There are a lot of reasons why you'd need to remain unknown on the web. Perhaps you need to maintain a strategic distance from those frightening focused on promotions for things you Googled before in the week. Or on the other hand maybe you simply don't need your beforehand went to sites turning up in your accomplice's perusing session. Whatever the reason, protection online is turning into a major ordeal as it turns out to be clear how little of it we truly have, because of omnipresent site trackers that gather information on our developments.
From turning on your program's undercover mode, to downloading a module to eradicate your tracks, here are a few hints on surfing the web without leaving (a lot of) a trail.
Use a private browser window
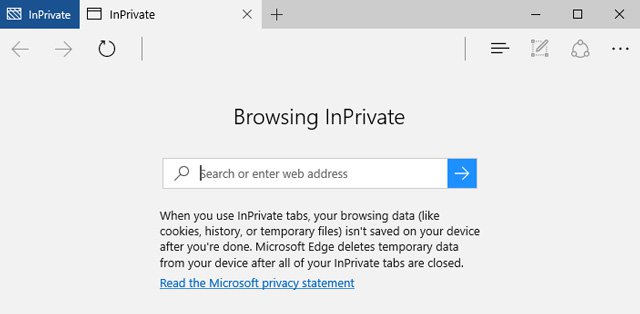
On the off chance that you share a PC – or are at an open PC – turning on private mode keeps your perusing history from being put away on the PC, hence keeping the locales you went by from flying up later, say, in an auto-finished web address.
Outsider treats – little content records that track your development between different locales – are likewise blocked, and first-party treats (which track your development inside a site so as to monitor, say, your shopping bin or inclinations) are erased toward the finish of the session, with the goal that whenever somebody visits that site, it won't be evident that you'd been there as well.
What to do: Head into the toolbar of your program and select a private or undercover mode.
Slaughter all treats
Blocking or erasing outsider treats (do it by heading into your program's Privacy settings) stops a few sorts of following, yet not all. Streak treats, or purported super treats, can store more data and are left by destinations that run Flash, which is any site with video content. These super treats can track your developments crosswise over various programs and even recover outsider treats you beforehand erased.
What to do: Download the free CCleaner to clear both Flash and normal treats, yet be cautioned – a few destinations utilize outsider treats to track you inside the webpage, so you may end up signing in over and again.
Stop your program sending area information
About all programs have an element that sends your geological area to locales you visit, in principle to furnish you with more important, helpful encounters – for instance, so a flight correlation site naturally knows where you're reserving from, or so Google can come back with adjacent query items. In any case, sponsors or locales can utilize that exceptionally same data to add to that promotion profile of you.
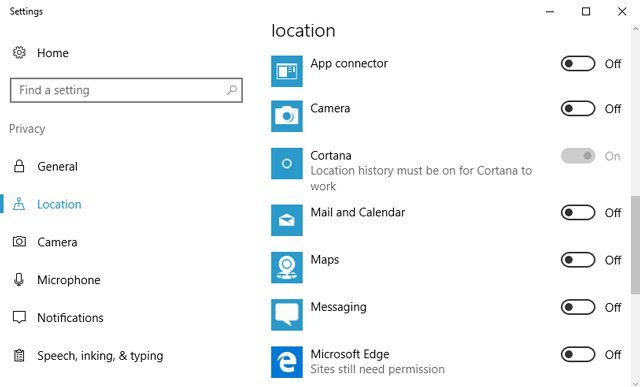
What to do: Deny area demands from sites where it isn't fundamental. While the default choice is dependably select in, i.e., your program will ask you the first run through a site needs your area, you can likewise handicap the component altogether:
Chrome – Preferences > Settings > Advanced > Content settings, and decide to either deny any site to track your physical area, or ask when a site needs to track.
Safari – Preferences > Privacy, where you can debilitate area administrations, or let every site make a demand.
Firefox – Type "about:config" in the URL bar, at that point "geo.enabled". Double tap to handicap area altogether. Something else, Firefox dependably asks before sending your area to a site.
Microsoft Edge – You don't set this utilizing the Edge program. You'll have to kill area following utilizing your PC's fundamental Settings > Privacy and afterward look down to Choose applications that can utilize your exact area and flip Microsoft Edge to Off
Inquiry secretly
Google represents over 75% of worldwide hunt activity, with billions of pursuit questions prepared a day. It utilizes this information to convey always customized list items, which are very applicable for the majority of us, however it additionally makes a rise of you-driven hunt that could keep you from seeing certain site pages in light of what you've tapped on before.
What to do: You can kill Google's customized look by hitting Search Tools > All Results > Verbatim. To keep your inquiries being followed – and influencing the advertisements you're demonstrated – change to a private internet searcher, for example, DuckDuckGo.
Stop Google following you
Much obliged its fluctuated blend of administrations – Gmail, Calendar, Google+, YouTube, Search – Google is in an interesting position to fabricate a profile of your identity, what you like and what you do on the web. Its bound together security strategy implies that it can track you over every one of its administrations – including filtering your email - and utilize the data cross-item to customize your experience. The geniuses are helpful things like getting area particular schedule updates, however the cons incorporate focused on advertisements in light of your email content or your photo transforming up on things you've enjoyed while signed into Google+.
What to do: Opt out of "shared support" in promotions and kill advertisement personalization (despite everything you'll be indicated advertisements, however they won't be focused on). At last, download the Google Analytics Browser Add-on to stop Google Analytics utilizing information on your developments to make profiles for its promotion accomplices
Stop social locales making sense of you
Its a dependable fact that interpersonal organization destinations have amassed a colossal measure of data on us in view of what we do inside their locales – things we like, individuals we tap on most and what we look for. However, locales like Facebook, Twitter and LinkedIn track clients even after they've logged out of their records. One way is the point at which you tap via web-based networking media sharing catches, for example, a Facebook Like catch, or a Twitter share catch. However, regardless of whether you don't share content, the very demonstration of going by a site page that contains such catches sends the data back to the mothership, enabling publicists to keep demonstrating a similar promotion to somebody who has gone by their website page and left (maybe on the grounds that they perused yet didn't purchase).
Facebook, which works its own versatile promotion arrange, utilizes a contrasting option to a tracker called a change pixel that publicists use to track what number of snaps or deals they get. The data backpedals to Facebook, paying little mind to whether the publicist's site had a Facebook catch on it.
What to do: Head to Facebook's Settings/Adverts to control whether promotions are focused on in view of your snaps all through Facebook; for Twitter, Settings/Security and Privacy, at that point uncheck the case for "Tailor ads..."; for LinkedIn, Privacy and Settings/Account/Manage Advertising Preferences.
(You can look at our goliath manual for Facebook security settings as well.)
In every one of these cases, you won't get advertisements in view of your perusing, however regardless you'll be followed, apparently for security reasons. (Be that as it may, a few locales, including Twitter, respect the Do Not Track setting found in your program's protection settings, which implies they won't log your quality at their site.)
Quit following
Each webpage on the web is inserted with following treats in the different bits of substance they contain – for instance, advertisements, remark boxes, supported connections. These treats are set by various promotion systems contained horde publicists who get information on what locales you tap on inside specific advertisement systems. This information is then used to make a profile that is shared among the individuals from a promotion organize so they can target publicizing in view of your apparent inclinations and propensities.
What to do: Head into your program's security settings and turn on Do Not Track. To limit information accumulation on your web developments further, you can likewise quit following at Network Advertising Initiative and Digital Advertising Alliance, by any promoters who are a piece of these associations. You can likewise quit straightforwardly at significant promotion systems including BlueKai, Acxiom and Chitika. Despite everything you'll see promotions - however they won't be focused on.
Square all trackers
Quitting can stop you being followed by numerous locales, yet numerous more may not respect such demands. Against tracker program modules can keep these treats from "tailing" you around the web.
What to do: Download a hostile to tracker module, for example, the Electronic Frontier Foundation's Privacy Badger, Ghostery, or Disconnect, which squares following treats to keep advertisement investigation organizations from building a fabulous profile of exactly where you jump at the chance to go on the web.
Debilitate Java and unused modules
Modules are downloadable, little projects that improve your program's abilities, for instance, playing certain video or activitys. (These are not to be mistaken for program Extensions, which are basically site pages that heap data inside another site page.) Unfortunately, two of the most usually required modules, Adobe Flash and Java, are additionally to fault for uncovering recognizing insights about your program.
Specifically, Java is outstanding to "unique finger impression" a program by showing to locales an overabundance of recognizing points of interest, for example, IP address, textual styles downloaded and that's only the tip of the iceberg.
What to do: Since modules are additionally a typical route for malware to discover its way into a program, it's not a terrible plan to handicap them, especially lesser-utilized ones. Also, where once by far most of destinations required Java to run their different movements or intelligent pieces, nowadays an ever increasing number of locales are assembled utilizing code that can be locally keep running by programs.
Chrome: Enter "chrome://modules/" into your inquiry bar. To impair you need to incapacitate them briefly, simply click "Handicap."
Firefox: Type "about: addons" into the pursuit bar, at that point select Plugins. You can actuate the modules dependably, never, or simply subsequent to asking authorization.
Safari: Head to Preferences > Security > Plug-in Settings to kill each on or.
Microsoft Edge: Rejoice, for you have no modules accessible to you.
On the off chance that you get messages on specific destinations that you have to run these modules, you might need to put resources into a content blocker expansion, for example, NoScript (Firefox) or ScriptNo (Chrome). These stop all Flash and Java as a matter of course, with choices to construct a whitelist of trusted locales that need these modules.
Utilize an intermediary organize
The greater part of the above alternatives are awesome for avoiding following treats that can give advertisers what they have to make extraordinarily point by point profiles of your identity. Yet, you can at present be followed and distinguished by means of the IP address of your program. IP locations can recognize your estimated area, and how frequently you visit specific destinations.
To recover somewhat more namelessness, a virtual private system (VPN) veils your IP address and reassigns you another one, so you seem, by all accounts, to be surfing from a different area. Each time you sign into the VPN, you get another IP address, anticipating individuals, (for example, your manager, say) from observing what sites you visit.
In nations where certain locales are prohibited, for example, China, numerous individuals influence utilization of VPNs to surf to by means of IP delivers that give off an impression of being from another nation, keeping in mind the end goal to get to online networking including Facebook. Here in the U.S., it's significant that an as of late passed change gives the FBI forces to hack any PC utilizing a VPN.
What to do: Not all VPN administrations are made equivalent. Some complete a far superior activity of securing your protection than others [it was as of late found that PureVPN helped the FBI in finding a cyberstalker utilizing client get to logs, despite the fact that they guaranteed not to have "any logs" of client activity], offer quicker speeds and better convenience. In light of our own testing, and outsider examination, for example, PC Mag, we prescribe NordVPN (Disclosure: we have an offshoot association with NordVPN). Remember that administrations like Netflix may not give you a chance to interface in case you're utilizing a VPN benefit. Look at our tips on the most proficient method to utilize a VPN and still access Netflix. Utilizing a VPN is additionally a decent method to ensure your information on open WiFi systems.
Download a private, unknown program
Modules, intermediaries and making sure to turn on private perusing can make for an unwieldy web involvement. In case you're willing to surrender the solace of your most loved program, you can download a radical new program that offers the greater part of the above highlights – including the capacity to turn on an intermediary arrange through a switch in the toolbar.
The Epic program depends on the Chrome program however with security settings dialed up so outsider treats are naturally blocked, inquiry and perusing history is never logged, and trackers are constantly blocked. Regardless you'll see advertisements, however you won't be followed – and the landing page shows an intriguing counter indicating what number of trackers endeavored to log your developments today.
What to do: Get Epic Privacy Browser. Protection doesn't really come to the detriment of accommodation – you can empower auto-fill to finish web frames with beforehand entered information (accepting it isn't an issue that another person with access to your PC sees this), and however passwords can't be spared inside your records' sign-in shapes, you can download a secret key expansion that takes every necessary step for you.
Run dim with TOR
For the most profound level of secrecy, look at the TOR program, which circulates your web movement through a system of TOR servers (hubs) with the goal that a site you went by can see just the IP address of the leaving hub. Utilizing TOR makes it exceptionally troublesome for anybody to track you, however it does back off perusing. For additional obscurity, TOR can be utilized as a part of blend with VPN. TOR can be utilized for any sort of perusing that requires protection and security, incorporating visits to locales in the Deep Web not available by customary programs. While these locales to a great extent tend towards unlawful action and items, places of refuge for shriek blowers and political nonconformists additionally exist – and TOR is one of the main ways they can be gotten to.
Utilize computerized cash
Acquiring things online is an extraordinary method to attach your character to specific profiles and sites – all things considered, you're utilizing your Mastercard points of interest. On the off chance that you don't need certain buys related with a profile – for instance, perhaps you need to make a private gift to a disputable site, for example, Wikileaks - you ought to consider utilizing a computerized money, for example, Bitcoin, which, similar to money, isn't fixing to any recognizing insights about you.
Notwithstanding, on the grounds that bitcoin exchanges are open, a decided sleuth could track particular adds up to in the long run fabricate a profile about who's spending it – and attach it back to a person. A developing harvest of obscurity centered computerized monetary forms are rising, for example, are rising, for example, Zcash, which has gotten over $700,000 from financial specialists.. Nonetheless, it's not as broadly acknowledged as Bitcoin (which itself isn't precisely the following Mastercard).
By the day's end, remaining unknown online requires outrageous exertion – tech mammoths and specialist organizations go to incredible torments to make It extremely advantageous and simple for us to show our developments and profiles in return for a free administration. While there are advantages to being followed, maybe the key issue today is for individuals to understand that not exclusively are free administrations to the detriment of our security, however that our data is significant – and we should scrutinize each organization that solicitations it, undetectably or not.