Greetings Steemit! This time it's not my own work, but I was fascinated by amount of analytics that was used when creating the table. And it's still very interesting and useful.
What, in general, is safe mail?
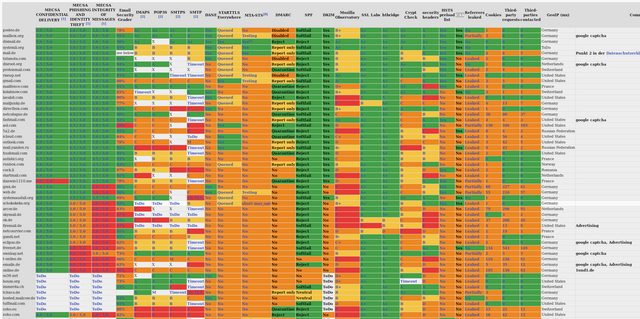
It's hard to designate email services one from others nowadays. Most of them will say that they support important security futures, that they support GDPR, and all such stuff. But in reality - if you want to know that your emailing is 99.9% not leaving any traces after it (and you still can always introduce your own encryption methods!) - read on.
How to ensure?
In general, we have to gather some metrics. In the best way, we should gather this metrics from different sources, and re-check them frequently. This is the only way we could be sure that nothing's changes. Great option here is to use open source software - where each and every change can be traced to git commit. In this case it would be easier to ensure that everything is still safe. So, ...
What are the metrics?
- MECSA - it's European standard on making a safe email service.
- StartTLS - Opportunistic TLS (Transport Layer Security) refers to extensions in plain text communication protocols, which offer a way to upgrade a plain text connection to an encrypted (TLS or SSL) connection instead of using a separate port for encrypted communication. Several protocols use a command named "STARTTLS" for this purpose. It is primarily intended as a countermeasure to passive monitoring.
- DANE / DNSSEC - DNS-based Authentication of Named Entities (DANE) is an Internet security protocol to allow X.509 digital certificates, commonly used for Transport Layer Security (TLS), to be bound to domain names using Domain Name System Security Extensions (DNSSEC).
- MTA-STS - is a mechanism enabling mail service providers (SPs) to declare their ability to receive Transport Layer Security (TLS) secure SMTP connections and to specify whether sending SMTP servers should refuse to deliver to MX hosts that do not offer TLS with a trusted server certificate.
- DMARC - Domain-based Message Authentication, Reporting and Conformance - is an email-validation system designed to detect and prevent email spoofing, the use of forged sender addresses often used in phishing and email spam.
- SPF - Sender Policy Framework is an email authentication method designed to detect forged sender addresses in emails (email spoofing), a technique often used in phishing and email spam.
- DKIM - DomainKeys Identified Mail is an email authentication method designed to detect forged sender addresses in emails, (email spoofing), a technique often used in phishing and email spam.
I still can't understand what all those metrics mean, what should I do?
At first, please, relax. The guy who did the large analytic on the topic of email security already marked green color stuff that's good, yellow - which is so/so, orange - which is problematic and red - as a sign of danger. You might follow the link to review the table and decide if some mail services can suite your needs, depending on the colors. :)
The wonderlink
https://dismail.de/serverlist.html
Links to read
- https://starttls-everywhere.org/faq/
- https://mecsa.jrc.ec.europa.eu/en/technical
- https://github.com/aeris/cryptcheck
The results
In my opinion, the table shows that we should consider using one of this safe email services:
- posteo.de
- mailbox.org
- dismail.de (the creator of the spreadsheet)
- systemli.org
- mail.de
Next five services includes tutanota.com, disroot.org, protonmail.com, riseup.net, and, surprisingly, gmail.com. Probably you should be careful when using them. Others still worth considering, especially if you use own developed encryption.
Hope this article were useful. Please comment on what safe mail service do you use or don't? Skol!
Den Ivanov aka @sxiii from oooooslooooo city