Public Key Cryptography
Public key cryptography utilizes hashing algorithms agreed upon by all parties involved. Popular algorithms are SHA-128, SHA-256, SHA-512, and so on where SHA stands for “Standard Hashing Algorithm.” Essentially any arbitrary length of data (bits in the form of 1s and 0s) will follow computational rules which shorten it down (or expand it) to a certain number of bits designated by the number following the “SHA-”. While it is relatively simple for a machine to compute in this direction it is theoretically impossible to reverse engineer the original data from the hashed result.

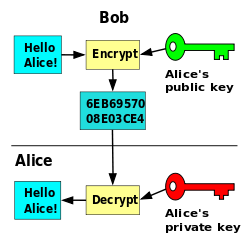
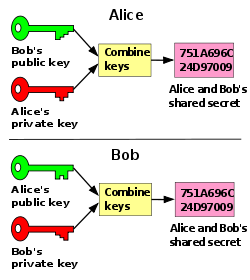
In a typical key exchange scheme, each party generates a public/private key pair and shared their own public key. After obtaining an authentic copy of one another's public key, Alice and Bob can compute a shared secret offline. The shared secret can be used, for instance, as the key for a symmetric cipher.
Bitcoin Blockchain
Bitcoin uses the calculation of SHA-256 as a proof-of-work to mint coins to the miner of that result which ‘finds the solution’ in a game which gets more difficult as more try to solve the riddle resulting in an average goal block-time of 10 minutes although it is still computationally random so we’ve seen 3 in a minute and 5 in two as well as witnessed three thirty-minute block times in a row. Essentially a distributed trustless ledge system not very much unlike a simple spreadsheet.
Ethereum Smart Contracts
In late 2013 Vitalik Buterin made history by launching a crowdsale paid for by Bitcoin within a Bitcoin contract. Enter Ethereum. The Bitcoin earned during the crowdsale would fund the Ethereum Foundation who would develop the ‘world computer,’ a decentralized programming language for Bitcoin-like transactions with the aim to not indefinitely waste excess energy in a proof-of-work algorithm. If Bitcoin is likened to a simple spreadsheet than Ethereum can be illustrated as Microsoft Excel complete with the Visual Basic for Applications turing complete scripting language to enable ever more complex cell computations.
The DAO
While the Distributed Autonomous Organization crowdsale was a record-breaking success it’s crown jewel, the split(), which boasted a no-risk investment if there ever was one, ended up splitting its Achilles tendon. The Daohub campaign brought in over $160 Million which ended up funding what became dubbed “The DAO Heist” where we experienced that on-the-fly contingency planning requires social mechanisms. In this case that was made possibly only by the relative celebrity status of the developers of the DAO 1.0 framework, their close relationship with Vitalik Buterin of Ethereum and his sole identity which prompted the exchanges’ willingness to restrict trading based on his consultation and later the the miners of the Ethereum blockchain would 51% attack their own network to reclaim those tokens.
‘“DAO 2.0 will iron out this and many weaknesses in the first real DAO. DAO is obviously a largely sought after technological goal considering the revenue it brought in. This will not stop.” @jeffanthony and the rest of the community are all looking ahead to the next solution.’
Synereo-as-a-Solution
Since social mechanisms are the natural way humans operate we will generally respond best when we act in a socially familiar way. Any sustainable DAO would have to integrate “escape hatch” social contracts which we are assured can be best handled by Synereo. A default contingency planning mechanism, which I codename “S.A.S. Mode,” could have stopped the leakage of many of the funds exploited from The DAO to the point that it would have been a decent bug bounty and we could move on from there.
Consider, as well, that much of the issues hindsightedly noticed as a direct result of The DAO experiment involved centralized decisionmaking. The code review, discussion in slack during testing, questions strategically ignored or misdirected to the back-burner, and a forum team whom did not know what they were getting into -- all centrally handled parts of the decisionmaking process independent of one another. Once an attack affected all parties there was not yet a system in place to handle that, in fact all parties had not been able to do a whole lot of anything even with the systems which were in place as the mass was mostly entropied within exchanges.
Synereo can solve not only the central communications issue as it aims to be “The Decentralized Social Network” but can act as oracle solutions between blockchains which also perfectly positions itself within the domain of content management, other resource management, and the killer-app private-key/persona management.
References:
Public Key Cryptography, Wikipedia (retrieved July 12, 2016)
Ethereum Whitepaper, Vitalik Buterin (2013) https://github.com/ethereum/wiki/wiki/White-Paper
Distributed Automomous Organizations, Slock.it UG (2016) https://download.slock.it/public/DAO/WhitePaper.pdf
The DAO Heist FAQ, ConsenSys (retreived July 15, 2016) https://media.consensys.net/2016/06/24/the-dao-heist-faq/
DAO Moving Forward: A Community Perspective, Patrick Maguire (July 6, 2016) https://blog.daohub.org/dao-moving-forward-a-community-perspective-22f15b72d0c4
Smart Contract Escape Hatches Bill Marino (2016) http://hackingdistributed.com/2016/06/22/smart-contract-escape-hatches/
Congratulations @jeff-anthony! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Do not miss the last post from @steemitboard:
Vote for @Steemitboard as a witness to get one more award and increased upvotes!
Downvoting a post can decrease pending rewards and make it less visible. Common reasons:
Submit