Disclaimer: I am not a seasoned veteran in Cybersecurity, I am simply someone who loves the field and wants to push their skills as far as possible within their favoured topics. Ultimately, netting a position in the industry along the way. However, what I say is based on my own experience and practice.
Introduction
Hi and welcome to my first “proper” Steemit post. I will be discussing and outlining a few different fields in Cybersecurity, a brief explanation and some relative books and/or resources to follow up with.
Note: This post is aimed at beginners/newcomers who are wanting to learn more about what happens within the mysterious world of Cyber. Content I post will be toned down and (hopefully) be generalized enough for everyone to follow. For this reason, I will not include any code snippets in this post but will be using them in future content.
Cybersecurity has been a focused topic for a while now, but recently there has been a huge increase in presence. Ranging from tutorials to researchers, and from small code write ups through to fully hosted playgrounds. In this post, I will be discussing the following few topics that I have dabbled with
- Software Exploitation
- Reverse Engineering
- Penetration Testing
Feel free to skip any section you aren’t interested in, or already have an understanding of the topic.
Software Exploitation
Software Exploitation is a huge topic that spans across Cybersecurity, so I will attempt to summarize the main fields I have personally come across into short chunks.
New software is being developed, released and hacked every day. Developers all around the world are working on exciting, new ideas to help their everyday users increase their work productivity, social life or even just pass time. The downside to this, is everyone is potentially at risk if the software they are using contains vulnerabilities, that an attacker could exploit.
One of the most common vulnerabilities that can be exploited in software is the Buffer Overflow. This is where a chunk of memory (known as a buffer) has been assigned by a developer to hold some specific information for current or later us in the program. This could be something like a name field. When the user types their name into the field and “submits” the data, the program executes various functionality to push it on to the memory model (stack or heap), as shown in the following diagram.
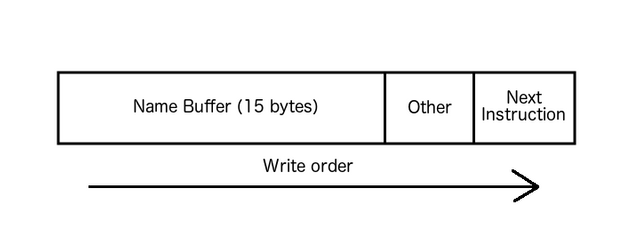
Let’s imagine a developer has assigned a set size of the buffer to be 15 characters (bytes) in size. What would happen if the user’s name breached this limitation? Some functions utilised will actually continue to write the extra data to the adjacent memory addresses after the buffers allocated space. This is what is known as a buffer overflow.
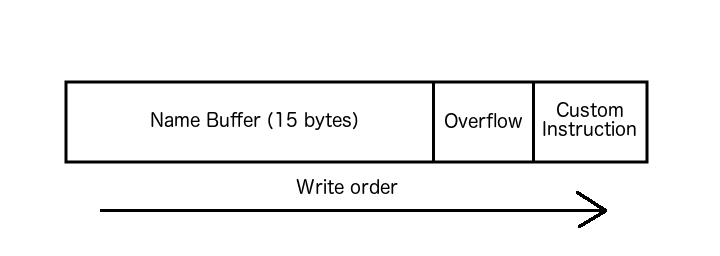
You may be wondering why this is useful when exploiting software. Within memory are specific addresses that hold data for specific registers and instructions for the computer to continue execution. If these values can be overwritten without breaking the program, the next instruction can be customised and allow an attacker to execute arbitrary code, visualised in the following image.
Further reading on Software Exploitation?
- “Hacking: The Art of Exploitation” by Jon Erickson as this covers various exploitation topics with code samples and methods of exploiting them.
- “A Bug Hunter’s Diary. A Guided Tour Through the Wilds of Software Security” by Tobias Klein. It consists of real world vulnerabilities that have been found in released software and detailed explanations of how they were exploited.
Reverse Engineering
This is a topic that I am fairly new too, but I find it fascinating. Reverse Engineering is the process of studying compiled code and essentially working backwards until it is as understandable as the original code source in which each piece can be studied. Imagine purchasing a car – and wanting to understand how each piece worked and the components they were made of. You could take it all apart until an overall understanding of each area can be had. However, instead of physical components, a reverse engineer will study assembly instructions (x86 or ARM, depending on the environment) and separate the program into different sections.
Reverse Engineering can be utilised in various different fields, including Malware Analysis, Software Exploitation and Penetration Testing. In Malware Analysis, you study and attempt to figure out how malicious programs effect the target system and what they do when they have a foothold. A very common type of malware these days is Ransomware, I’m sure you have seen them in the news. It essentially encrypts all of your files and demands a payment is made before you can access your files again. Analysts can attempt to reverse engineer the software to see how they encrypt the files, whether there is any indication of who the developer is or even a way to decrypt the data for free [link a free decrypter found (twitter this morning)]. Reverse engineering can be utilised in software exploitation when the source code isn’t accessible. The assembly instructions can be studied to try and pinpoint potential vulnerabilities and how to utilise them, for the sake of keeping this brief I will further touch on Assembly in a future post. Penetration Tests can be based on, or around, custom apps and software. A reverse engineer could find vulnerabilities to penetrate the network or elevate privileges within the target environment.
Further Reading on Reverse Engineering?
- "Reverse Engineering for Beginners" - Brilliant read and can be read online for free at https://beginners.re/
- @fox0x01 has some incredible reads for ARM based reverse engineering at http://azeria-labs.com
Penetration Testing
Penetration Testing, commonly referred to as pen-test(ing) compiles various skill sets and fields into one toolbox. A pen-test can be performed on a company to test both their network security and their physical security. A tester, or a team of testers, are given legal permission and a scope to attempt to break into a company utilising various methods of their choice. This can range from utilising open source intelligence, social engineering on staff members, software exploitation and more. All results are recorded and presented to the client to help them understand their security weaknesses as well as proposed methods to help secure their assets in the future.
Lots of pen-testing tools and resources can be used within the Kali Linux operating system. This is a free operating system developed and maintained by Offensive Security [link], pre-loaded with many tools and resources to hack into systems.
I have spoken to a lot of Cybersecurity newbies (including myself) who have stated that their target goals included pen-testing for companies, either as a solo contractor or as part of team. The field is very popular and a lot of fun.
Further Reading on Penetration Testing?
- “Penetration Testing, A Hands on Introduction to Hacking” by Georgia Wiedmann. Extremely popular book, easy to understand and helps you set up a private pen-testing environment at home.
Outro
Although brief, I hope each section has helped simply clarify each of the 3 outlined sections. I plan to post further information about work I have done in each field, with some detailed write ups/tutorials on tools and challenges I have completed. I hope you enjoyed the read, and hopefully learnt a little something yourselves.
If there are further questions or comments about changes that need to be made, then please let me know, posting content online is a learning curve for me and I would appreciate any help.
Feel free to follow me on here or Twitter @Monobehaviour for more!
Congratulations @justblink! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPDownvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit