
A zero-day vulnerability in Telegram Messenger allowed attackers to spread a new form of malware with abilities ranging from creating a backdoor trojan to mining cryptocurrency.
A zero-day vulnerability has been discovered in the desktop version for end-to-end encrypted Telegram messaging app that was being exploited in the wild in order to spread malware that mines cryptocurrencies such as Monero and ZCash.
The attacks take advantage of a previously unknown vulnerability in the Telegram Desktop app for Windows and were spotted being used in the wild by Kaspersky Lab.
Researchers believe the Russian cybercriminal group exploiting the zero-day were the only ones aware of the vulnerability and have been using it to distribute malware since March 2017 -- although it's unknown how long the vulnerability had existed before that date.
The flaw has actively been exploited in the wild since at least March 2017 by attackers who tricked victims into downloading malicious software onto their PCs that used their CPU power to mine cryptocurrencies or serve as a backdoor for attackers to remotely control the affected machine, according to a blogpost on Securelist.
The attacks have also been seen to steal Telegram directories from victims, including information about their personal communications and files sent and received.
The vulnerability resides in the way Telegram Windows client handles the RLO (right-to-left override) Unicode character (U+202E), which is used for coding languages that are written from right to left, like Arabic or Hebrew.
According to Kaspersky Lab, the malware creators used a hidden RLO Unicode character in the file name that reversed the order of the characters, thus renaming the file itself, and send it to Telegram users.
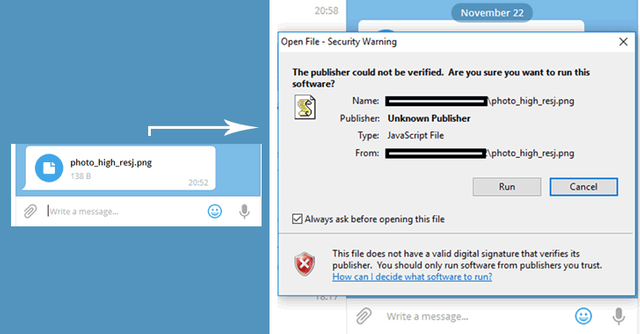
For example, when an attacker sends a file named "photo_high_reU+202Egnp.js" in a message to a Telegram user, the file's name rendered on the users' screen flipping the last part.
Therefore, the Telegram user will see an incoming PNG image file (as shown in the below image) instead of a JavaScript file, misleading into downloading malicious files disguised as the image.
"As a result, users downloaded hidden malware which was then installed on their computers," Kaspersky says in its press release published today.
Kaspersky Lab reported the vulnerability to Telegram and the company has since patched the vulnerability in its products, as the Russian security firm said: "at the time of publication, the zero-day flaw has not since been observed in messenger's products."
The vulnerability can be used to carry out a variety of attacks against an infected machine. One payload attackers distribute in this way can be used to take remote control of the machine.
In this instance, a downloader written in .NET and using the Telegram API as the command protocol is able to launch a modified start registry key on the system, allowing the attackers to gain full control.
This backdoor allows for a number of malicious operations, including launching, downloading and deleting files and extracting web browsing history archives.
In addition to installing a backdoor onto the system, the attackers are also able to tailor the Telegram malware for mining cryptocurrency -- including Monero, ZCash and Fantomcoin. It's unknown how much has been made from the scheme, but it can prove highly lucrative to cybercriminals.
Researchers haven't disclosed when the vulnerability was discovered but said that since disclosing it to Telegram, attacks using the exploit haven't been seen in the wild. ZDNet attempted to contact Telegram, but hadn't received a reply at the time of publication.
One way Telegram users can avoid falling victim to these types of attacks is by not downloading untrusted files from unknown sources - and being wary of trusted contacts suddenly attempting to share files without context.
Woff, woff!
Hello @sam4u3, We have met 2 times already!
I'm a guide dog living in KR community. I can see that you want to contribute to KR community and communicate with other Korean Steemians. I really appreciate it and I'd be more than happy to help.
KR tag is used mainly by Koreans, but we give warm welcome to anyone who wish to use it. I'm here to give you some advice so that your post can be viewed by many more Koreans. I'm a guide dog after all and that's what I do!
Tips:
Unfortunately, Google Translate is terrible at translating English into Korean. You may think you wrote in perfect Korean, but what KR Steemians read is gibberish. Sorry, even Koreans can't understand your post written in Google-Translated Korean.
I sincerely hope that you enjoy Steemit without getting downvotes. Because Steemit is a wonderful place. See? Korean Steemians are kind enough to raise a guide dog(that's me) to help you!
Woff, woff! 🐶
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://thehackernews.com/2018/02/hackers-exploit-telegram-messenger-zero.html
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
kr-guide!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit