
In a new report released by Group-iB, a cybersecurity intelligence agency, it has been revealed that 65 percent of the $882 million in cryptocurrency stolen from exchanges ends up in North Korea.
With sanctions from the United States and Europe continuing to weigh on Pyongyang, North Korea has reportedly turned to cryptocurrencies to generate additional revenue.
According to the report, North Korean hackers have stolen as much as $571 million since January 2017, making up nearly 5 percent of the country’s GDP.
The report notes that many of the attacks are tied directly to neighboring countries Japan and South Korea, including the $534 million hack of Japan’s CoinCheck, which has only recently resumed operations.
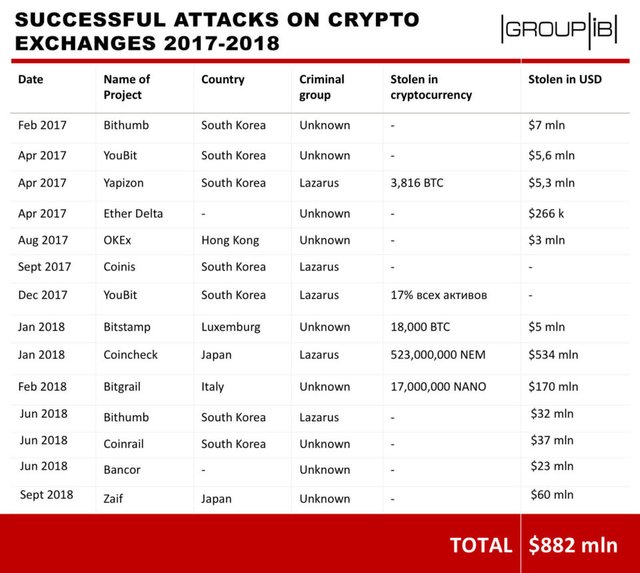
Though just a few of the attacks that have occurred over the past two years have actually been tied to a specific criminal organization, South Korea expects that North Korean hacker groups are likely responsible for many more.
The three branches of the DPRK’s hacking ecosystem
First, and most well-known, is the Lazarus Group, the supposed state-sponsored hacker group responsible for the Sony Motion Pictures hack, and according to some, the WannaCry attack which infected over 200,000 computers across 150 countries.
Lazarus has widely been blamed for many of the attacks associated with the North Korea's cybercrime wave, but FireEye suggests that there may be two other groups which are casually flying under the radar.
FireEye believes that there are two groups that are specifically focused on cyber-espionage, targeting infrastructure, media outlets and the general population – the Lazarus Group and TEMP.Hermit – and one other group which is responsible for financial crime – APT38.
Similar toolsets and even overlaps in coding have linked the three groups to one another, offering a surprising insight into how organized and complicated the North Korean government’s efforts might be. The FireEye report also uncovers how precise and patient the groups are in their attacks.
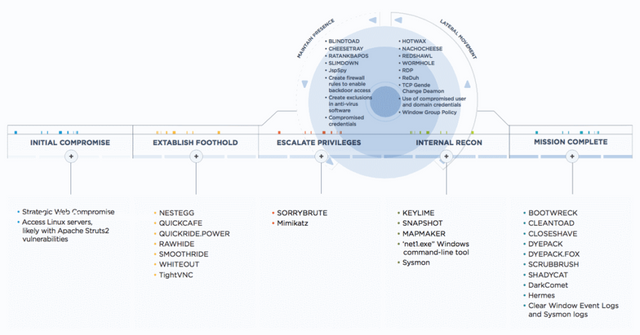
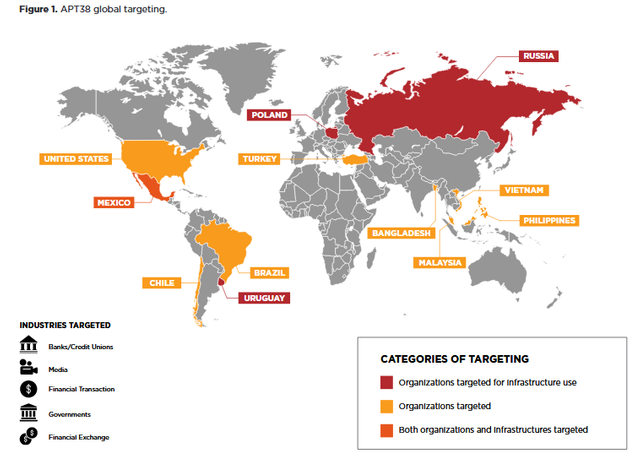
With these tools and techniques, FireEye noted that the first activity from APT38 could be traced all the way back to 2014, the same time that Lazarus first hit the scene. And North Korea's attacks are much further reaching than originally thought, directly targeting infrastructure and organizations in at least 12 countries.
Conclusion
While many of the exact details of the three organizations tied to Pyongyang remain scarce at best, it’s becoming abundantly clear that North Korea possesses a deep understanding of technology.
Last year, FireEye also reported the country had started mining cryptocurrencies around the same time sanctions on coal trade were enacted, suggesting that the regime could be using their most abundant natural resource to generate revenue despite the economic measures weighed against it.
Additionally, South Korean media outlet, Yonhap News, notes that there has been a significant uptick in cryptojacking activity, most likely tied to North Korea's hackers.
While the DPRK has fallen out of favor with many international news outlets in recent months, it’s clear the country is still very active behind the scenes.
Originally posted on Crypto Insider : https://cryptoinsider.com/north-koreas-hacks-iceberg/