Diro's decentralised identities & access is a horizontal technology having applications in many industries like IAM, Blockchain, Context (AR/VR, Dapps), Cyber Security, RegTech, FinTech, AI etc.
DIRO’S Features
- Perfectly organized & updated contacts.
- Missing contacts appear automatically.
- Existing contacts get automatically fixed.
- Archive Contacts.
- Smart Dialer.
- Automatically manage what others see about you.
Today’s digital world lacks a credible identity system that is universally consumable and can be trusted by counter parties across industries. Further, all crowd sourcing based solutions lack credibility and verification that is needed to address regulatory requirements. Getting, all the industries, governments and consumers across hundreds of jurisdictions to agree on a framework is a challenge. A great deal has already been written on challenges in creating universal identity (Vinay Gupta, 2017). The problem has been part technical and part political.
Technical Challenge
Owning Identity is hard : An average consumer is not technologically inclined. Besides having technological and cryptographic challenges, owning identity without proper safety and recovery is dangerous. Permanent loss of control or hacking can lead to severe consequences. Owning an identity today is a technological challenge for an individual as it requires:
Associating public keys with Identity – a public ledger is needed for identity lookups and making sure each identity is uniquely represented by a person. The ledger would typically contain the public key and would be located on a public blockchain.
Modify and control identity attributes – a privately owned profile or profiles containing a list of attributes and values that can be added, modified or revoked.
Regaining lost control of Identity – owners need to have unrestricted access and right to regain control or reset keys in case of a compromise without the need for centralized authority.
Selective sharing of attributes - a way to share signed copies of identity attributes with third parties. The third parties should be notified when such attributes become invalid or expire.
Collect third party claims and authorizations – a method to collect & further share third party certificates containing claims or authorizations.
Verifying identity requires mass consensus : Digital identities have had two broad concerns.
Synthetic Identities – wherein the actual person does not exist and the identity is digitally constructed.
Identity theft – where the attacker is masquerading as someone else. The digital identity is hijacked. This person may or may not be known to the real owner.
Centralized systems are unreliable in long term : Global identity trust fabric needs to be a decentralized system that cannot be attacked from inside or outside. A central store for identity data exposes it to mass breaches and denial of service attacks. Any exposure to such a system would render every service in the world vulnerable. identity systems also control authentication and authorization of third party services including financial transactions and therefore attract the most hacking attempts.
Limitations of mass adoption : Existing networks and databases are limited by their reach in verifying identities to their existing users. The identity trust fabric needs to function with fraction of people signing up and avoid the classic chicken and egg bottleneck.
Cyber-security can no longer be a walled garden
- Tens of specialized cloud services being consumed as technology stacks
- Multi devices including smartphones are now a norm
- Remote working and work from home is more common
- Bring your own device
- Authorization information embedded along with digital assets
- Cloud collaboration is replacing Virtual networks
DIRO’S Solution
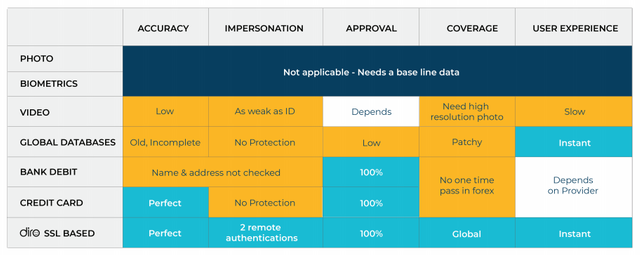
DIRO proposes a unique way of eliminating identity and document fraud. Using its innovative browser plugin a user can capture any webpage along with its SSL certificates to make them tamper resistant and immutable. It can be a driving license, profile page or a utility bill showing the users name, address or date of birth etc. Once the document is captured it does not need to be verified again. The magic is that it works across the web, countries or languages, with no retooling required. The current identity verification is broken as global databases are inconsistent, difficult to update, patchy and without a baseline biometrics data. By placing reliance on human verification on physical or photocopies of Identity documents, the overall system becomes vulnerable to bad actors and as weak as the weakest entry point. Different methods of verifying remote identities are compared below.
New kind of KYC :
Its far easier to verify documents directly captured from Government portals or Utility providers. Since the capture is digital in nature, the accuracy of Optical Character Recognition (OCR) is 100%. The document is classified based on the domain name in the SSL certificate. The authenticity of the domain is programmatically verified from Alexa rankings and traffic. The system checks for the presence of name, date of birth or address. It becomes viable to use Cognitive Robotic Process Automation (CRPA) on this high-quality data for automated decisioning at a very low cost. Users are authenticated remotely by log in and capture of following webpages:
Identity documents (with date of birth) - Passport, Driver’s license, Tax Id, National Insurance, Mark sheets or election card depending on the country.
Address proof (recent utility bill) - Water, Electricity, Gas, Cable, Internet, Landline.
Stronger authentication (optional) - bank statement or credit card statement
Identity linked to wallets across chains (patent pending) :
Once the Identity is established the users may add any wallets or public keys belonging to any blockchain. The effective KYC/AML status can then easily be shared in public without sharing the identity information through a public API. Further, the transactions on public blockchains linked to the wallet can be evaluated for KYCC status without compromising privacy of anyone.
A Trust-less Identity System
Converged directory services : Experience shared contact directories with integrated access management using LDAP. Integrates multiple silos of identities across 1000s of platforms with simple contact app.
Password-less IAM : Eliminate need for hardware tokens or keys with open standards like Federated SSO with SAML, OAuth 2.0, OpenID Connect etc. With applications across multiple domains.
Universal Identities : Self Soverign Identities with seamless Global Pgp and digital signing infrastructure using SPKI and Self-service key retrieval (DPKI).
Eliminate synthetic identities : With the worlds largest passive social graph with SPKI. Further make identities Sybil resistant with Proof-of-life. Use patent pending cryptographic KYC for eliminating Identity fraud.
Automated privacy : Discover and use profile cards to automate privacy across the identity eco-system. Prevent external correlation using contact IDs. Unlock private contextual data from within contacts with cryptography and IAM frictionlessly.
Strong network effect : Creates large scale value through crowd mining and viral stacking. With top Identity use cases and being default dialer app diro maps the entire identity network with just 1% users.
For more information about this project visit :
- Website : https://www.diro.io/
- Whitepaper : https://docs.wixstatic.com/ugd/fae167_26798553a540495d9c8189932e9c088f.pdf
- ANN Thread : https://bitcointalk.org/index.php?topic=3266144.msg34032664#msg34032664
- Telegram : https://t.me/DiroToken
- Twitter : https://twitter.com/DiroLabs
- Facebook : https://www.facebook.com/DiroBlockchain
Bitcointalk profile : https://bitcointalk.org/index.php?action=profile;u=2038051