Security Researchers have discovered a vulnerability in PGP or S/MIME Email Encryption methods which is currently being called EFAIL that exposes the encrypted emails in plain text even all the messages that have been transferred in the past.
“Email is no longer a secure communication medium,” Sebastian Schinzel, a professor of computer security at Germany’s Münster University of Applied Sciences, told the German news outlet Süddeutschen Zeitun. The vulnerability was reported by the Electronic Frontier Foundation on Monday Morning and the details were updated on the internet at 6 AM ET today. A group of people from news embargo are saying to stop using PGP.
The Researchers are currently saying that there is no immediate fix available for this vulnerability.
"The EFAIL attacks exploit vulnerabilities in the OpenPGP and S/MIME standards to reveal the plaintext of encrypted emails. In simple terms, EFAIL abuses active content of HTML emails, for example externally loaded images or styles, to exfiltrate plaintext through requested URLs. To create these exfiltration channels, the attacker first needs access to the encrypted emails, for example, by eavesdropping on network traffic, compromising email accounts, email servers, backup systems or client computers. The emails could even have been collected years ago."
"The attacker changes an encrypted email in a particular way and sends this changed encrypted email to the victim. The victim’s email client decrypts the email and loads any external content, thus exfiltrating the plaintext to the attacker."
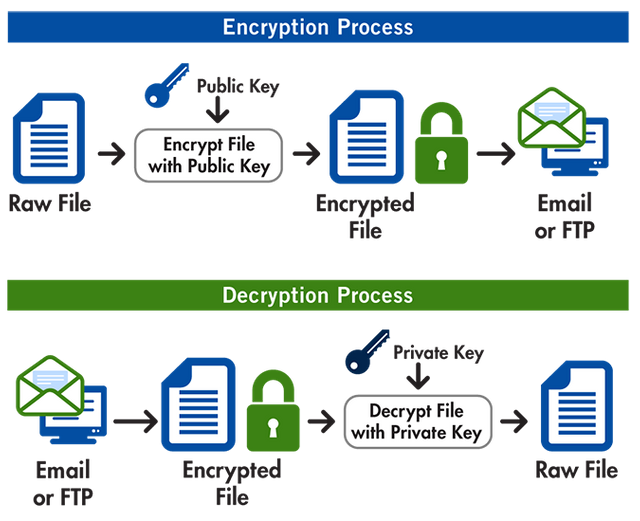
PGP (Pretty Good Privacy) is an encryption algorithm that is considered as the Gold Standard for the security of the Emails which was first developed in 1991. The PGP encryption became the standard of the market in the 21st century but after this breach, there will be a significant reduction of clients taking advantage of this algorithm.
“They figured out mail clients which don’t properly check for decryption errors and also follow links in HTML emails. So the vulnerability is in the mail clients and not in the protocols. In fact, OpenPGP is immune if used correctly while S/MIME has no deployed mitigation,” GNU Privacy Guard said on Twitter.
Take your time to comment on this article.
Posted from my blog with SteemPress : https://latesthackingnews.com/2018/05/15/emails-no-longer-secure-critical-flaw-found-in-pgp/