
Here comes a problem for job seekers and recruiters. The attackers are now targeting organizations by impersonating job seeker applications. Reportedly, researchers have found a new phishing campaign delivering the Quasar RAT malware via malicious attachments pretending to be CVs.
Quasar RAT Delivered Via Phishing
Researchers from Cofense have discovered another phishing campaign in the wild delivering Quasar RAT to the victims. Quasar is an open-source remote administration tool for Windows that can act as spyware.
In the phishing campaign detected by the researchers, the attackers impersonate the phishing emails as a job seeker’s application. The email includes a malicious attachment mimicking a resume that actually contains the malware.
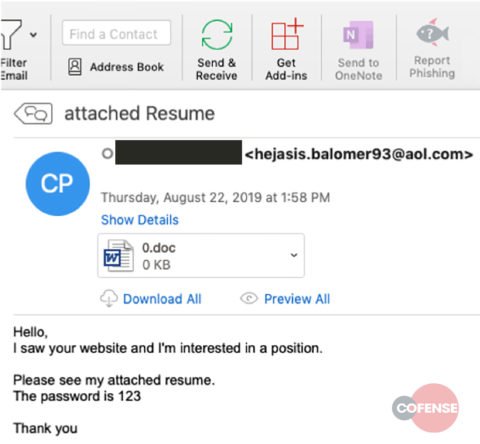
Source: Cofense
As per the email’s content, the recipient must open the attachment using the given password. Upon opening the attachment, the document asks the recipient to enable document editing to open the seemingly protected document.
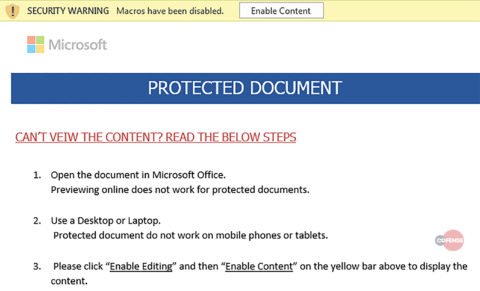
Source: Cofense
Once enabled, the document then executes the malware embedded within. The researchers have presented a detailed technical analysis in their blog post.
Capability To Evade Detection
While the overall malware execution in this phishing campaign seems usual, what makes it worth noting is its ability to escape security checks.
At first, the requirement for a simple password as ‘123’ to open the attachment makes the document non-suspicious. Even if the system opens the document, it will trigger no malicious activity (as it requires enabling editing feature).
Additionally, if a system opens the document and begins analyzing macros, it will fail to do so owing to a system crash for excessive memory consumption due to heavy ‘garbage code’. As elaborated by the researchers,
This is likely an intentional effect by the threat actor in the form of more than 1200 lines of garbage code that appears to be base64 encoded. Forcing the script to attempt to decode the garbage strings causes, in all likelihood, a crash due to the magnitude of decoding required.Still, if the system has enough memory to allocate to the process, the resulting content would still lack the payload URL. The attackers have masked the information including parts of payload URL as metadata of embedded objects.
Lastly, the execution of malware also takes place in a manner to evade detection by downloading a ‘Microsoft Self Extracting executable’ which then extracts the 410MB Quasar RAT binary. This unusually large file size also contributes to escaping security checks. As explained by the researchers,
By using an artificially large file size the threat actors make sharing information difficult while also causing problems for automated platforms that attempt to statically analyze the content.This malware campaign appears specifically aimed at organizations by exploiting job applications. Thus, the relevant recruitment personnel in every organization should remain vigilant while handling emails, particularly during active recruitment phases.
Let us know your thoughts in the comments.
Posted from my blog with SteemPress : https://latesthackingnews.com/2019/08/27/attackers-target-company-recruitment-processes-with-phoney-job-applications-loaded-with-quasar-rat/
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://latesthackingnews.com/2019/08/27/attackers-target-company-recruitment-processes-with-phoney-job-applications-loaded-with-quasar-rat/
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit