W8zk7gwQFnwGV
Litecoin: LfqygtBxy3AJgEpTnTMUYGEoTYEcED8YPZ


Another solid, informative post by Digicrypt! TRNGs are where it's at - never trust PRNGs!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks! Haha Amen!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
This is awesome, I am not a tech savvy person but I love learning about how the crypt world operates. Is so ingenious! I specially love the crypt technology because it makes me feel like I am part of a revolution. Like we are the good guys from the Matrix or something like that. =P
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks I am glad you enjoyed it! Goodluck on your journey Neo ;)
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
lol, thanks =D
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Good info and read...thanks
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thanks for reading and taking the time to comment!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Indeed awesum stuff, thank you for this series keep up the good work & look forward to next time on Rouge Money :)
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thank you! Always great to hear from a Rogue Money listener :)
I am working on another project that you might like, should be out next week!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Very informative series. I am really looking forward to the next part.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thank you! Yeah the next part should interesting Qunatum Cryptography is pretty crazy!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
I posted news of a quantum computing breakthrough today. Please take a look.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Thank you for the info, very informative series!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
You are very welcome and thank you!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit