Welcome to the Deep Web, where most of the internet's web pages have their servers set up and you have a couple of underground marketplaces full of vendors from all around the world. You can find listings for anything from topshelf marijuana to an eightball of coke, to even guns and hackers for hire. The main concern for most people, even if just visiting, is to remain as secure as possible. They're well aware that entering a world full of drug dealers, scammers and assassins might be a dangerous one. So how do you do it?
Well if you've done at least one google search on this topic before, or have seen some piece in the news, you've definitely stumbled upon TOR. "The Onion Router" browser is basically a modified version of Firefox that was created by a government contractor a long time ago, it helps you visit .onion sites which are like encrypted versions of .com sites (to simplify explanations). To access .onions, you need specific browsers because just typing in the urls into Torch or Chrome won't really do the trick. TOR is nice and all, as it masks your IP and makes it seem like you're in a different country while also giving you access to these hidden sites, but do remember that its background is a little murky.
Just using TOR may be suspicious or illegal in some areas (although it's perfectly fine in the US, however if your ISP sees you using it they might note that down), so that's where VPNs and VM's come into play. If you'd like to visit let's say, Hansa for example, you'd have to probably install TAILS which comes with TOR inside of it. The NSA can easily discover where your redirects are coming from if you have nothing but TOR open, as well as other hackers or malicious software.
TAILS is nice since you're able to put it on an encrypted flashdrive (if you're wondering how to do this, check out the first link down below to another one of my Steemit posts) and basically plug it out and smash it if you ever get raided. Also, for anybody interested TAILS 3.0 just came out so definitely don't forget to update!
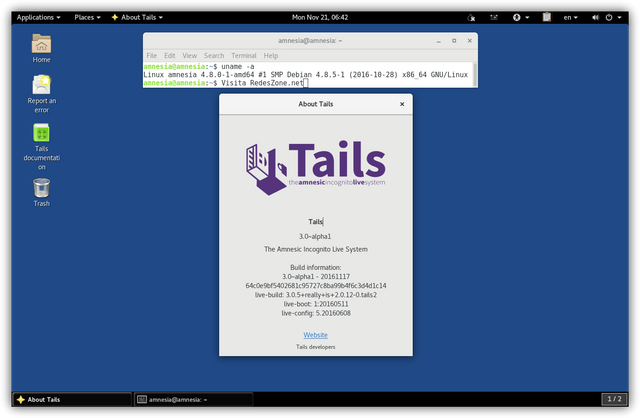
TAILS will be easier to work with now, as it's got a slightly updated interface. If you're a complete newbie, going with the more technical options like Whonix or Qubes might actually make OPSEC worse for you. Just because they're more secure doesn't mean they're the better option. If you don't fully understand what you're working with, you could leave some parts of the systems open to attacks and you'd just be better off going with TAILS. If you're vending for example, getting TAILS on a VM and then running that either on Debian Linux or distros would be dope too.
But the best option by far it seems like would be going with Qubes and then mixing Whonix with it. The problem?
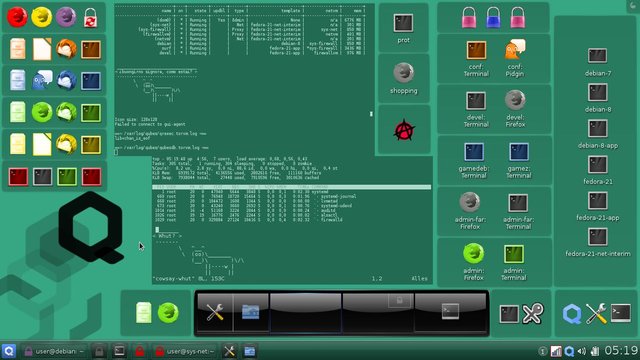
This may look a little complex for the average non-techie person..
What's cool about Qubes is the fact that you're able to run multiple "domains" and files and data aren't transferred between the domains unless you allow it to happen. This means that if you shut down a domain/vm with malware on it, the hackers could never get to your other more important tabs. So if you keep passwords in one, emails on another, bank login details or crypto wallets on a third and so forth, it'd be incredibly difficult to penetrate all those layers.
Then you combine Whonix on top of all that and you're all good to go.
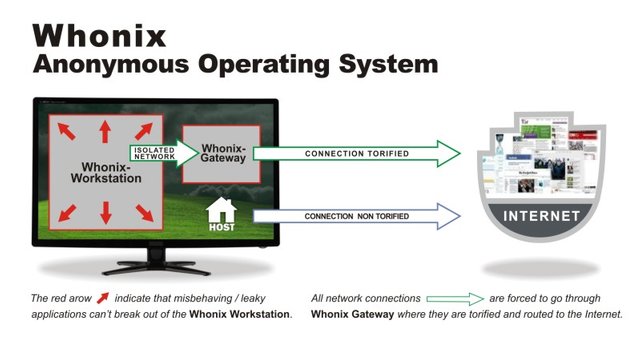
So after all that stuff, what about the internet connections? It's best to go with 2 VPNs, one on the host system and then one through TOR. VPN's don't really work too well with TAILS unless you force it with a VPN router or through bridges, but that could get a little tricky. On top of all that, if you were extremely paranoid you could hack into your neighbor's wifi with an adapter and change it up every few days. But even once on that step, I'd definitely look into TOR Bridges and SOCKS5 proxies.
Now Whonix/Qubes and VPNs are only the beginning of your OPSEC. If you really wanted to go full out, you need to think about physical stuff too. You'd have to be moving around a lot, have a fake identity with forged documents, living in a third world country and using mules :)
If you're curious about the darknet and its markets, check out my latest guide but please realize that it is outdated (as in old version of TAILS and without whonix/qubes)
Anyways, more to come! Thanks for reading chaps
LINKS
https://steemit.com/security/@avilsd/how-to-encrypt-your-usb-for-the-deep-web
https://www.torproject.org/projects/torbrowser.html.en
https://www.whonix.org/
https://www.qubes-os.org/
https://tails.boum.org/upgrade/tails/index.en.html
https://openvpn.net/
https://www.reddit.com/r/DarkNetMarkets/
https://www.reddit.com/r/DarkNetMarketsNoobs/wiki/bible/buyer
https://www.youtube.com/c/AVILSD
