Nowadays, the Internet is part of our lives and we are using it for almost everything, and many of us would be impossible to imagine life without it.
It was a real IT revolution and the world has changed completely and irreversibly. Internet companies had become real giants with incredible possibilities.
Options for new businesses emerged.
As the volume of trading and banking services grew on the internet, the number of those who wanted to abuse the entire system has also grown.
It has become clear that the need for security and safety is priceless and inevitable.
Many improvements have introduced to improve data traffic protocols or transmission control protocol TCP and IP ("IP has the task of delivering packets from the source host to the destination host solely based on the IP addresses"), often referred to as TCP/IP.
Internet Protocol Version 4 (IPv4) is dominant protocol and succeeded by (IPv6).
However, the level of possible attacks and abuse in the whole design couldn't be anticipated, so we have witnessed a variety of theft of data and money, espionage etc.
Solid progress has been made by VPN(virtual private network).
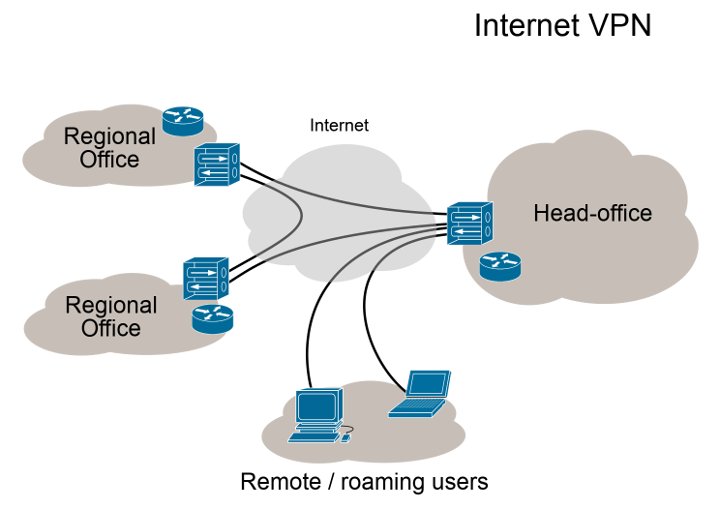
VPN is a group of computers networked over a public network or the Internet. What does that mean? This means that you no longer need to have computers physically in one place, but at any location in the world, but that you can have all the privileges of the local network. This concept is often used in the private sector, which is relevant to various companies because it allows users to connect VPN to the business network from home and to access the company's computer resources. The most common way is to access the company's servers where confidential data is used in the business. However, VPN has one more function, which is to protect your connection from other participants on the Internet. That is, protect your data from a third party. This "third person" can be an ISP or some other company that wants to see your Internet traffic. When you connect a VPN to a specific server, from your computer to that server, after authentication, a secure tunnel through which your data travels, is created. This tunnel is naturally encrypted, and if someone comes into possession of data traveling through the tunnel, it will not be able to see what kind of data it is because there is no key with which these data are encrypted and can not decrypt them. They can try to decrypt it with brute force technique, but they will probably not even get to the data that they find in those Internet packages he has intercepted.
In fact, such traffic is difficult to intercept, especially when using special VPN protocols. There are 4 protocols that most popular VPN service providers support.
These are PPTP, L2TP/IPsec, OpenVPN and Chameleon protocols. The simplest protocol is the Point-to-Point Tunneling Protocol, which is also one of the oldest protocols, and it was made by a consortium behind Microsoft.
This is a protocol that uses 128-bit encryption and has become an integral part of all operating systems.
Another protocol worth the attention is L2TP/IPsec. It's actually dual technology since L2TP (Layer 2 Tunnel Protocol) is just a VPN protocol that does not have a mechanism for encrypting data and is combined with an IPsec that serves as a mechanism for encryption.
Combined, you get an extremely strong VPN protocol with 256-bit protection, which is slightly slower than PPTP, but also much safer.
You are now wondering if there is a good protocol that is not compromised? Yes, and it is the OpenVPN protocol or better said technology. OpenVPN is open source technology that relies on the OpenSSL library and the SSLv3 / TLSv1 protocol and is considered the best and most reliable technology when talking about VPN.
There is no free good VPN. First of all, free VPNs will fill you with advertisements, give you a slow link, you will barely open a website, and will most likely record your activity on the Internet.
VPN provider knows your real IP address!
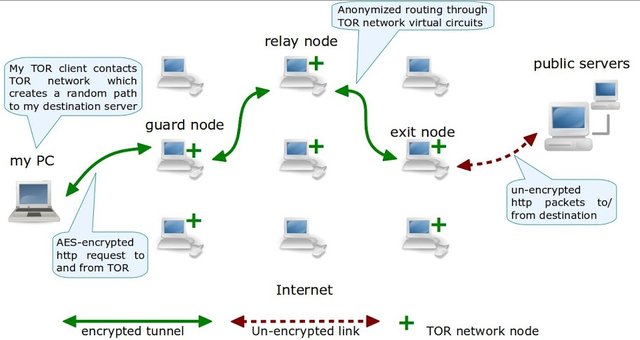
Let's talk about TOR!
Tor is free and open source project for enabling anonymous communication. TOR is an acronym of "The Onion Router".
Tor is routing Internet traffic through a free, worldwide, volunteer network of many thousand relays to hide the user's location.
Tor is designed to protect the user's private data, as well as their freedoms and opportunities to conduct confidential communications while keeping their Internet activity beyond the ability to be monitored.
Tor encrypts the original data, including the IP address, repeatedly and sends it through a virtual circuit that includes consecutive, randomly selected Tor stages.
Each stage decrypts the layer of encryption to uncover only the next stage in a circle in a row. And so the rest of the encrypted data.
The final stage decrypts the deepest layer of encryption and sends the original data to the destination without detecting, or even knowing, the source of the IP address.
Because communication routing is partially concealed at every step in Tor Circle, this method eliminates every single point where communication can be detected or deanonymized through the surveillance.
The NSA (National Security Agency) featured Tor as "the King of High Security, Low Latency in Internet Anonymity" and there are no competitors to TOR.
The attacks against Tor are an object of active academic research.
In June 2013, Edward Snowden used Tor to send information to the Washington Post, and the Guardian.
Those who support Tor say they support freedom of expression, including countries where the Internet is censored, protecting the privacy and anonymity of users.
Critics say that Tor is not as secure as it is supposed to be. In October 2013, after leaking documents revealed by Edward Snowden, Guardian reported that the NSA was trying to crack Tor and failed in that intention, even though they had success in individual attacks on Tor users.
The Tor project claims that Tor is used by normal people who want to hide their Internet activity from sites that follow them, as well as advertisers, Internet espionage etc.
With the emergence of the cryptocurrencies and the crypto market, the need for online anonymity has dramatically increased.
Many new crypto projects claim that anonymity is guaranteed at highest level. Monero, Zcash, PIVX, Komodo, NAV Coin, ZenCash, Verge and many of them claim they are using the TOR protocol, but by inspecting the documentation you cannot be sure that the TOR is incorporated into the deepest layers of those projects.
Seeking a true genuine cryptocurrency with all the attributes of the TOR protocol and bringing together new technologies incorporated into new hybrid applications, you can't take away the impression that probably, so far, no project is closer to that ideal than DeepOnion.
It's very important to notice multi-layered security model. I strongly recommend you to explore the DeepOnion White Paper for a more comprehensive insight into the entire project.

Disclaimer: I do not provide personal investment advice and I am not a qualified licensed investment advisor.
Conduct your own due diligence, or consult a licensed financial advisor or broker before making any and all investment decisions.
Great Article!!!The networks are fascinating.
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit
Congratulations @mikebgd2018! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPDownvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit