You probably seen or heard or shared this news from TV, Radio and Social Media that Russian civilian and military intelligence services (RIS) successfully interfere with 2016 US Presidential election and hacked the email addresses of high profile target in Politics to name a few.
Department of Homeland Security Assistant Secretary for Public Affairs Todd Breasseale issued an executive summary today of the U.S. government’s findings of Russian malicious cyber activity known as Grizzly Steppe.
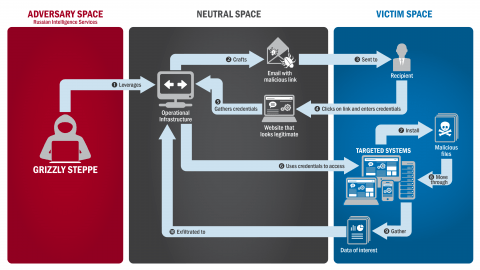
Russia’s civilian and military intelligence services engaged in aggressive and sophisticated cyber-enabled operations targeting the U.S. government and its citizens. The U.S. Government refers to this activity as GRIZZLY STEPPE. These cyber operations included spearphishing campaigns targeting government organizations, critical infrastructure entities, think tanks, universities, political organizations, and corporations, and theft of information from these organizations. This stolen information was later publicly released by third parties.
What Is Spearphishing?
Spearphishing is the use of forged emails, texts, and other messages to manipulate users into opening malware or malicious software or clicking on malicious links.
Spearphishing attacks can lead to credential theft (e.g., passwords) or may act as an entry point for threat actors into an organization to steal or manipulate data and disrupt operations.
For more information, see the US CERT Tip on Avoiding Social Engineering and Phishing Attacks.
Continue reading the executive summary at their website: https://www.dhs.gov/news/2016/12/30/executive-summary-grizzly-steppe-findings-homeland-security-assistant-secretary
Reported Russian Military and Civilian Intelligence Services (RIS). Alternate Names
APT28
APT29
Agent.btz
BlackEnergy V3
BlackEnergy2 APT
CakeDuke
Carberp
CHOPSTICK
CloudDuke
CORESHELL
CosmicDuke
COZYBEAR
COZYCAR
COZYDUKE
CrouchingYeti
DIONIS
Dragonfly
Energetic Bear
EVILTOSS
Fancy Bear
GeminiDuke
GREY CLOUD
HammerDuke
HAMMERTOSS
Havex
MiniDionis
MiniDuke
OLDBAIT
OnionDuke
Operation Pawn Storm
PinchDuke
Powershell backdoor
Quedagh
Sandworm
SEADADDY
Seaduke
SEDKIT
SEDNIT
Skipper
Sofacy
SOURFACE
SYNful Knock
Tiny Baron
Tsar Team
twain_64.dll (64-bit X-Agent implant)
VmUpgradeHelper.exe (X-Tunnel implant)
Waterbug
X-Agent
Commit to Cybersecurity Best Practices
A commitment to good cybersecurity and best practices is critical to protecting networks and systems. Here are some questions you may want to ask your organization to help prevent and mitigate against attacks.
- Backups: Do we backup all critical information? Are the backups stored offline? Have we tested our ability to revert to backups during an incident?
- Risk Analysis: Have we conducted a cybersecurity risk analysis of the organization?
- Staff Training: Have we trained staff on cybersecurity best practices?
- Vulnerability Scanning & Patching: Have we implemented regular scans of our network and systems and appropriate patching of known system vulnerabilities?
- Application Whitelisting: Do we allow only approved programs to run on our networks?
- Incident Response: Do we have an incident response plan and have we practiced it?
- Business Continuity: Are we able to sustain business operations without access to certain systems? For how long? Have we tested this?
- Penetration Testing: Have we attempted to hack into our own systems to test the security of our systems and our ability to defend against attacks?
- Patch applications and operating systems – Vulnerable applications and operating systems are the targets of most attacks. Ensuring these are patched with the latest updates greatly reduces the number of exploitable entry points available to an attacker. Use best practices when updating software and patches by only downloading updates from authenticated vendor sites.
- Application whitelisting – Whitelisting is one of the best security strategies because it allows only specified programs to run while blocking all others, including malicious software.
- Restrict administrative privileges – Threat actors are increasingly focused on gaining control of legitimate credentials, especially those associated with highly privileged accounts. Reduce privileges to only those needed for a user’s duties. Separate administrators into privilege tiers with limited access to other tiers.
- Network Segmentation and Segregation into Security Zones – Segment networks into logical enclaves and restrict host-to-host communications paths. This helps protect sensitive information and critical services and limits damage from network perimeter breaches.
- Input validation – Input validation is a method of sanitizing untrusted user input provided by users of a web application, and may prevent many types of web application security flaws, such as SQLi, XSS, and command injection.
- File Reputation – Tune Anti-Virus file reputation systems to the most aggressive setting possible; some products can limit execution to only the highest reputation files, stopping a wide range of untrustworthy code from gaining control.
- Understanding firewalls – When anyone or anything can access your network at any time, your network is more susceptible to being attacked. Firewalls can be configured to block data from certain locations (IP whitelisting) or applications while allowing relevant and necessary data through.
I first posted this article at https://que.com/grizzly-steppe-russian-malicious-cyber-activity/
Cheers,
@Yehey
https://QUE.com - Follow Me to Follow You :)
Hi ! Great article, following you :)
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Rubbish.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit